Tenable SecurityCenter and its API. SecurityCenter is an enterprise level vulnerability management product of Tenable Network Security. As the name implies, the it is designed to be the center of Tenable security infrastructure. SecurityCenter takes data from other Tenable products: Passive Vulnerability Scanner (PVS), Log Correlation Engine (LCE), Nessus, and provides a powerful GUI interface for searching and reporting. Sounds familiar? Well, yes, it is something like SIEM, but with a strong emphasis on Vulnerability Management.

I’ve took this screenshot from SC5 video presentation in Spanish.
In this post, I certainly will not fully cover SC functionality and all the features of its API. I just would like to pay tribute to a convenient asset mechanism of SecurityCenter and show very basic operation of SecurityCenter API: retrieving the results of the vulnerability scanning (as I did it for Nessus in “Retrieving scan results through Nessus API“).
As in the Nessus case, to scan something with SecurityCenter you need to set a list of hosts or range of ip-addresses. But in SecurityCenter, you can also very easily make groups of hosts (Assets), which will be updated dynamically according to the fresh scan results. For example, Windows hosts, hosts with detected OpenSSL vulnerabilities, hosts with expired SSL certificate. You can do this with just a few clicks.
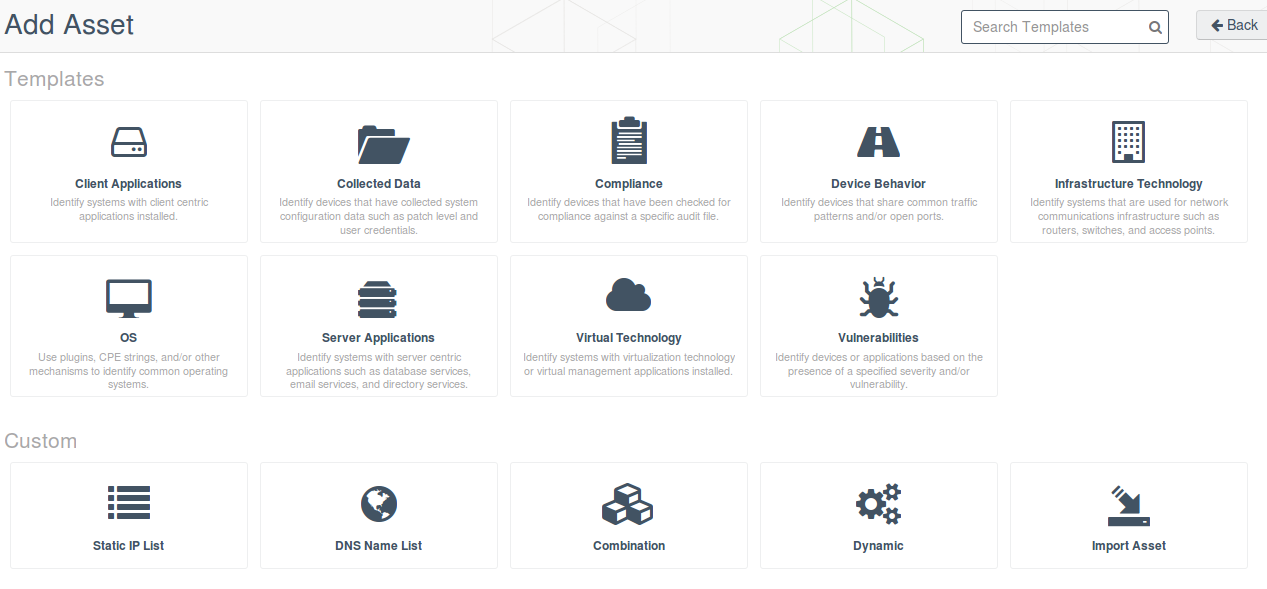
Tenable offers a variety of templates for creating assets list:
- Client Applications – Identify systems with client centric applications installed.
- Collected Data – Identify devices that have collected system configuration data such as patch level and user credentials.
- Compliance – Identify devices that have been checked for compliance against a specific audit file.
- Device Behavior – Identify devices that share common traffic patterns and/or open ports.
