Scaner-VS: Vulnerability Management solution for Russian Military. Scaner-VS is a Vulnerability Assessment system developed by Moscow-based NPO Echelon. It’s pretty popular in Russian government organizations, especially in Russian Army, because it comply all government requirements, has all necessary certificates and is relatively cheap.
As for requirements and certificates, NPO Echelon itself is an important certification authority, so they know how to do the things right. It’s not a secret product or something. You can request trial version freely at http://scaner-vs.ru/version-for-testing/. But note, that it is only available in Russian. I am also sorry, but screenshots in this post will be also in Russian. I will try to do my best to describe them properly.
When you fill the form on Echelon website, you will soon get a link to 3.3 gb .iso file by email. Run it in VirtualBox virtual machine (choose Debian 64 or Debian 32).
Here is a boot menu. Choose first default option.
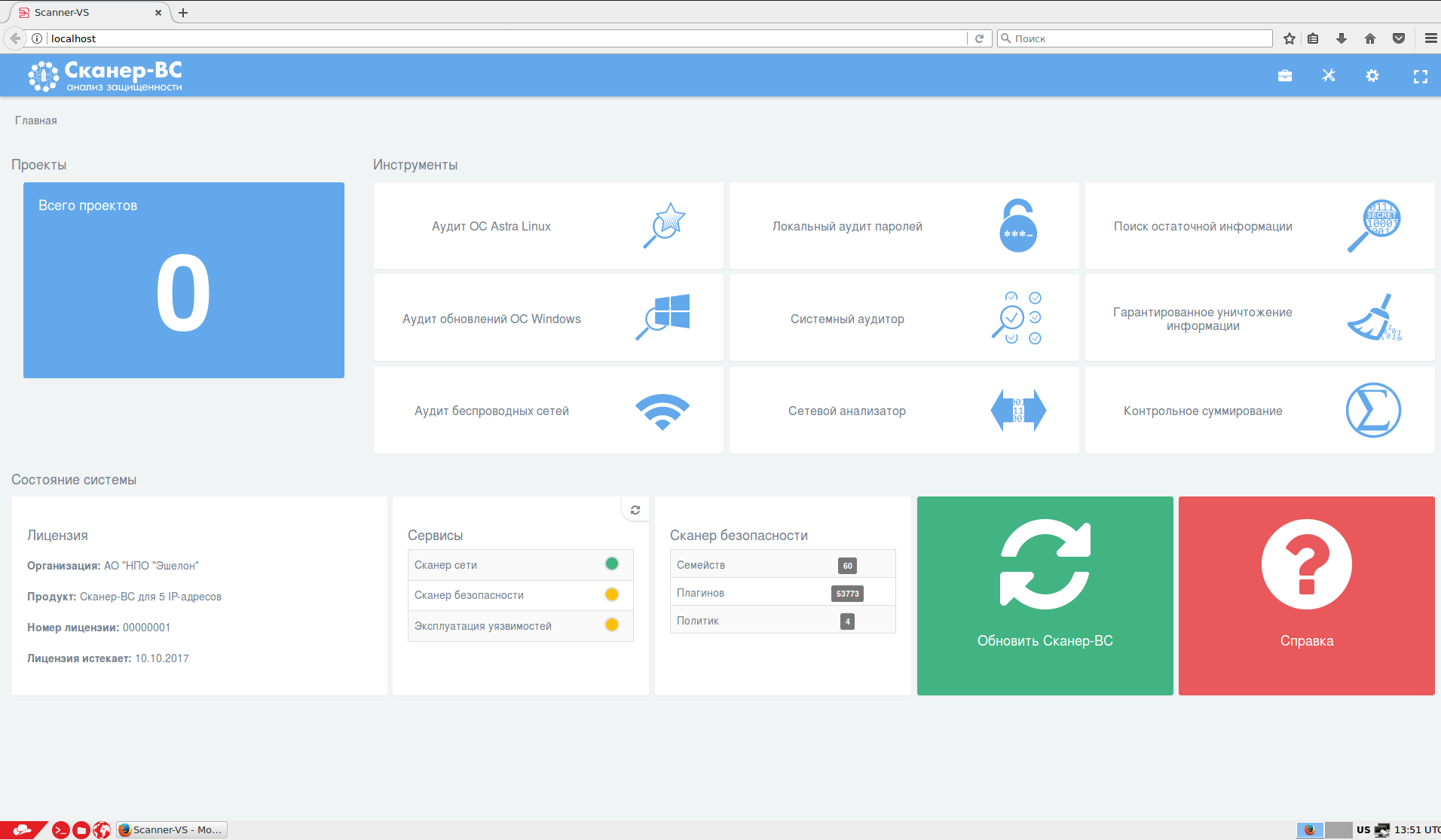
Some seconds later you will see Linux desktop environment with Scaner-VS web-GUI opened in Firefox.
So, as you can see, Scaner-VS is a Linux distribution with preinstalled security audit tools and some web-gui or framework that combines them. Some of the tools are well-known open source projects, others were developed by Echelon. If you press on 0 at the upper left, you will open project window of the main Vulnerability Scanner. Icons in table-like menu at the rights launch different Echelon tools:
- Astra Linux audit (Russian certified Debian-based distribution)
- Windows security updates audit
- Wireless nets audit
- Local passwords audit
- System audit
- Network analyzer
- Residual information search
- Guaranteed information destruction
- Checksum tool
Kali and OpenVAS
If you click on OS Start button, you will be probably note how the menu is similar to Kali Linux.
