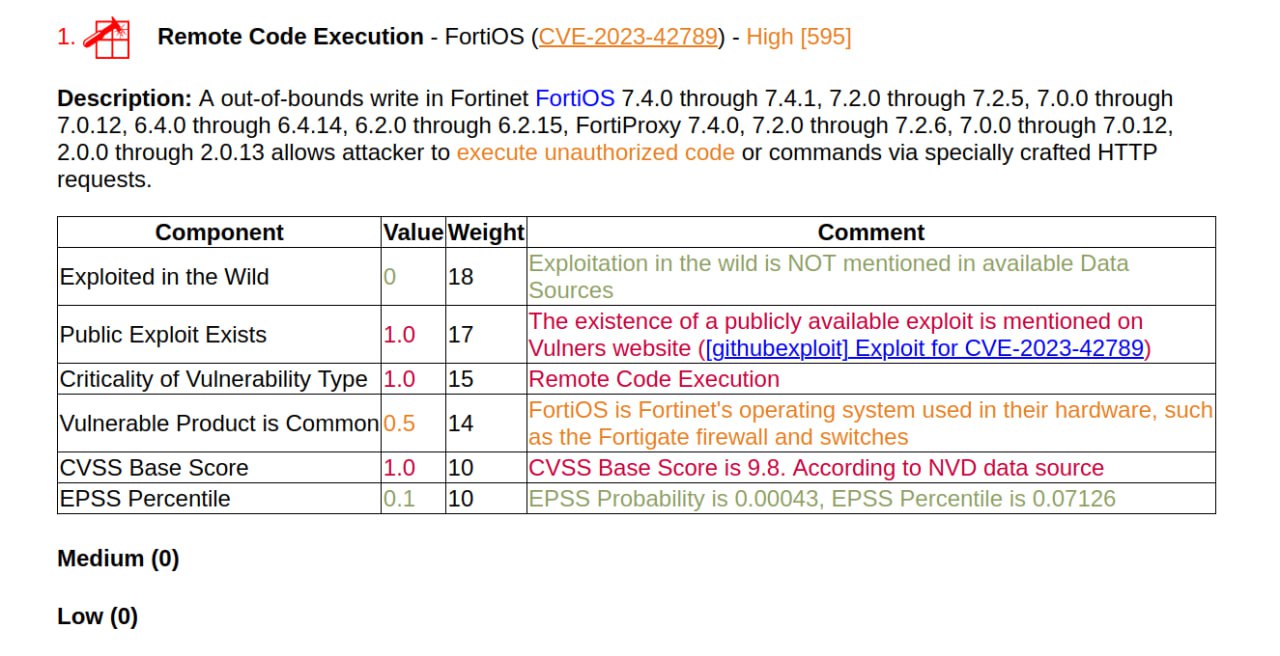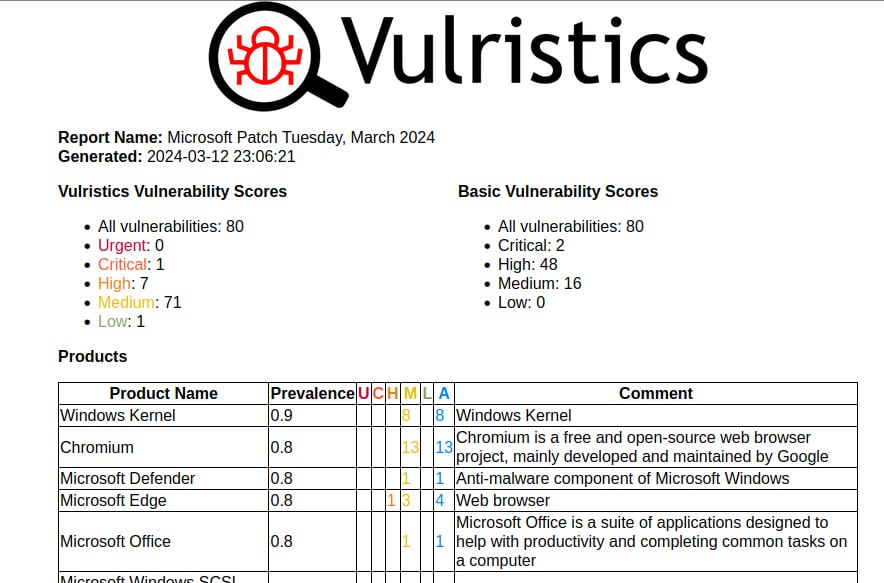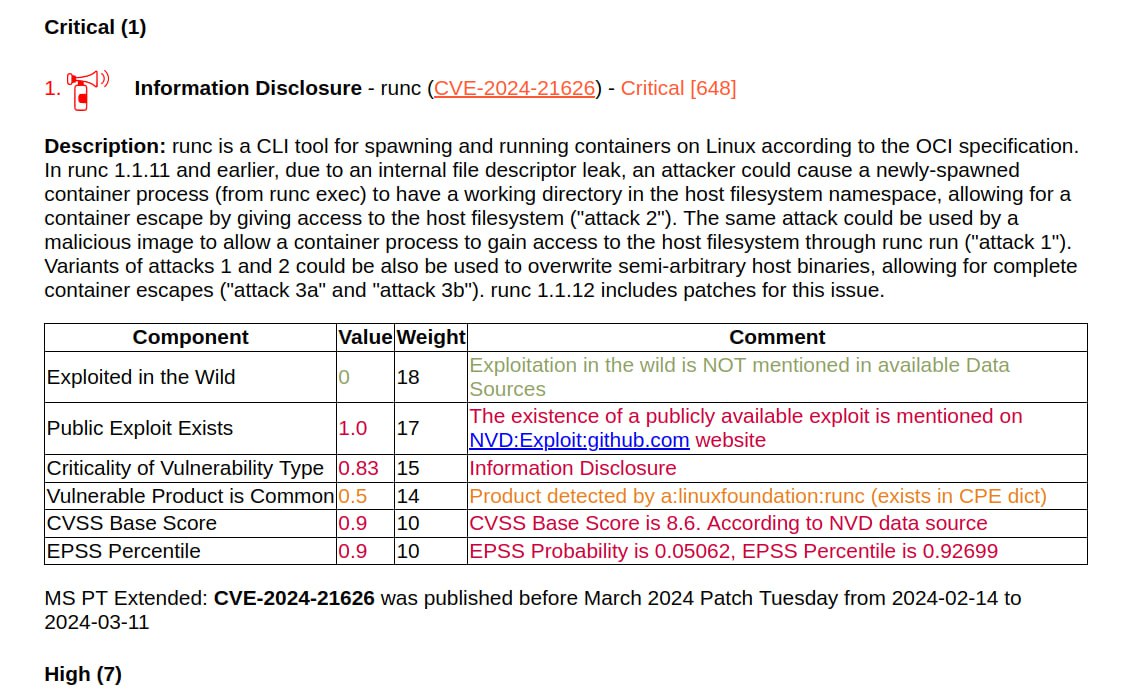