- Infrastructure Technology – Identify systems that are used for network communications infrastructure such as routers, switches, and access points.
- OS – Use plugins, CPE strings, and/or other mechanisms to identify common operating systems.
- Server Applications – Identify systems with server centric applications such as database services, email services, and directory services.
- Virtual Technology – Identify systems with virtualization technology or virtual management applications installed.
- Vulnerabilities – Identify devices or applications based on the presence of a specified severity and/or vulnerability.
If no template suit you, there are more powerful tools (Dynamic) or it may sometimes be necessary to make just a static list (dns/ip):
- Static IP List
- DNS Name List
- Combination
- Dynamic
- Import Asset
Nessus Template Scanning policies are in fact some variation of Advanced Scan policy (see “Tenable Nessus: registration, installation, scanning and reporting“). In the same way all SecurityCenter Asset templates are in fact variations of the Dynamic Asset, which allows you to specify very tricky nested criterias.
You can just view assets as a flat list and do various other things. For example, easily make a scan task for them or display information (only for particular assets, not all the systems) in convenient dashboards.
SecurityCenter graphical tools are very comfortable and beautiful. However, it is clear how they actually work. In fact it is the same Nessus scan results, just presented in a different form (not to taking into consideration PVS and LCE). You can make all the same by analyzing raw Nessus scan repoкts with your own scripts. Making some scripting might make sense if you, for example, cant use SecurityCenter for the all your hosts, because it is too expansive, and scan most critical hosts with SC, and the others with separate Nessus,
Let’s see how to retrieve the raw scan results from SecurityCenter with API. SecurityCenter API description is publicly available here: https://docs.tenable.com/sccv/api/index.htm. You do not have to pay anything extra to use it.

Nessus and SecurityCenter are the products of one company. It would be logical to see some API very similar to the Nessus API. But not really. In fact, it is all so different. It seems that these APIs was made by completely different development teams.
You can see the difference right from the authorization. To authorize in you need Security Manager account. We need to get the session key and cookies.
$ curl -s -k -X POST -d '{"username":"sc_user","password":"sc_password"}' -c sc_cookie.txt https://sc.corporation.com/rest/token
{"type":"regular","response":{"token":1130200994,"unassociatedCert":"false"},"error_code":0,"error_msg":"","warnings":[],"timestamp":1470939046}
Here is what is contained in sc_cookie.txt, if you’re curious:
$ cat sc_cookie.txt # Netscape HTTP Cookie File # http://curl.haxx.se/docs/http-cookies.html # This file was generated by libcurl! Edit at your own risk. sc.corporation.com FALSE / TRUE 0 TNS_SESSIONID bf4469c10e131108b1de0a1f4a66487e
For each request, you should add session key to the header and use cookie file.
Now we can get the list of scans. In fact, almost all of the API requests are something like “show me this big table.” By default, SC doesn’t show all of the fields. You can specify which fields you want to see in parameter fields of a particular GET-request. In order to select a scan interested for us, we need these fields: name, description, status and finishTime.
curl -s -k -X GET -H "X-SecurityCenter: 1130200994" -H 'Content-Type: application/json' -b sc_cookie.txt https://sc.corporation.com/rest/scanResult?fields=name,description,status,finishTime | python -m json.tool
{
"error_code": 0,
"error_msg": "",
"response": {
"manageable": [
{
"description": "",
"finishTime": "1468491230",
"id": "1201",
"name": "LONDON_USERS",
"status": "Completed"
},
{
"description": "",
"finishTime": "1468679415",
"id": "1104",
"name": "PARIS_USERS",
"status": "Completed"
},
...
{
"description": "",
"finishTime": "1470236912",
"id": "1174",
"name": "LONDON_SERVERS",
"status": "Completed"
}
],
"usable": [
{
"description": "",
"finishTime": "1468491230",
"id": "1201",
"name": "LONDON_USERS",
"status": "Completed"
},
{
"description": "",
"finishTime": "1468679415",
"id": "1104",
"name": "PARIS_USERS",
"status": "Completed"
},
...