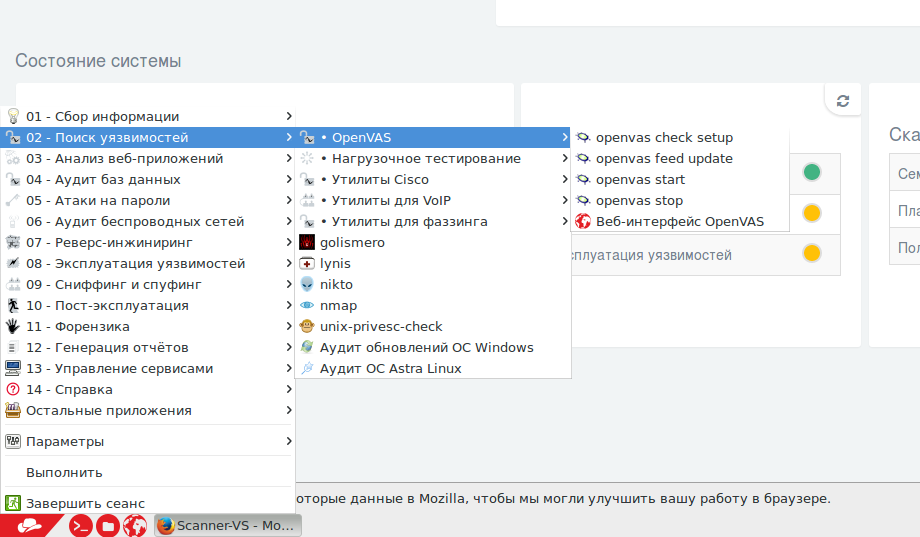
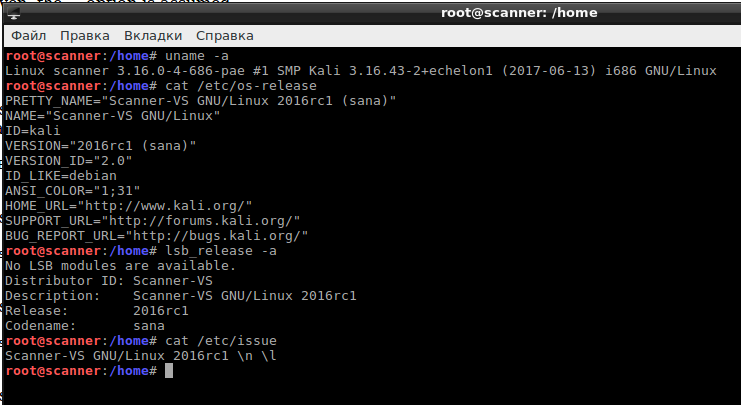
Well, the distribution was completely rebranded, but it is obviously based on Kali Linux 2.0 Sana:
You can also see a pretty old version of OpenVAS here:
Including OpenVAS GUI – Greenbone Security Manager:
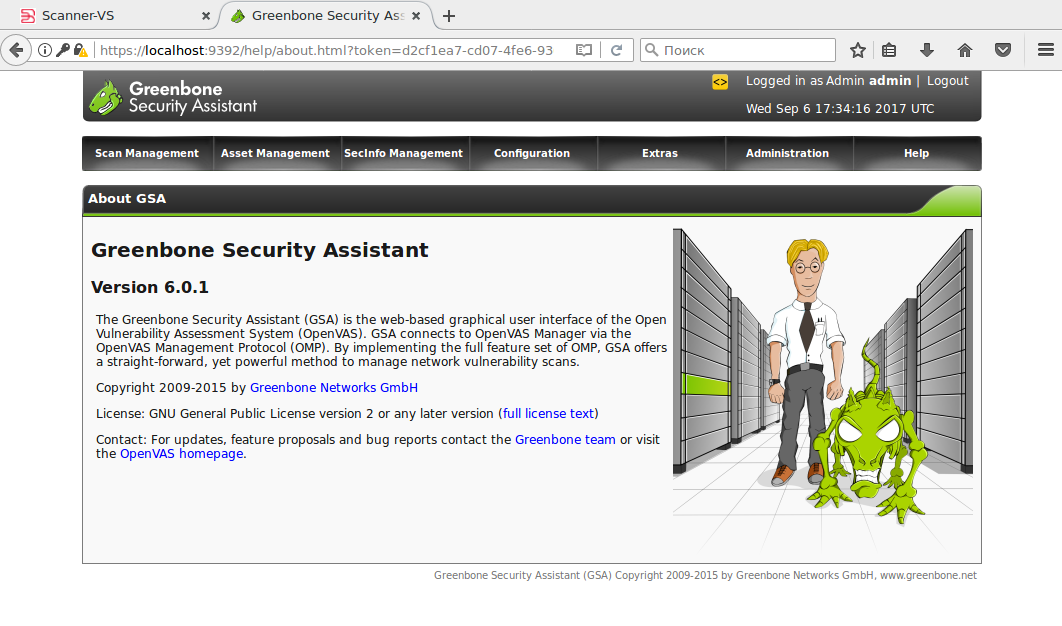
It’s the components of OpenVAS 6, the current version OpenVAS is 9.