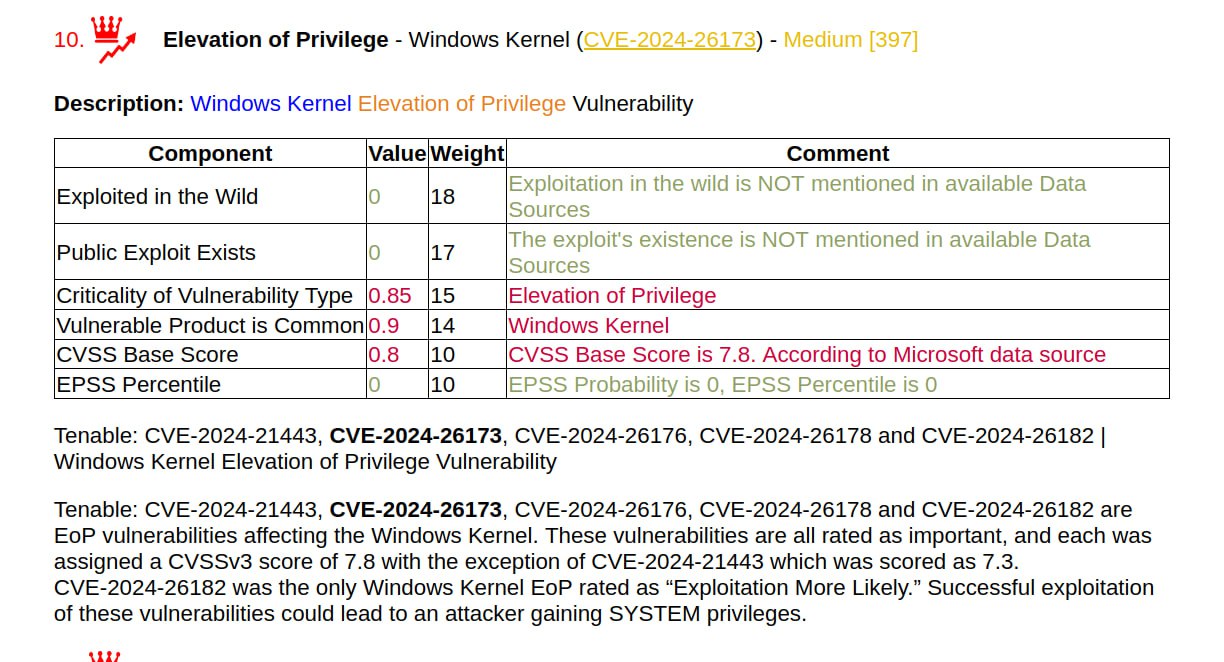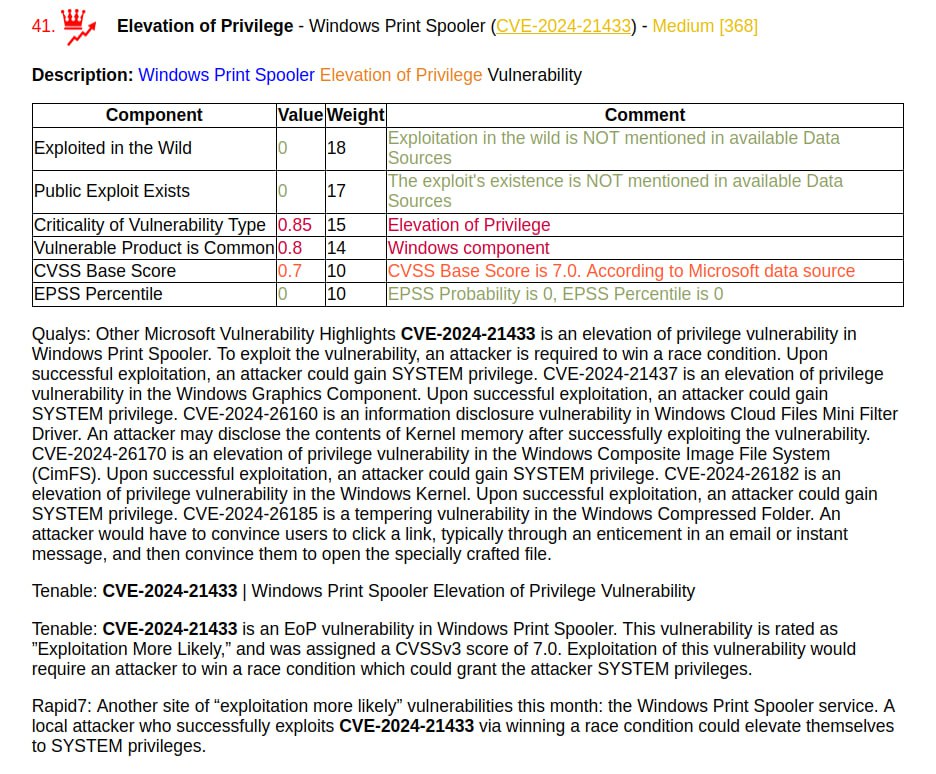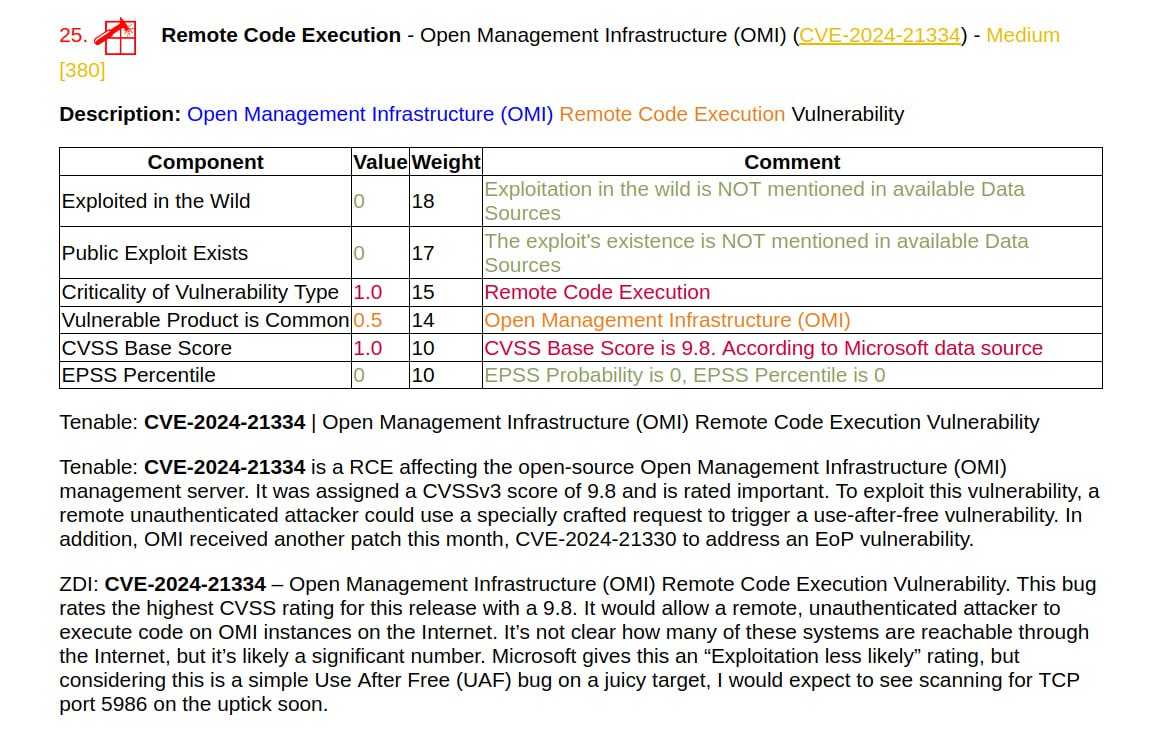