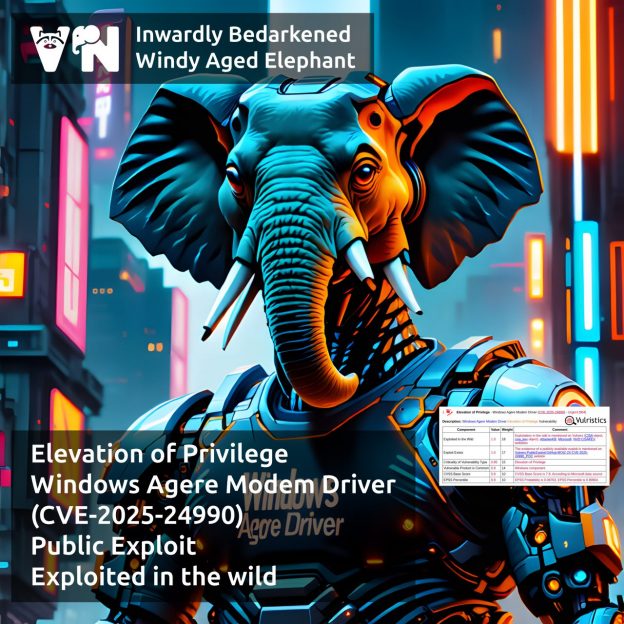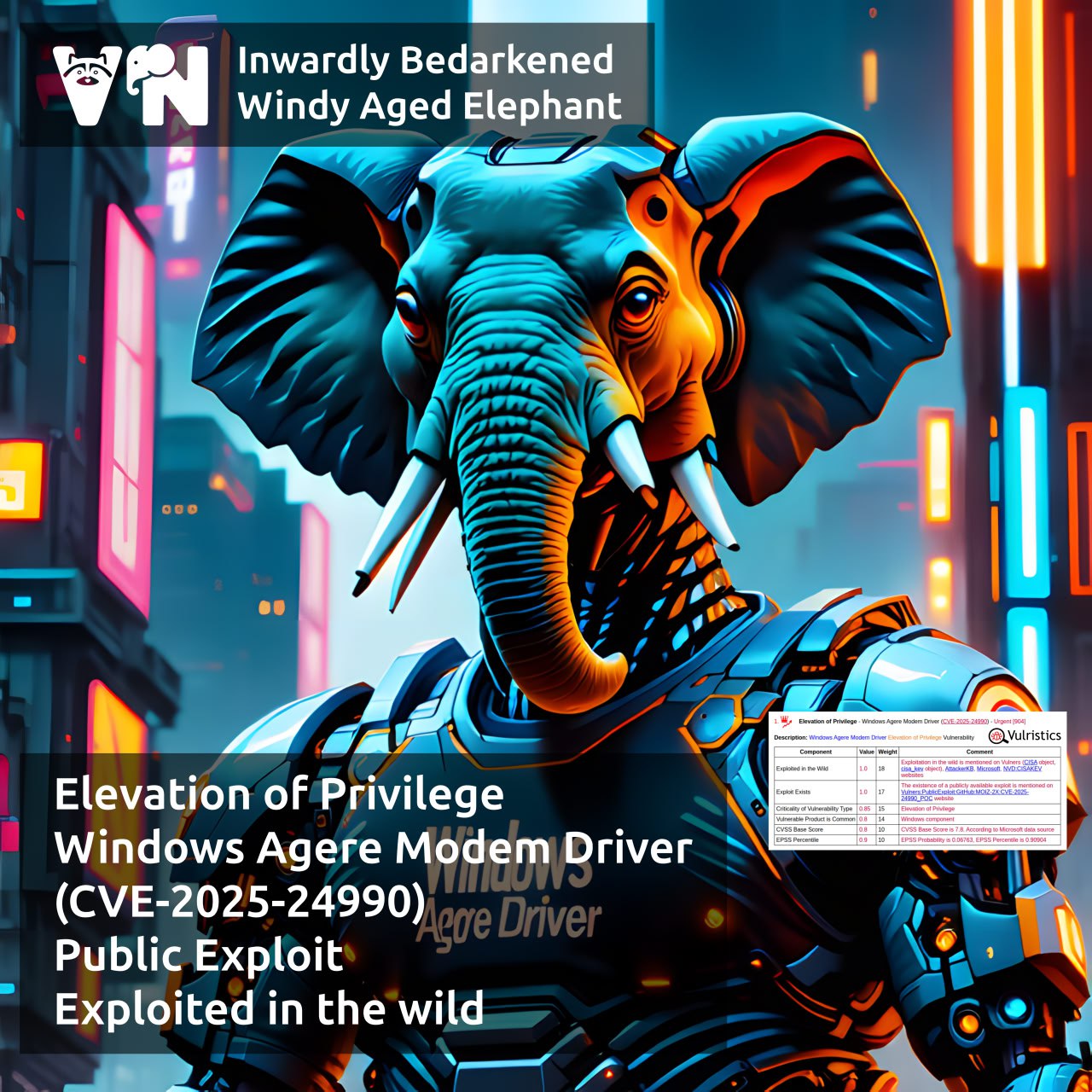
About Elevation of Privilege – Windows Agere Modem Driver (CVE-2025-24990) vulnerability. The vulnerability is from Microsoft’s October Patch Tuesday. Agere Modem Driver (ltmdm64.sys) is a software component that allows a computer to communicate with an Agere (or LSI) modem for dial‑up or fax connections. 📠🙄 Despite its questionable practical usefulness, the driver continued to be shipped with Windows. A local attacker who successfully exploits this vulnerability in the driver can obtain administrative privileges.
⚙️ The Microsoft cumulative update from October 14 removes this driver from the system.
🛠 On October 16, an exploit for the vulnerability was published on GitHub. The author reports that the driver has been shipped since Windows Vista. Microsoft had known about the issue since at least 2014 (11 years ❗️) but ignored it. 🤷♂️
👾 On October 22, this vulnerability was added to the CISA KEV; details about active attacks are not yet known.