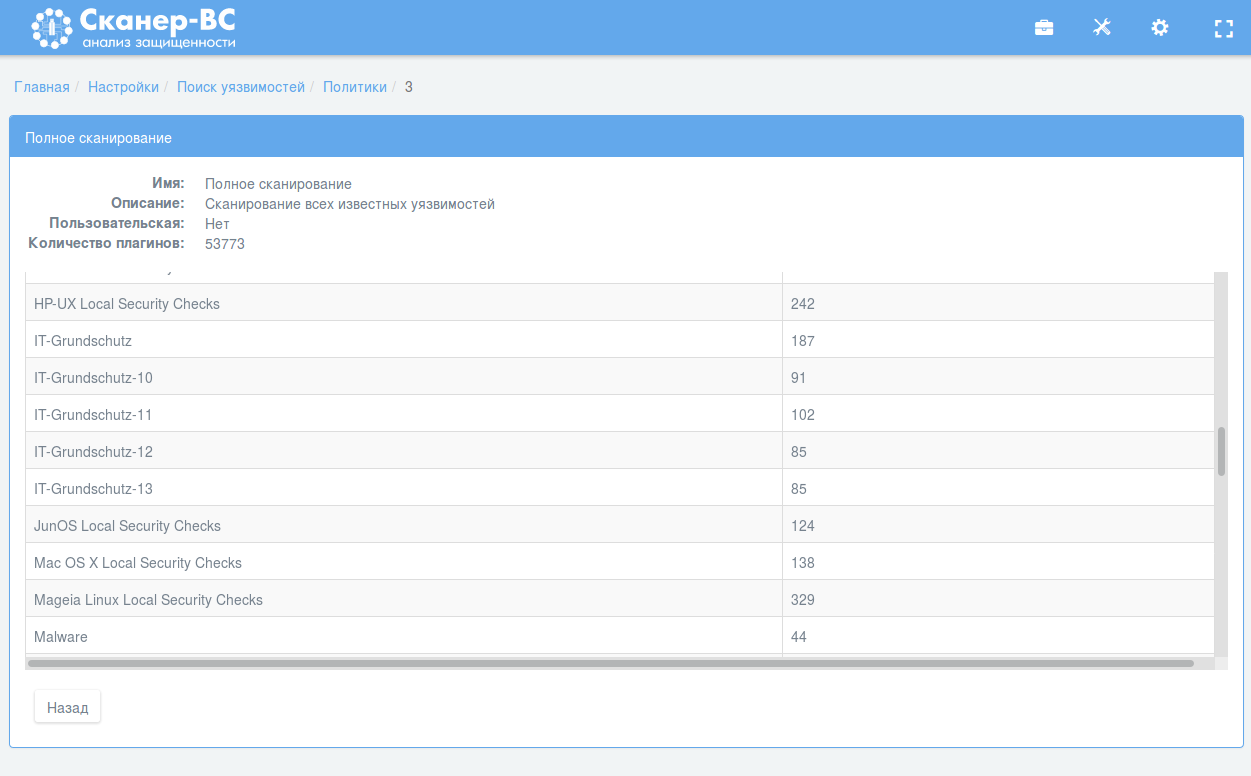
OpenVAS is under the hood of the main Vulnerability Scanner in Scaner-VS. It’s pretty obvious if you look on plugin group names in policy settings, like “Local Security Checks” and “IT-Grundschutz”, very typical for OpenVAS:
Scaner-VS Projects
Old versions of Scaner-VS used modified web-GUI by Greenbone. Now they have own GUI, that is actually pretty good.
The main idea of this Scaner-VS interface: users will work with the “Projects” – some spaces where you, you can make different kinds of scanning and and correlate the results. Very natural way to do Audits, by the way.
