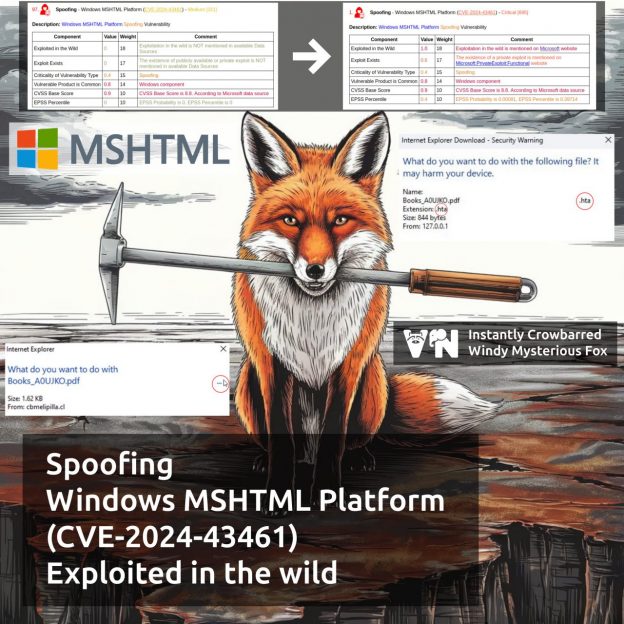
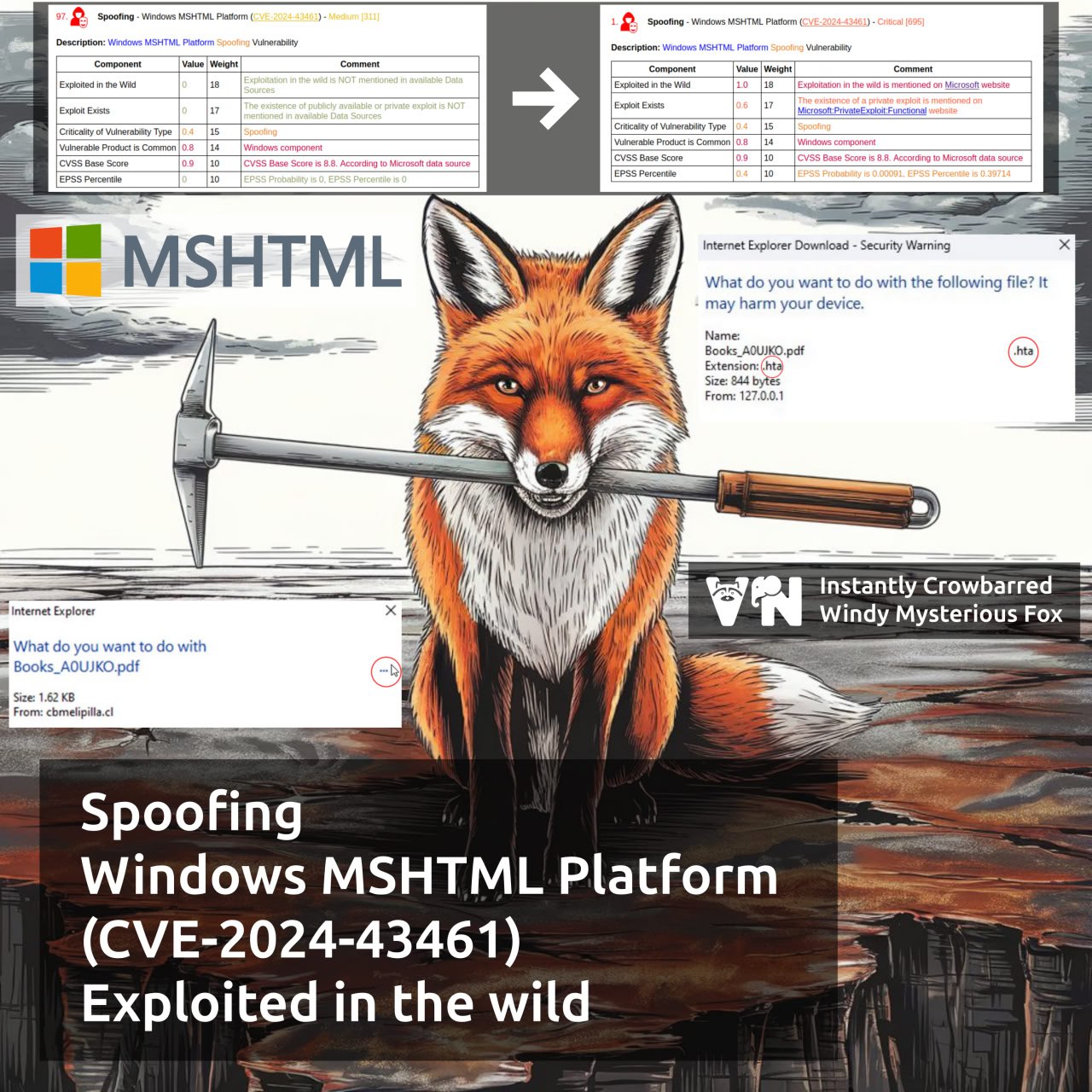
February Microsoft Patch Tuesday. A total of 55 vulnerabilities, half as many as in January. There are as many as six (❗️) vulnerabilities being exploited in the wild:
🔻 SFB – Windows Shell (CVE-2026-21510)
🔻 SFB/RCE – Microsoft Word (CVE-2026-21514)
🔻 SFB – MSHTML Framework (CVE-2026-21513)
🔻 EoP – Windows Remote Desktop Services (CVE-2026-21533)
🔻 EoP – Desktop Window Manager (CVE-2026-21519)
🔻 DoS – Windows Remote Access Connection Manager (CVE-2026-21525)
There is also one vulnerability with a public exploit:
🔸 DoS – libjpeg (CVE-2023-2804)
Among the remaining vulnerabilities, the following stand out:
🔹 RCE – Windows Notepad (CVE-2026-20841)
🔹 Spoofing – Outlook (CVE-2026-21511)
🔹 EoP – Windows Kernel (CVE-2026-21231, CVE-2026-21239, CVE-2026-21245), Windows AFD.sys (CVE-2026-21236, CVE-2026-21238, CVE-2026-21241)