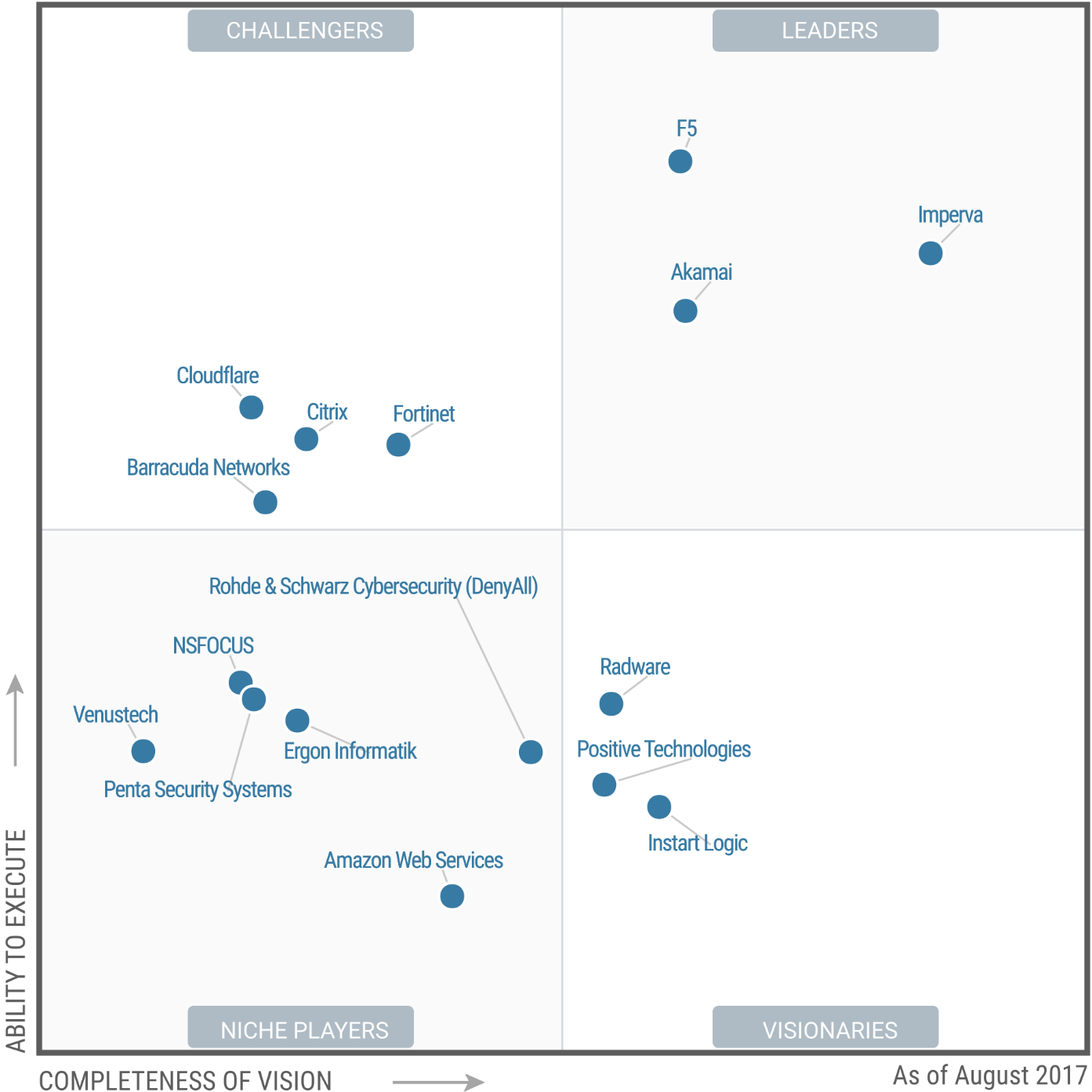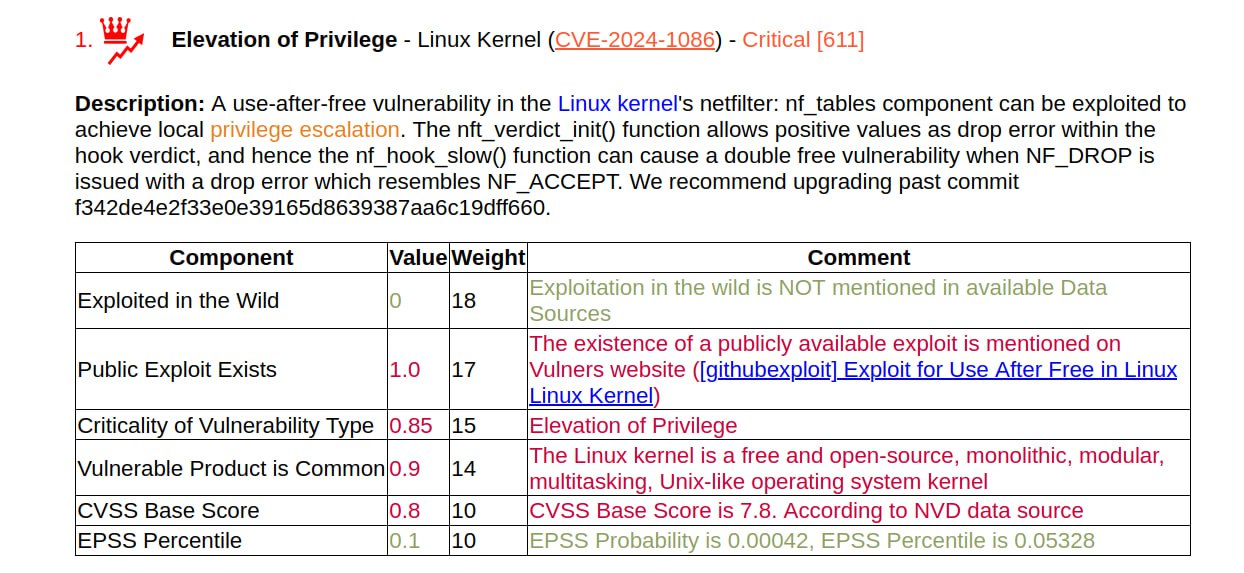
For the January Elevation of Privilege (Local Privilege Escalation) – Linux Kernel (CVE-2024-1086), the write-up and PoC were released on March 26. The video demo for the script looks impressive: they run the script as a regular user and after a couple of seconds they get a root shell. According to the author, the exploit works with most Linux kernels between versions 5.14 and 6.6, including Debian, Ubuntu and KernelCTF.
🔻 The exploit requires kconfig CONFIG_USER_NS=y; sh command sysctl kernel.unprivileged_userns_clone = 1; kconfig CONFIG_NF_TABLES=y. The author writes that this is the default for Debian, Ubuntu, and KernelCTF, and for other distributions it is necessary to test it.
🔹 The exploit does not work with kernels v6.4> with kconfig CONFIG_INIT_ON_ALLOC_DEFAULT_ON=y (including Ubuntu v6.5)
NSFOCUS writes that Redhat is also vulnerable. 🤷♂️