Let’s try to scan something, for example a CentOS host. I created a new project:
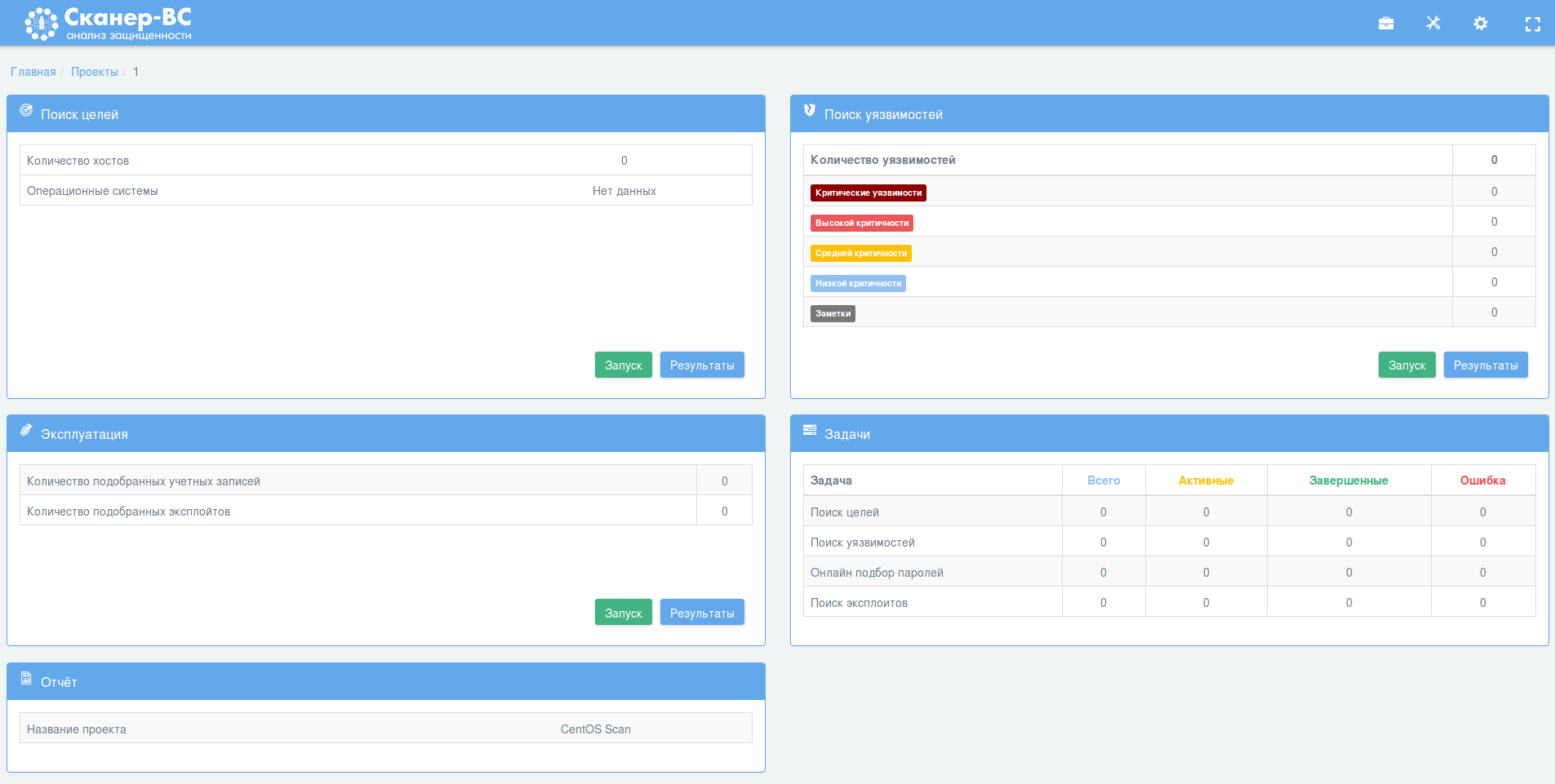
Dashboard of a new project:
The elements of a dashboard:
- Target searching
- Vulnerability scanning
- Vulnerability exploitation
- Tasks
- Report
I press green scan button in upper-right Vulnerability Scanning element.
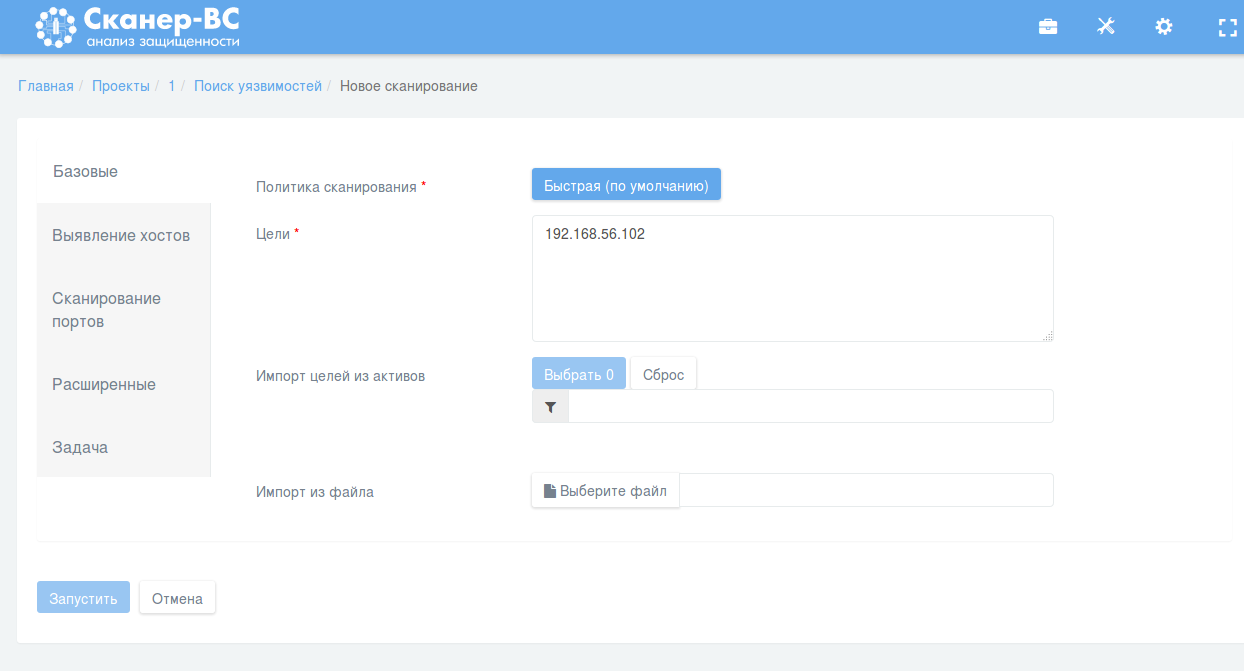
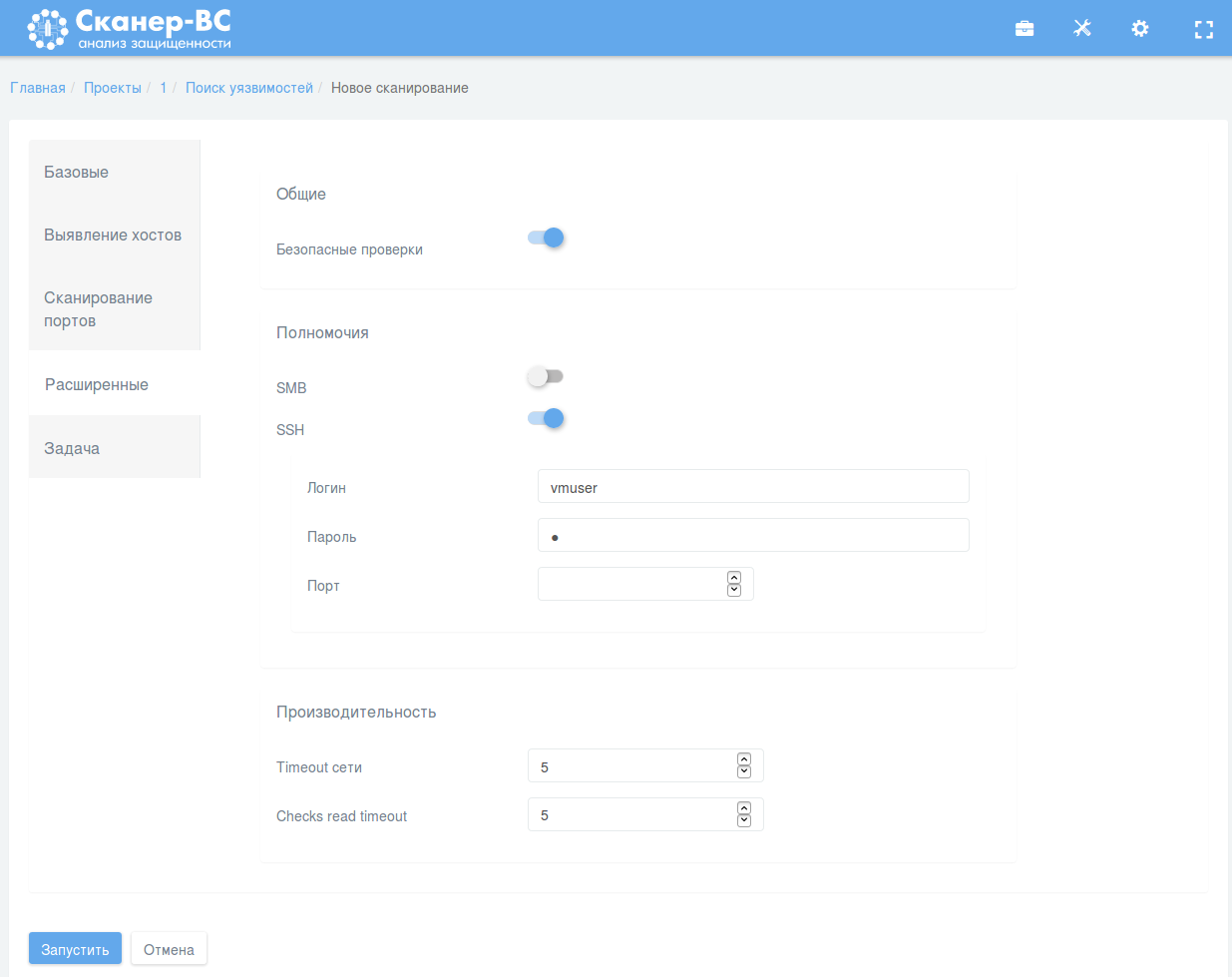
This is this Scan Configuration interface looks like:
Obviously inspired by Nessus 😉
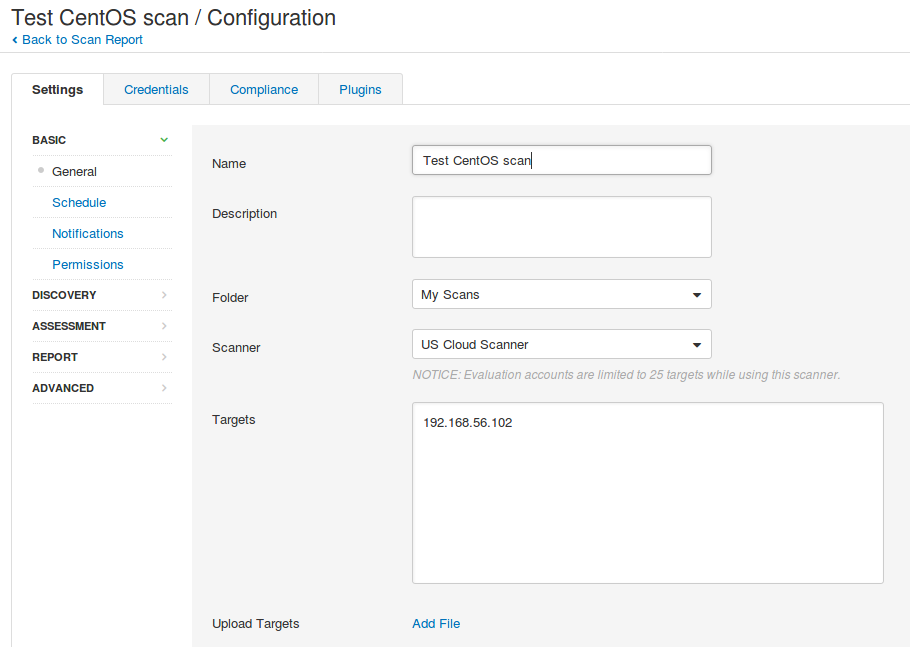