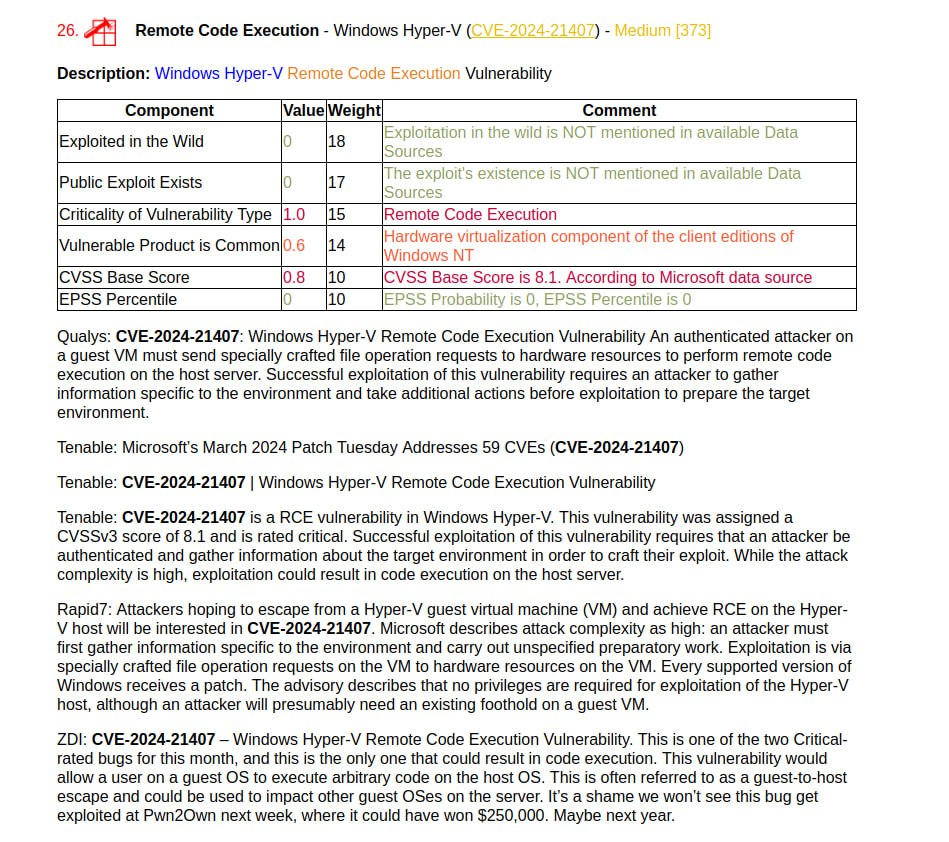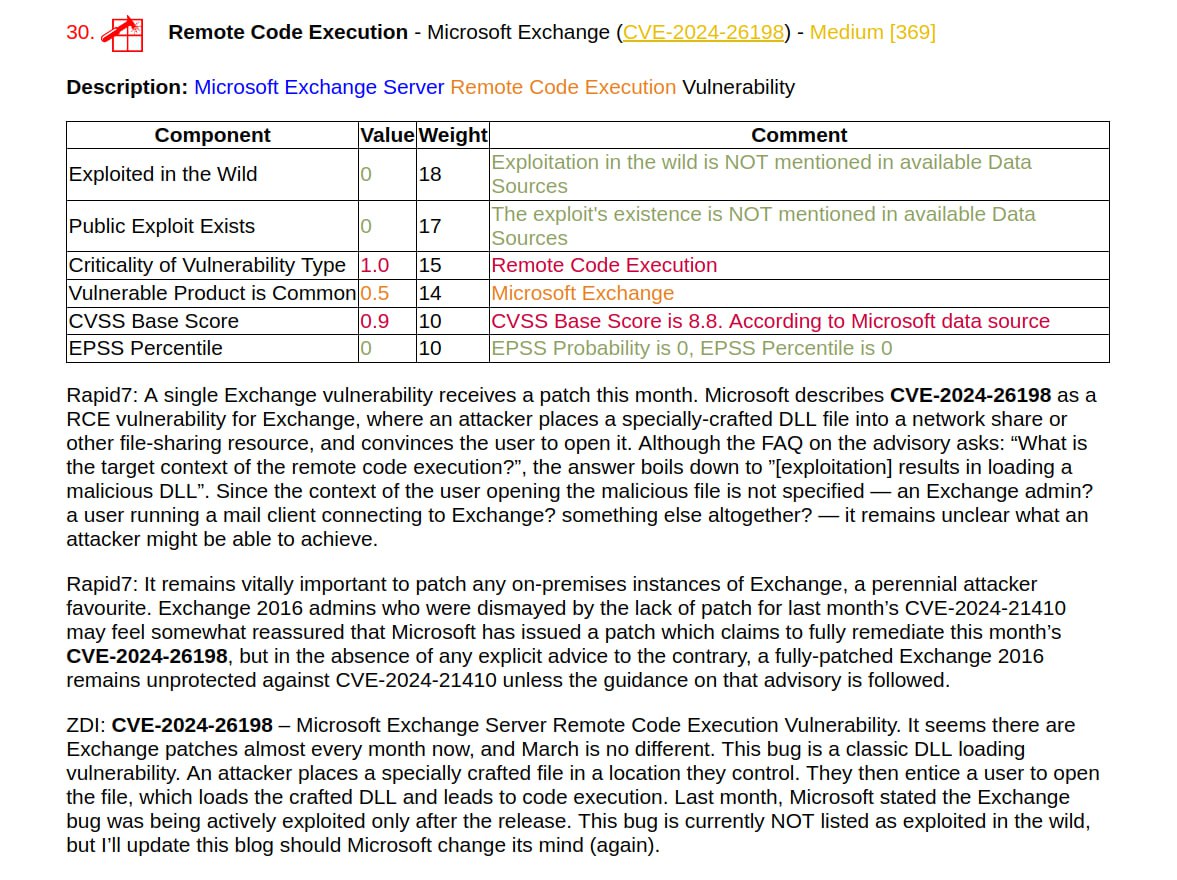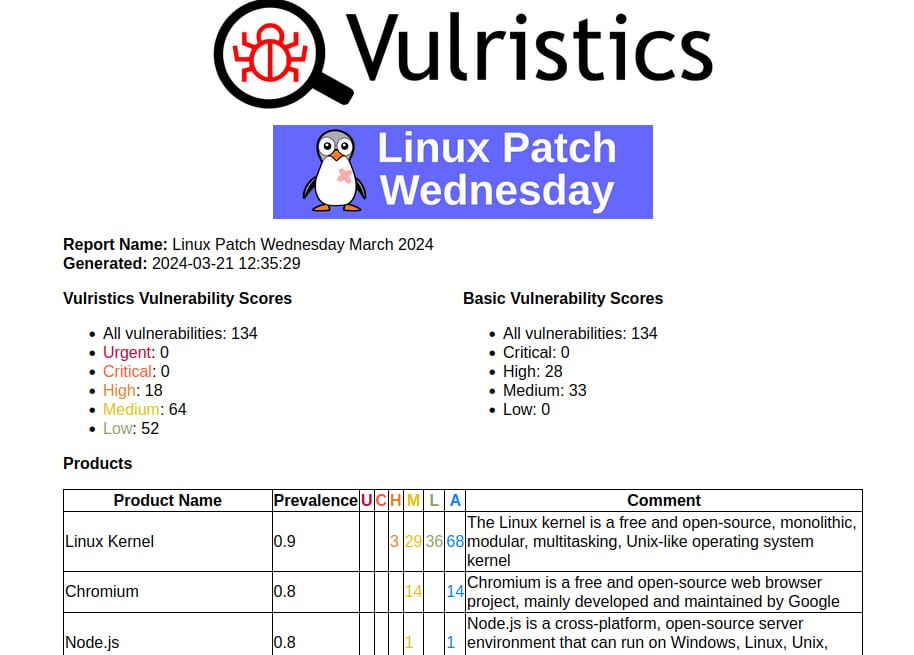
