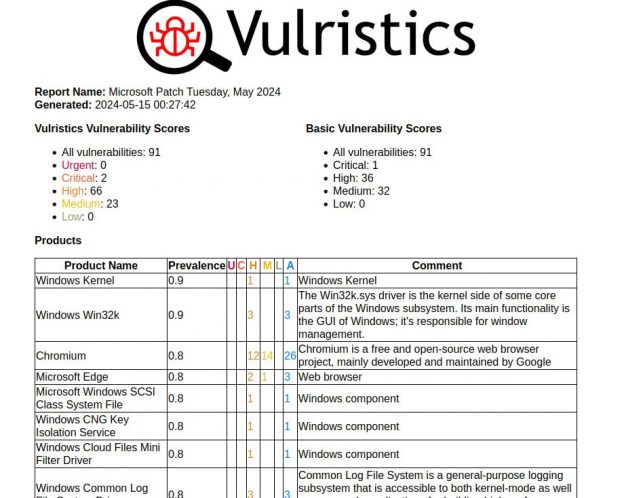
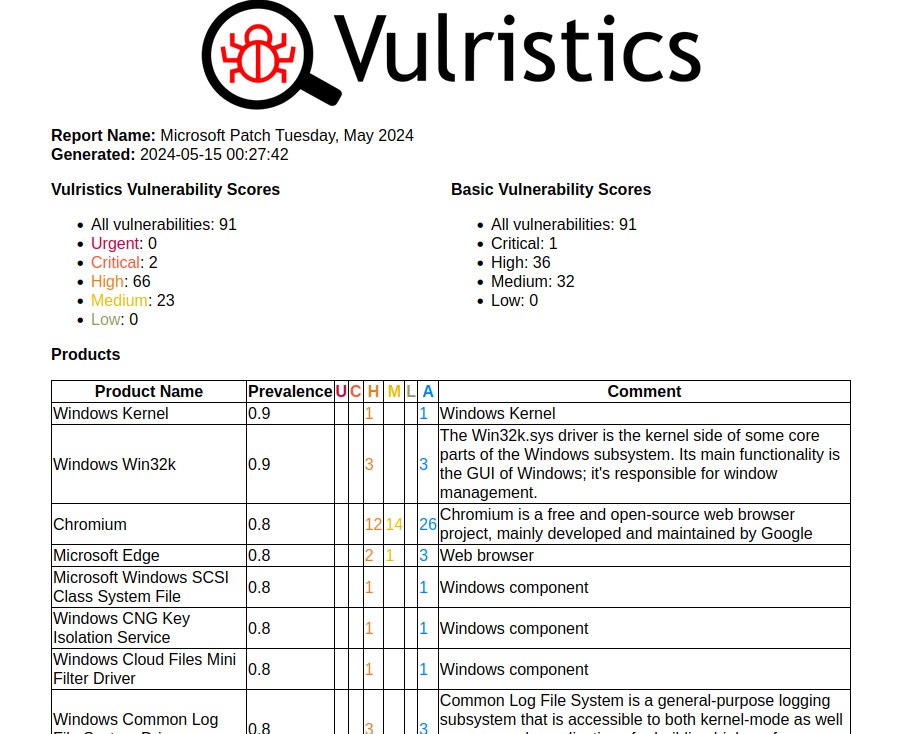
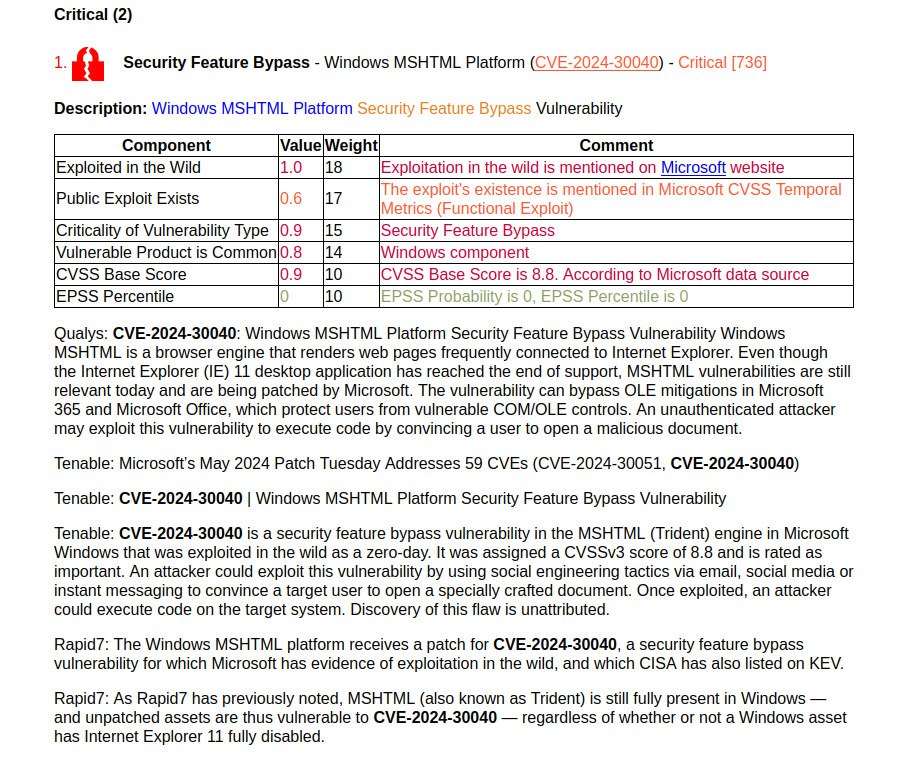
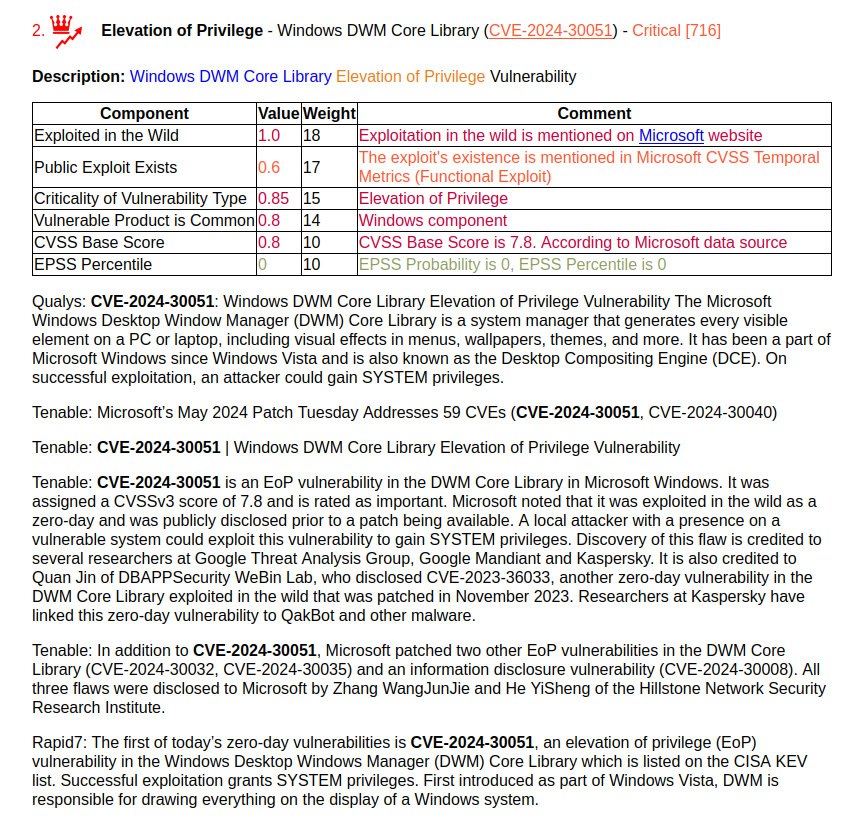
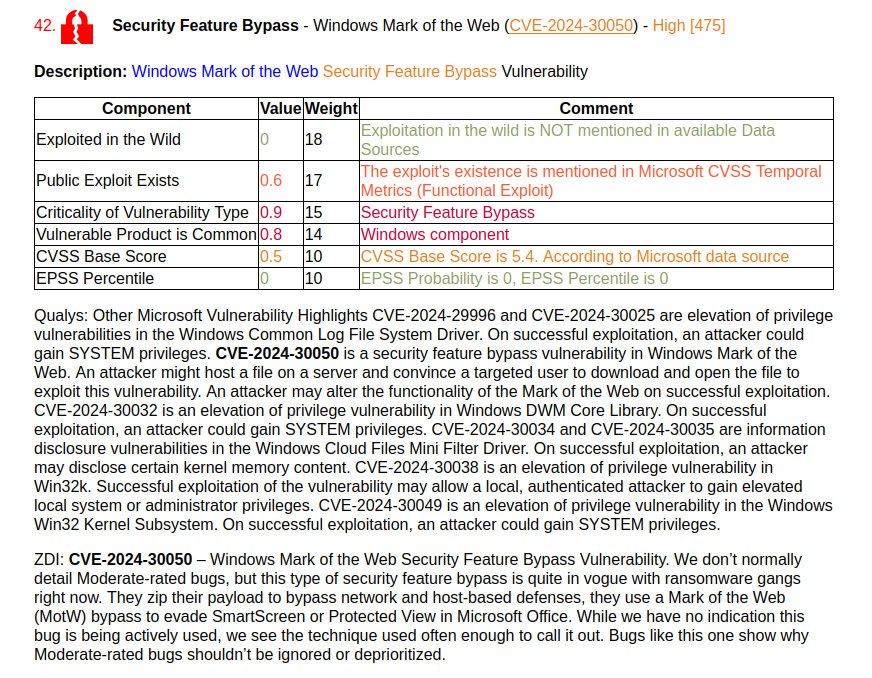
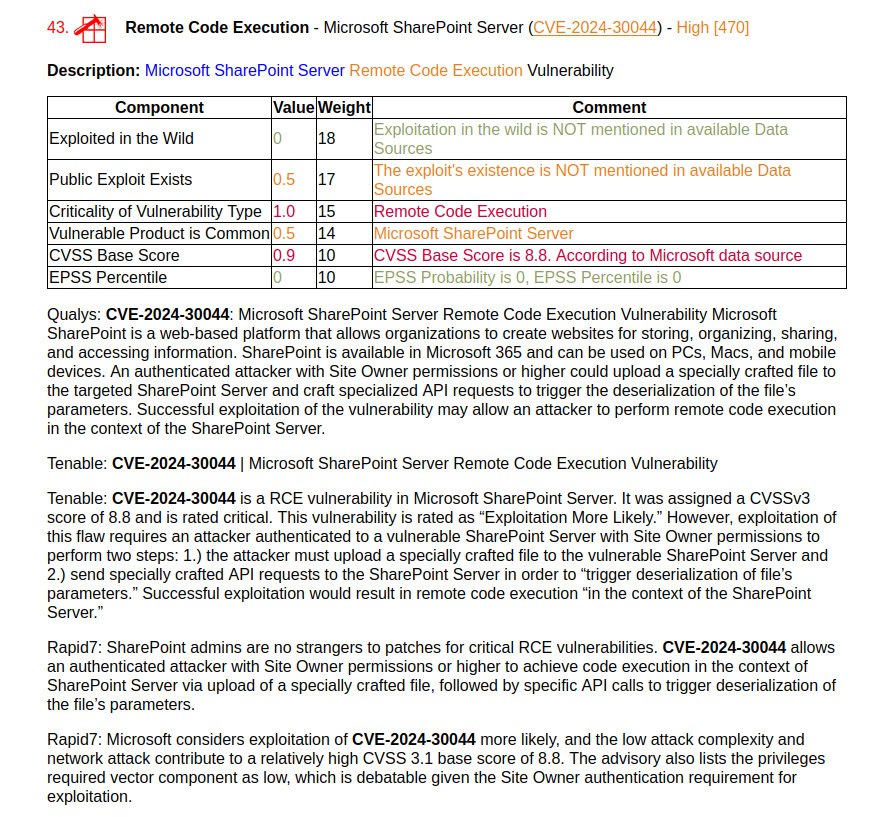
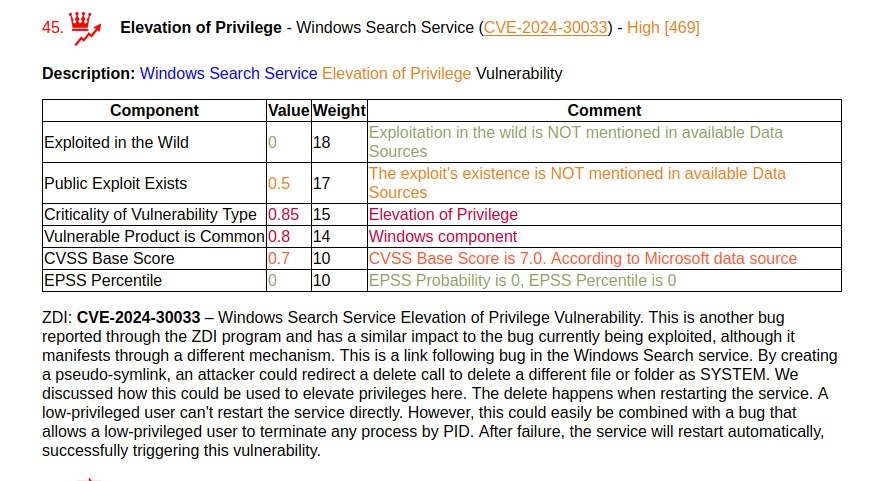