But, actually, I like it even more. For example, it doesn’t require you to fill the scan name if you don’t want to. It may generate the name from a target list and policy name. I chose Full Scan policy, set the IP in “Basic” tab, credentials in “Advanced” tab and launched the scan:
Scan is processing:
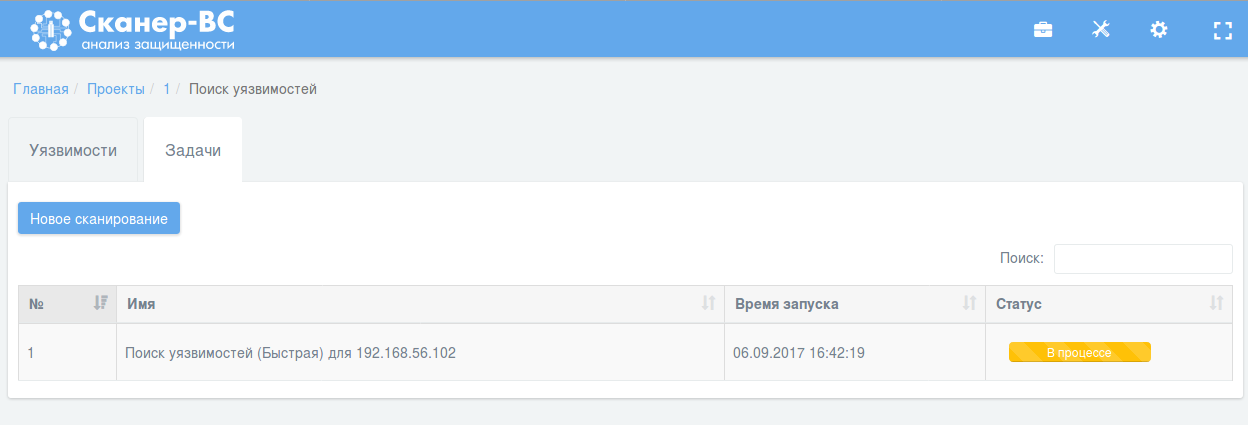
And some minutes later the scan is finished and we can see the report:
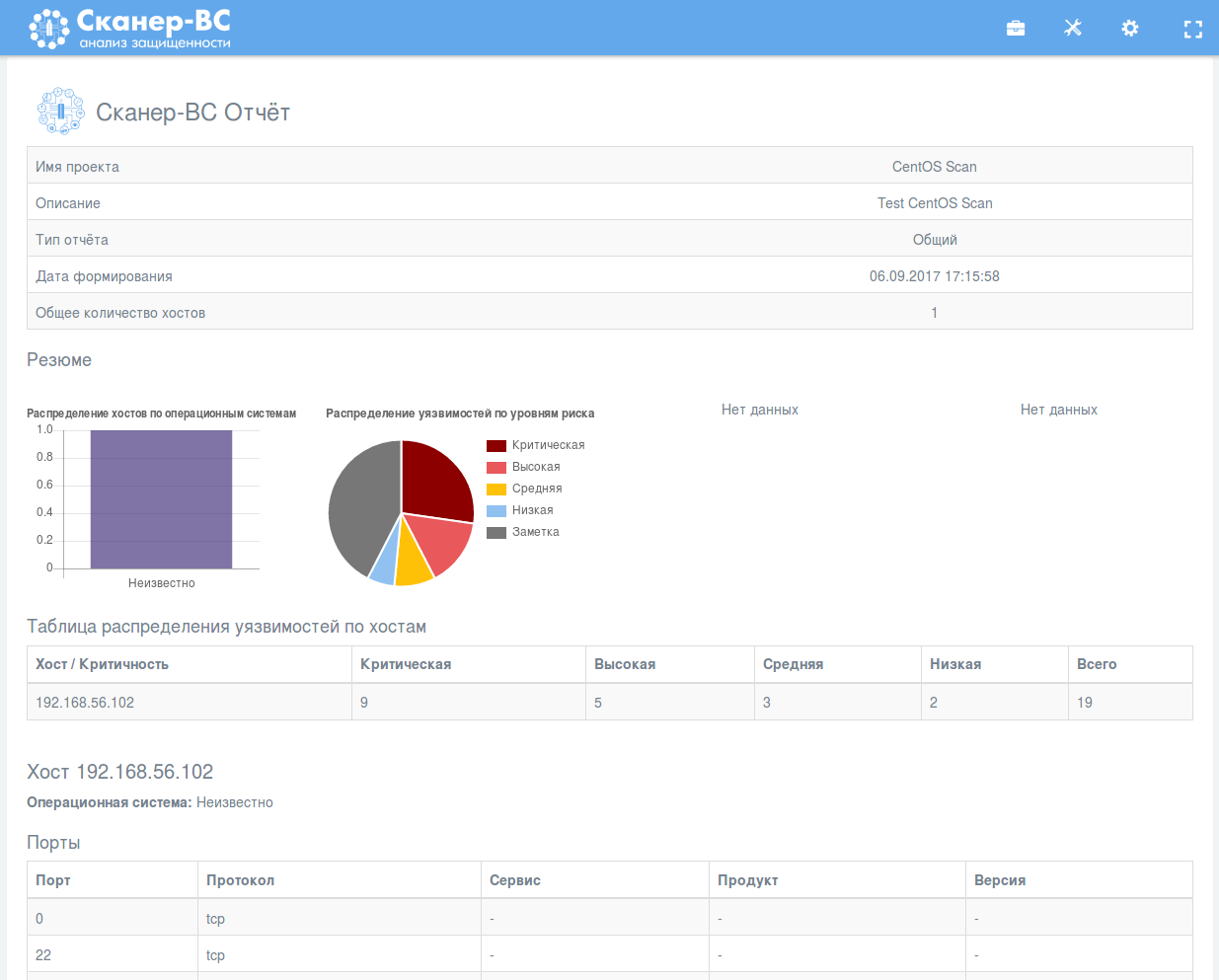
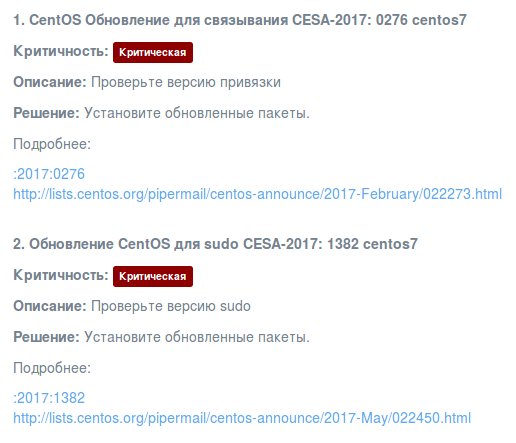
The report looks quite pretty. As you can see, there is no description for CESA vulnerabilities, cause it was probably too expensive to translate them all into Russian:
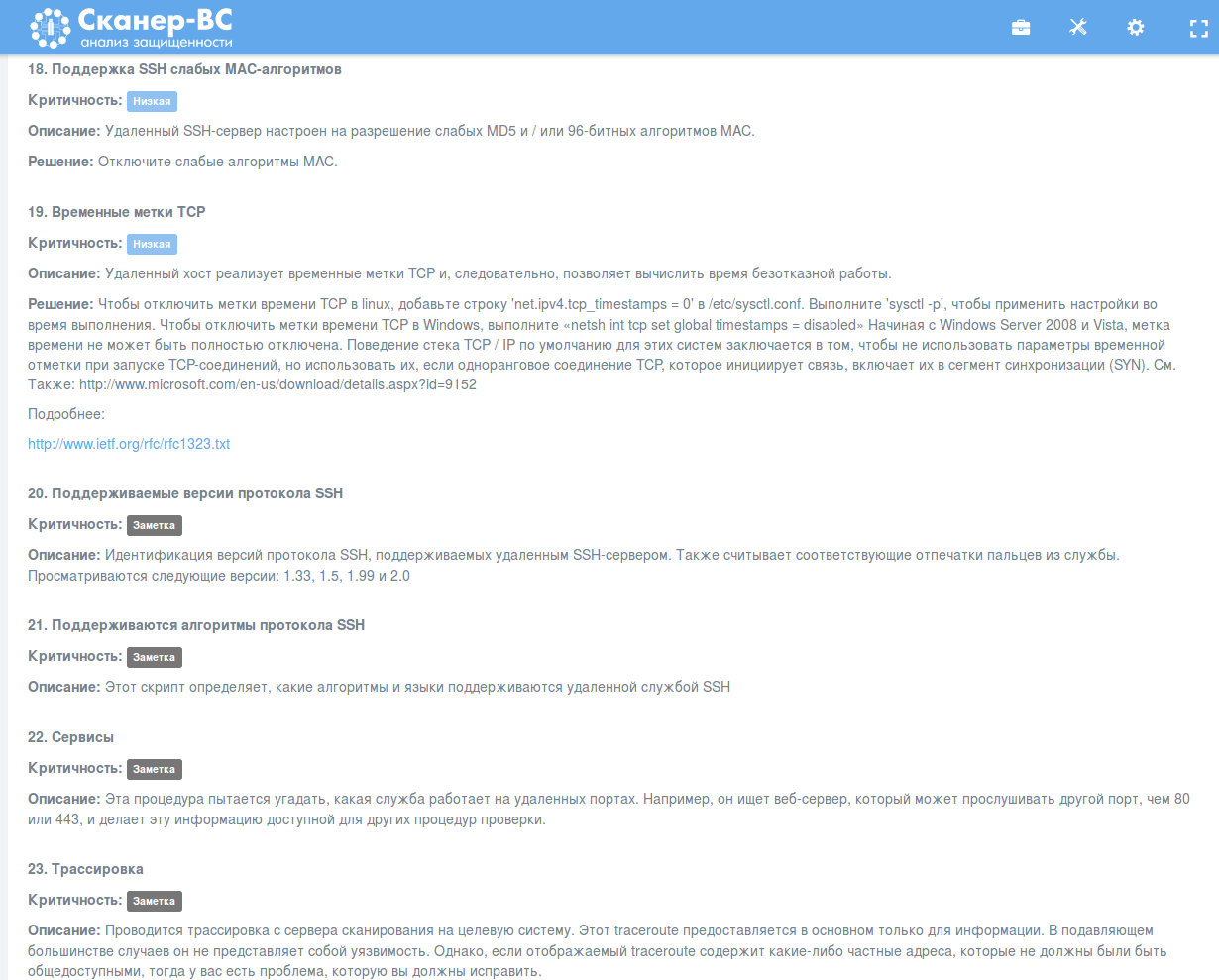
But more common plugins are translated in Russian completely:
This is how the scan dashboard looks after the scan is finished:
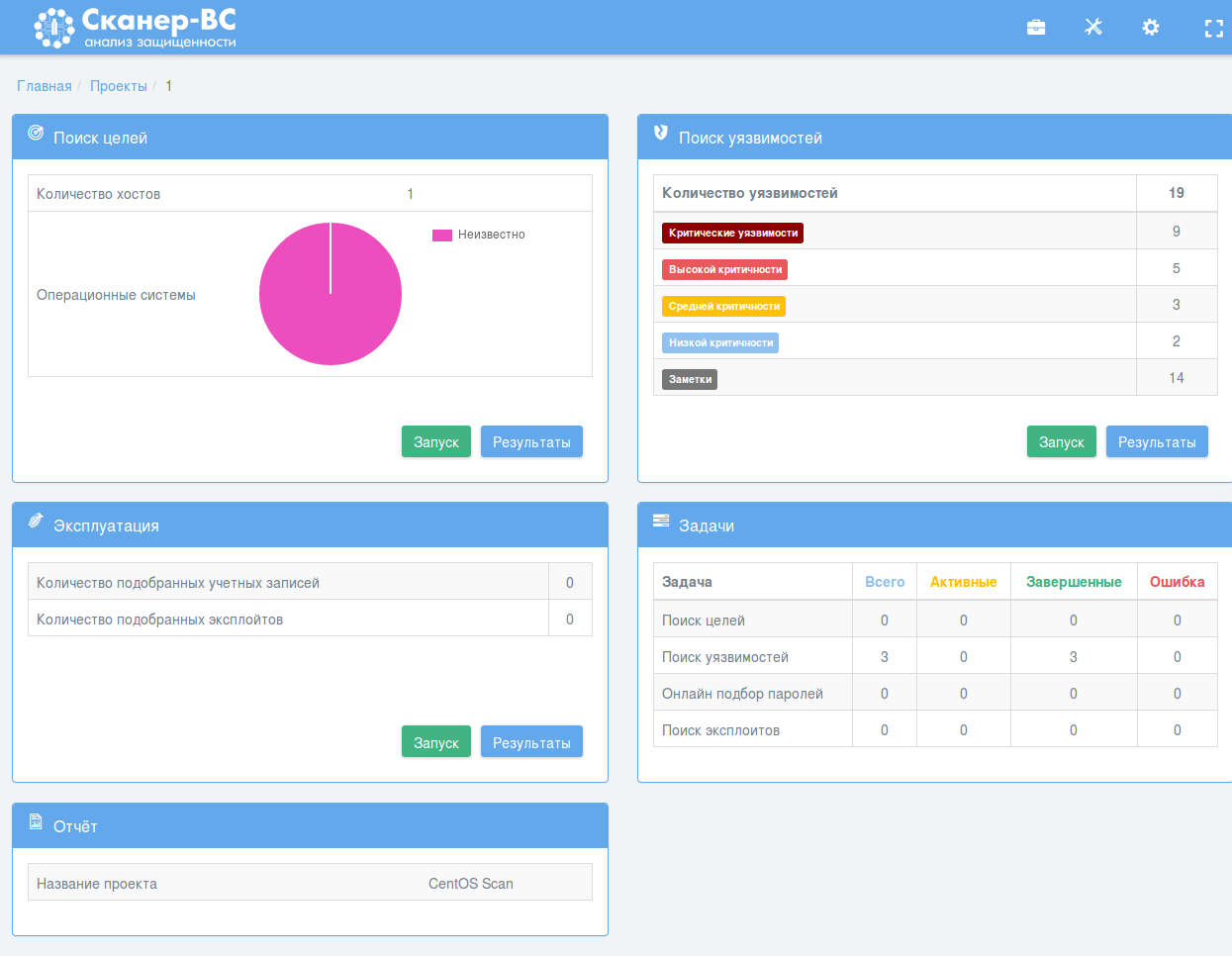
Well, there are some small problems, first element – “Target searching” sees some host in assets, but doesn’t show it as CentOS Linux host. However the OS was obviously detected, if we have CESA vulnerability in “Vulnerability scanning” results. Probably, it’s because Scaner-VS takes data only from nmap-based scanning.
