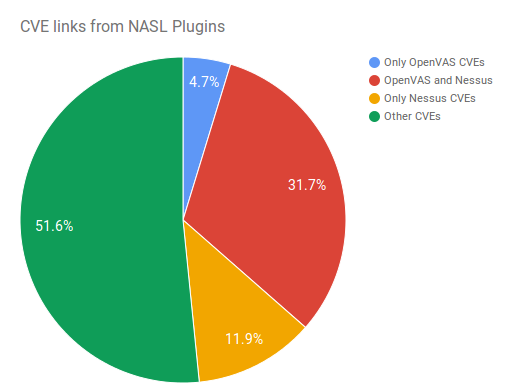
Vulners Subsriptions and Apache Struts RCE. If you work in IT Security Department of any large software developing company, you were probably searching for Apache Struts in your environment on this week.
And it’s all because of CVE-2017-5638:
Apache Struts is a free, open-source, Model-View-Controller (MVC) framework for creating elegant, modern Java web applications, which supports REST, AJAX, and JSON.
In a blog post published Monday, Cisco’s Threat intelligence firm Talos announced the team observed a number of active attacks against the zero-day vulnerability (CVE-2017-5638) in Apache Struts
This is a good example, that shows the usefulness of the Vulners.com service.
Just open cvelist:CVE-2017-5638 query and you will see all the objects related to this issue. This request works even before this CVE number appear on NVD and Mitre databases!
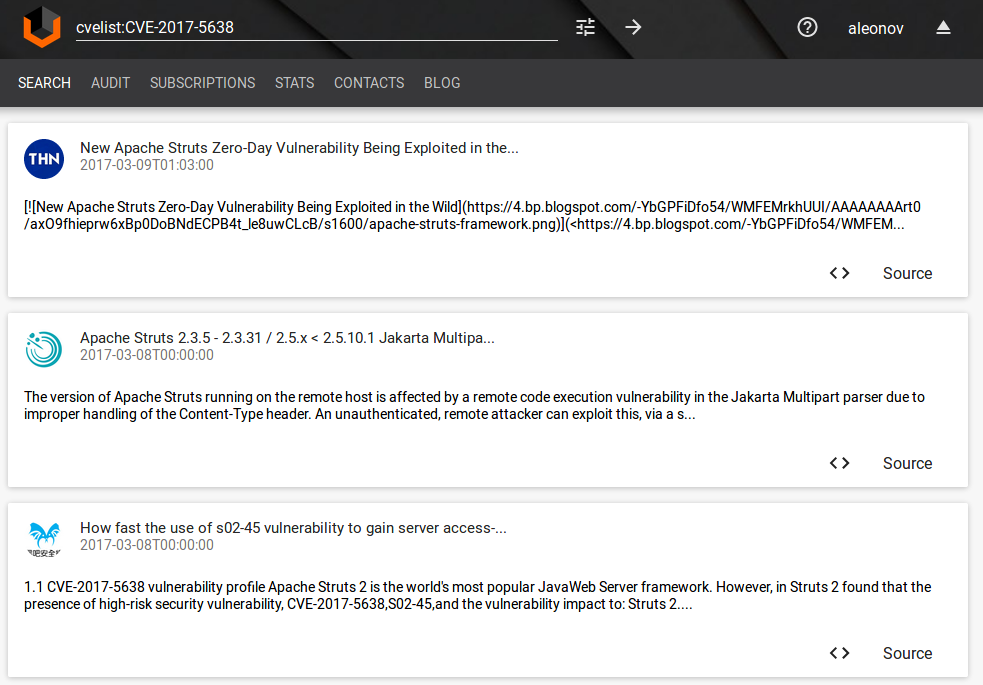
Here are: description of the vulnerability from The Hacker News, manual on how to use this vulnerability to gain server access from myhack58, Nessus local windows and remote cgi detection plugins.