{
"description": "",
"finishTime": "1470236912",
"id": "1174",
"name": "LONDON_SERVERS",
"status": "Completed"
}
]
},
"timestamp": 1470939236,
"type": "regular",
"warnings": []
}
As you can see, there is a flat list of all scans not grouped in any way. We can select the scan by the name and timestamp when it was completed. And we don’t need to get some history_id, like we did in Nessus, or something like that. Moreover, we do not even have to wait until report file will be ready for download. Isn’t it cool?
$ curl -s -k -X POST -H "X-SecurityCenter: 1130200994" -H 'Content-Type: application/json' -b sc_cookie.txt https://sc.corporation.com/rest/scanResult/1201/download > 1201.zip
$ unzip 1201.zip
Archive: 1201.zip inflating: 1201.nessus
This file is in the same Nessus v2 report format.
cat 1201.nessus | head
<?xml version="1.0" ?> <NessusClientData_v2> <Policy><policyName>CREDENTIAL_SCAN</policyName> <Preferences><ServerPreferences><preference><name>max_simult_tcp_sessions</name> <value>unlimited</value> </preference> <preference><name>use_mac_addr</name> <value>no</value> </preference> <preference><name>sc_version</name>
Thus, all of the scripts that you used to analyze Nessus scans will work for scans reports retrieved from SecurityCenter without any modifications.

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.

Pingback: Qualys Vulnerability Management GUI and API | Alexander V. Leonov
Pingback: New Vulners.com services for Linux Security Audit and Vulnerability Alerting | Alexander V. Leonov
I tried the command to obtain my token using my username, password, and /rest/token and it didn’t work for me. I get back:
{“type”:”regular”,”response”:””,”error_code”:13,”error_msg”:”This request is not
properly formatted.”,”warnings”:[],”timestamp”:1478642237}
Hello Janusz! It is probably because WordPress changes quotation marks in the examples by default. My fault, I forgot to uses <code> to suppress it. Fixed it now. Could you try it once again?
Alexander,
Outside the use of the analysis call, is there a way for the API to pull and download existing reports results?
Hello Omar,
Did you mean standard SecurityCenter reports, such as “Critical and Exploitable Vulnerabilities Report”? I have not worked with them a lot. To use them you need to use “rest/report” API call not documented in official manual.
Pingback: Custom Vulnerability Management Reports | Alexander V. Leonov
Pingback: Seccubus installation and GUI overview | Alexander V. Leonov
Pingback: ZeroNights16: Enterprise Vulnerability Management | Alexander V. Leonov
Pingback: Installing Nessus for SecurityCenter on laptop | Alexander V. Leonov
Pingback: Tenable Nessus: registration, installation, scanning and reporting | Alexander V. Leonov
Pingback: Tracking software versions using Nessus and Splunk | Alexander V. Leonov
I want to get the all the vulnerability List for every vulnerability summary in JSON format using curl command. Could you please help me with that?
Pingback: Parsing Nessus v2 XML reports with python | Alexander V. Leonov
I have a requirement – Pull the Vulnerability data from Tenable.io into Security Center, Can you help me in this regard.
-Thanks
Hi Raman! API of Tenable.ai is very similar to Nessus API. So, you can see post “Retrieving scan results through Nessus API”. It’s possible to import scan results to SecurityCenter in Nessus V2 XML format manually, but I haven’t tried to do it with API.
I would imagine something like this?
curl -s -k -X GET -H “X-SecurityCenter: XXXXXXXXXXX” -H ‘Content-Type: application/json’ -b sc_cookie.txt https://1.1.1.1/rest/scanResult/import
{
“filename” : “VS_foo.nessus”,
“repository” : {
“id” : “00000”
},
“classifyMitigatedAge” :”0″,
“dhcpTracking” :”false”,
“scanningVirtualHosts” :”false”
}
But i get an error:
{“type”:”regular”,”response”:””,”error_code”:10,”error_msg”:”Resource is not supported.”,”warnings”:[],”timestamp”:1541427911}
Thoughts on what I could be doing wrong?
Pingback: My short review of “IDC Worldwide Security and Vulnerability Management Market Shares 2016” | Alexander V. Leonov
Have you worked with Tenable and ACAS? I would be interested in knowing this
Hi!
Have you tried using this commands via a java application? Do you have any advice on that?