When I scanned 192.168.56.102 with “Target searching”, I’ve got this:
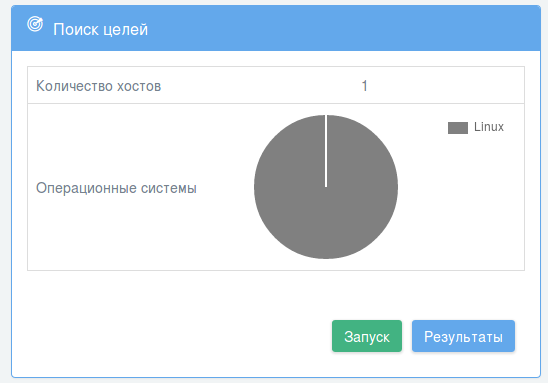
Linux. Not CentOS, but still better than nothing =)
In conclusion
I am very glad for Scaner-VS and Echelon. The progress is visible, the product is much better than it was several years ago. Some people criticize vendors, who earn money selling products based on open source. I was never agree with them. GPL does not forbid selling software. And the product is not the software itself, but also marketing, support, training, infrastructure, and, of course, certifications. For end-user from government organization that means that he will use familiar security tools from Kali absolutely legitimately. Isn’t it great?
I am not even telling about the fact that significant part of software for Scanner-VS was developed in Echelon. And this part looks pretty good. The fact that they use OpenVAS under the hood is also great. It is much easier to modify than some proprietary solutions, adding some own nasl plugins. I only hope that they will move to fresh version of OpenVAS and OPM (GMP) protocol for managing it.

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.