Impressions from PHDays Fest. 🏟
🔹 The scale was just insane. You walk and walk – and there’s action everywhere, and all of it is PHDays, every bit of it. 👀 It totally blew my mind, I saw just a tiny fraction of everything that was going on. 🤯🙂
🔹 In the public area, I was impressed by the university pavilions – BMSTU, HSE, MSU, ITMO, and Polytech. I see a lot of potential here for smaller activities, like alumni talks. I’ll try to be part of something like that next year. 😇
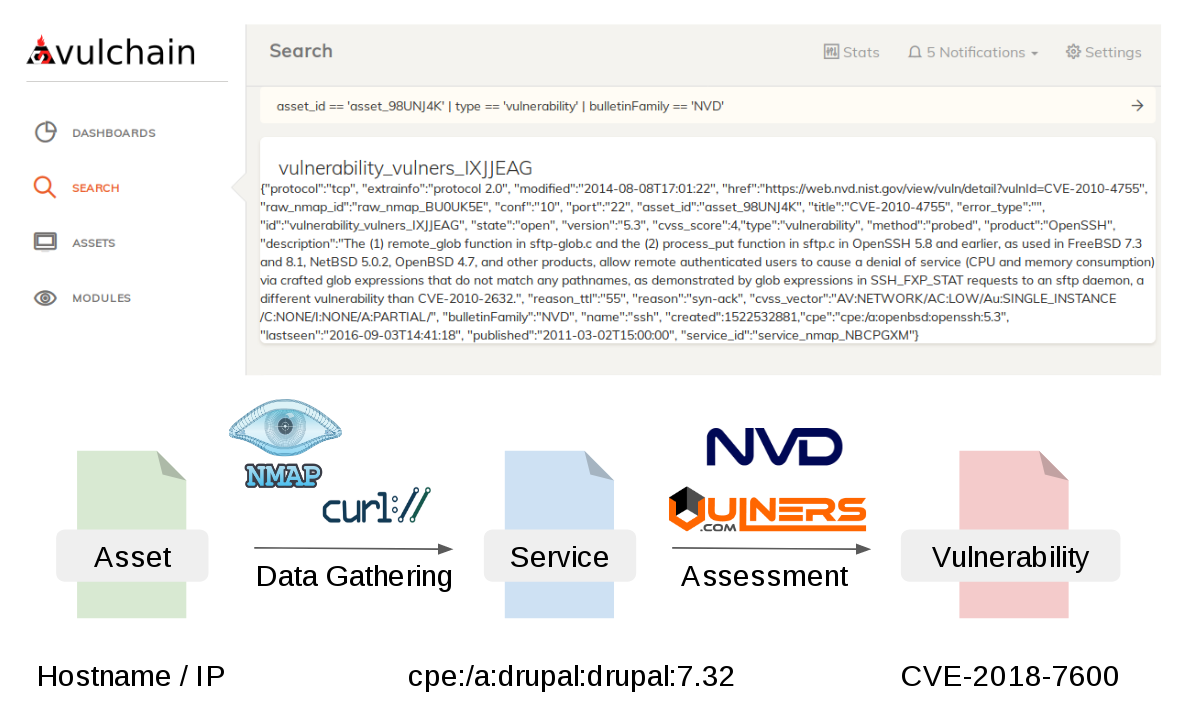
🔹 In the ticketed-access exhibition area, I mostly hung out at Security Vision booth. Great folks – I learned a lot about their VM product; will share insights soon. 😉
🔹 As for my own talk – everything was really well organized. 👍 Huge thanks to everyone who came and asked questions! 🙏🔥
🔹 I caught other talks in bits and pieces – planning to watch the full recordings later.
Thanks to the organizers! It was awesome! See you next year! 🎉🙂