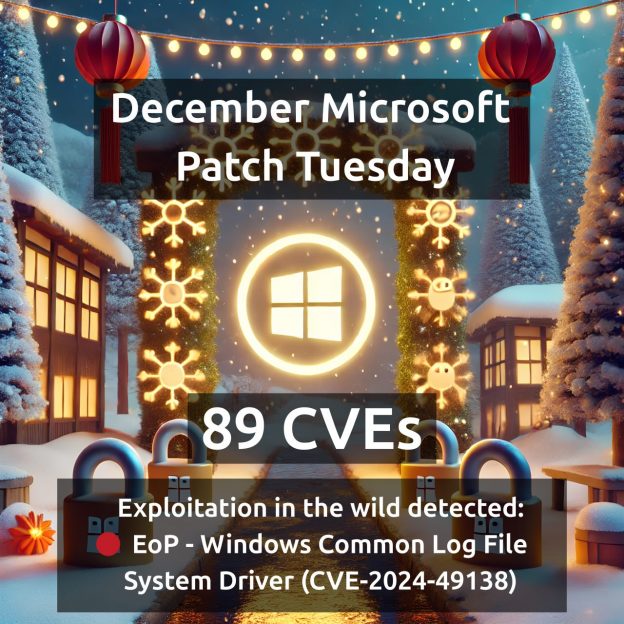
December Microsoft Patch Tuesday. 89 CVEs, of which 18 were added since November MSPT. 1 vulnerability with signs of exploitation in the wild:
🔻 EoP – Windows Common Log File System Driver (CVE-2024-49138). There are no details about this vulnerability yet.
Strictly speaking, there was another vulnerability that was exploited in the wild: EoP – Microsoft Partner Network (CVE-2024-49035). But this is an already fixed vulnerability in the Microsoft website and I’m not even sure that it was worth creating a CVE. 🤔
For the remaining vulnerabilities, there are no signs of exploitation in the wild, nor exploits (even private ones).
I can highlight:
🔹 RCE – Windows LDAP (CVE-2024-49112, CVE-2024-49127)
🔹 RCE – Windows LSASS (CVE-2024-49126)
🔹 RCE – Windows Remote Desktop Services (CVE-2024-49106 и ещё 8 CVE)
🔹 RCE – Microsoft MSMQ (CVE-2024-49122, CVE-2024-49118)
🔹 RCE – Microsoft SharePoint (CVE-2024-49070)