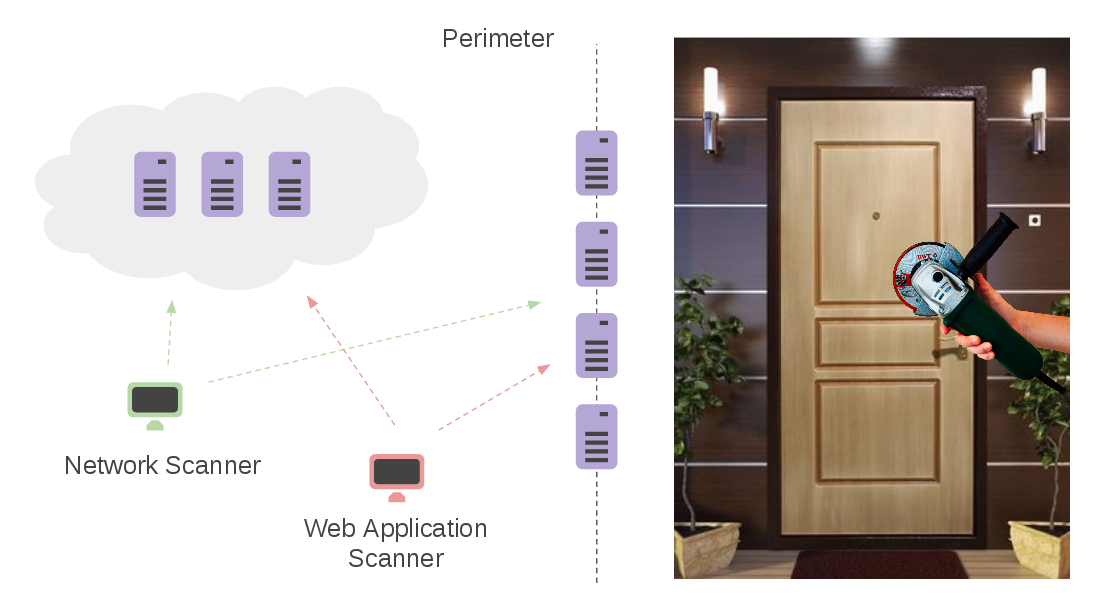
I have already wrote about Atlassian Jira automation in “Automated task processing with JIRA API“. But all examples there were with using of curl. So, I decided to make one more post about Jira API. This time with python examples and about labeling issues (nice wordplay, right? 😉 ).

You can use labeles for organizing issues on Jira Scrum and Kanban Boards, Jira Dashboards or just for advanced searching (e.g. labels = "LabelName")
Let’s start from the basics.
How to search Jira issues from your own python scripts?
It’s easy. Send a post request to /rest/api/2/search/ with some JQL expression. Jira server will return first 50 matching issues. If you need more, set a startAt parameter and repeat post requests while the number of issues you requested is less than total number of founded issues (parameter in response).