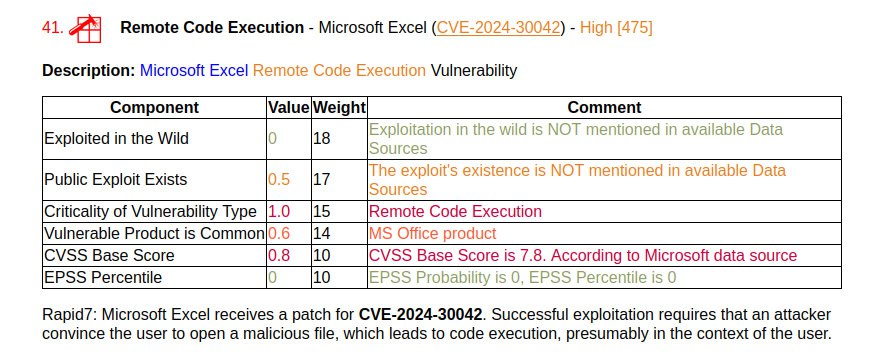
January Microsoft Patch Tuesday. A total of 114 vulnerabilities, twice as many as in December. There is one vulnerability with evidence of in-the-wild exploitation:
🔻 InfDisc – Desktop Window Manager (CVE-2026-20805)
There are also two vulnerabilities with public exploits:
🔸 RCE – Windows Deployment Services (CVE-2026-0386)
🔸 EoP – Windows Agere Soft Modem Driver (CVE-2023-31096)
Other notable vulnerabilities include:
🔹 RCE – Microsoft Office (CVE-2026-20952, CVE-2026-20953), Windows NTFS (CVE-2026-20840, CVE-2026-20922)
🔹 EoP – Desktop Windows Manager (CVE-2026-20871), Windows Virtualization-Based Security (VBS) Enclave (CVE-2026-20876)
🔹 SFB – Secure Boot Certificate Expiration (CVE-2026-21265)
Also noteworthy, reported by Positive Technologies:
🟥 EoP – Windows Telephony Service (CVE-2026-20931)
🗒 Full Vulristics report
На русском