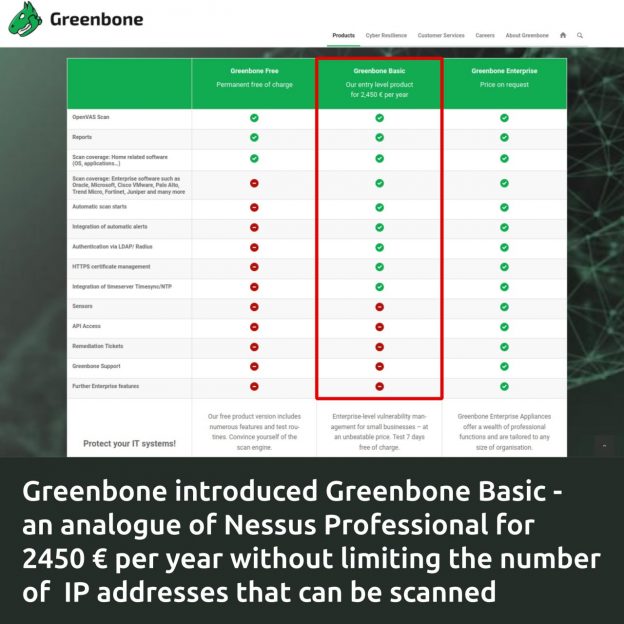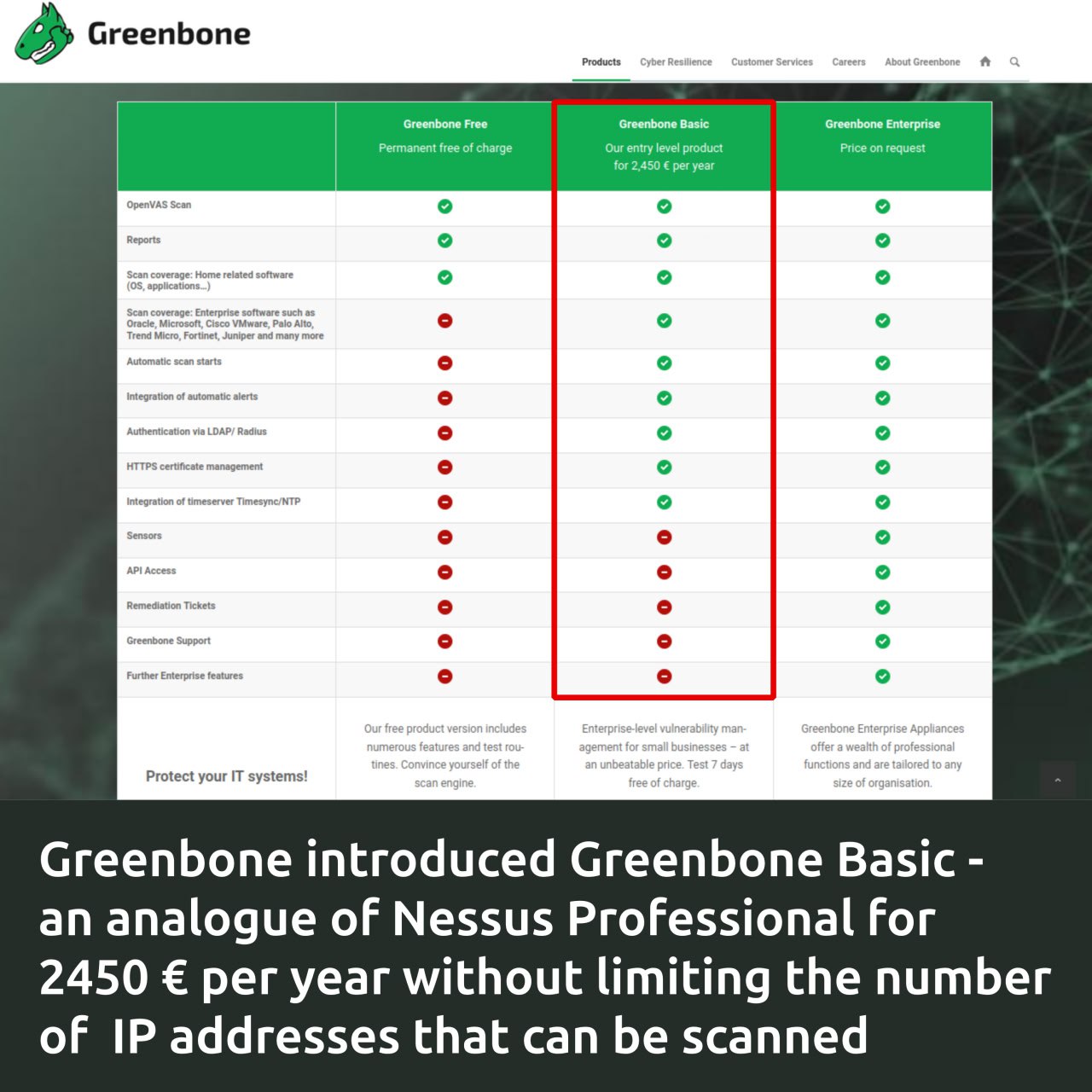
Greenbone introduced the Greenbone Basic vulnerability scanner for SMEs, the price of which is NOT tied to the number of IP addresses that can be scanned. A license for 1 scanner will cost 2450 € per year. It will be delivered as a virtual machine image. There is a comparison table and a data sheet.
Greenbone Basic differences:
🔹 Compared to Greenbone Free, it WILL have a full database of plugins for vulnerability detection, compliance scanning, scan scheduler, alerts, LDAP/Radius authentication, HTTPS certificate management, NTP integration.
🔹 Compared to Greenbone Enterprise, there WILL NOT be the ability to hierarchically connect scanners (sensors). API support, vulnerability remediation tickets, technical support from Greenbone and further enterprise features.
In terms of features, it looks like a real alternative to Tenable’s Nessus Professional. Competition in the entry-level fixed-price VM segment is intensifying. 👍