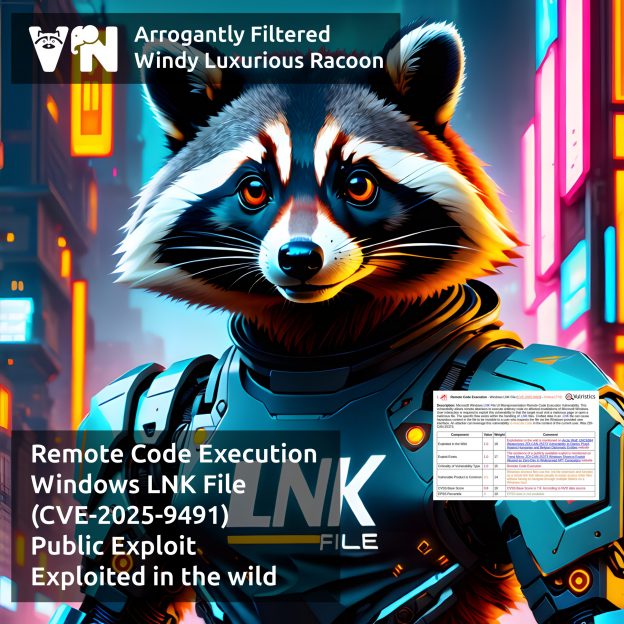
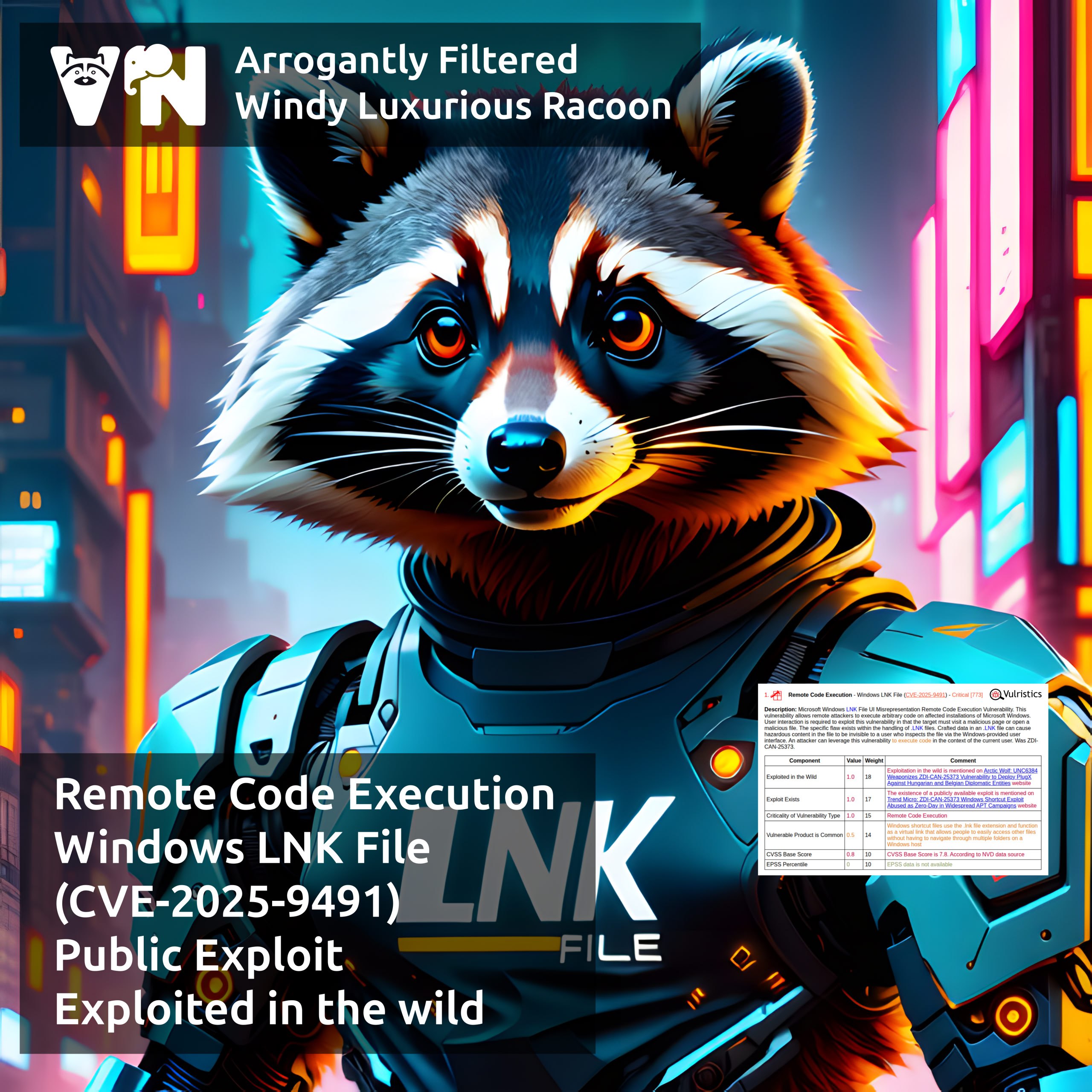
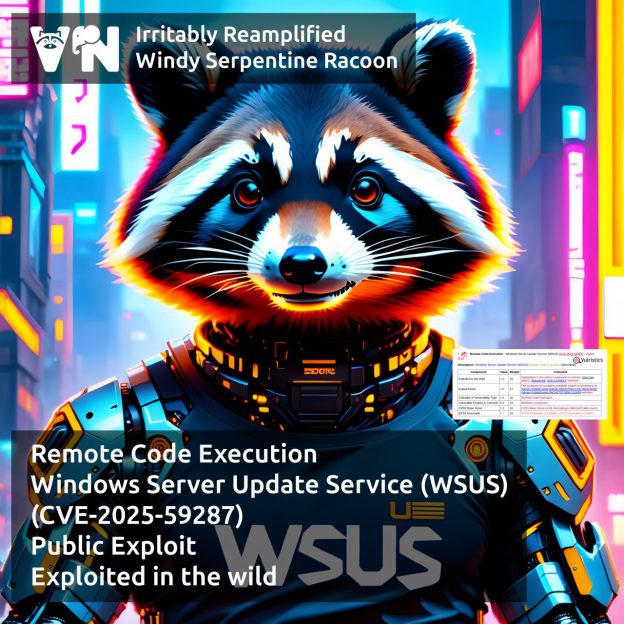
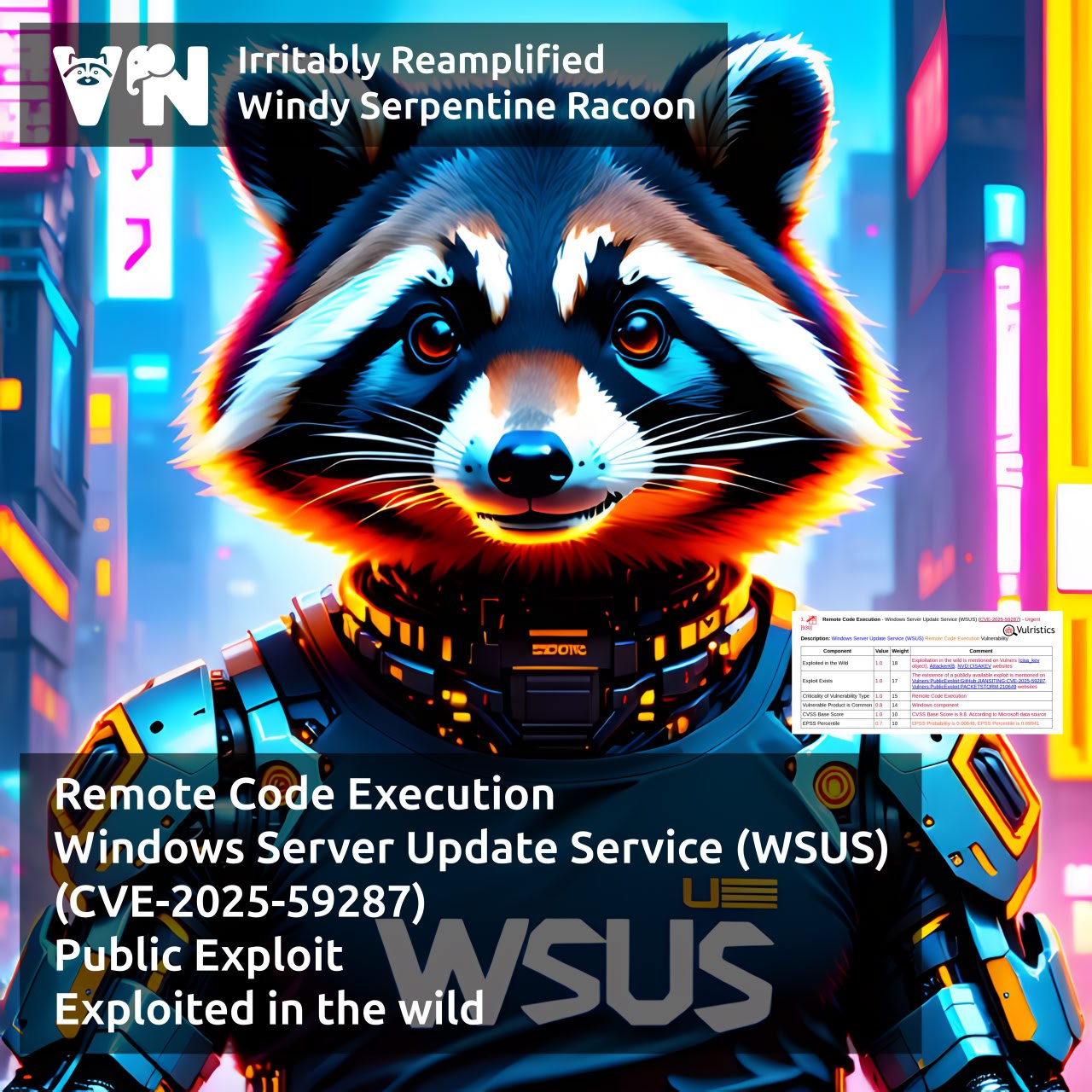
About Elevation of Privilege – Windows Remote Access Connection Manager (CVE-2025-59230) vulnerability. A vulnerability from the October Microsoft Patch Tuesday. The Windows Remote Access Connection Manager (RasMan) service is a core Windows component that manages dial-up and Virtual Private Network (VPN) connections, ensuring secure communication between a computer and remote networks. An access control flaw in the RasMan service could allow an authenticated attacker to elevate privileges to the SYSTEM level.
👾 On October 14, Microsoft reported signs of the vulnerability being exploited in the wild. On October 22, it was added to the CISA KEV catalog. No further details about the attacks have been disclosed so far.
🛠 No public exploits have been observed yet.