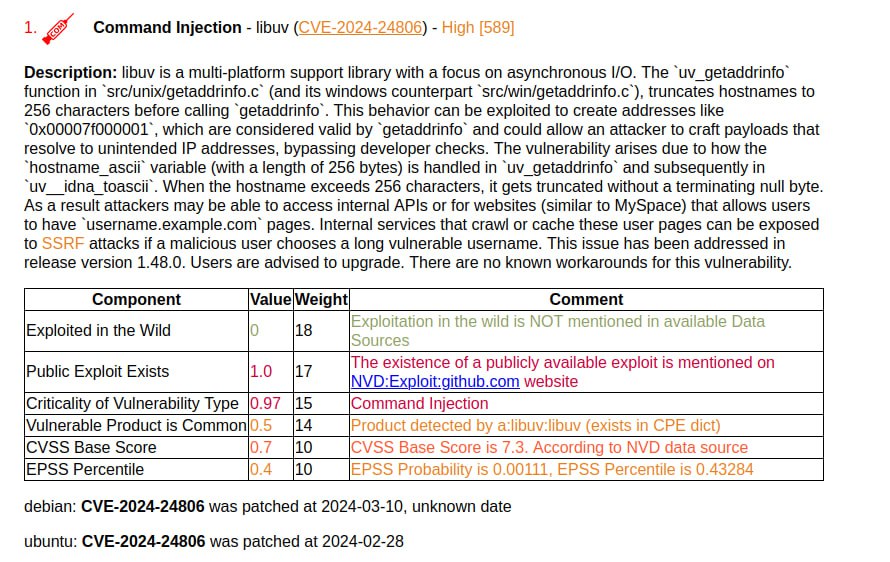
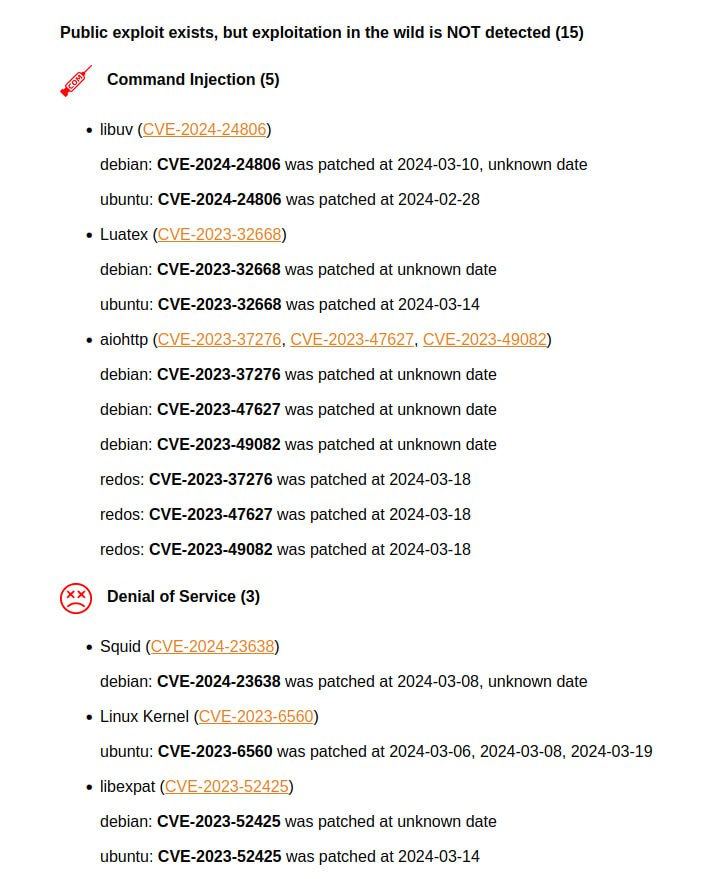
I generated a report on the March Linux Patch Wednesday. 134 vulnerabilities, of which 68 are in the Linux Kernel. There are no vulnerabilities with signs of exploitation in the wild. There are 15 vulnerabilities with PoCs.
🔸 The top vulnerability is Command Injection – libuv (CVE-2024-24806). This is a multi-platform library for asynchronous I/O. An attacker could potentially access internal APIs.
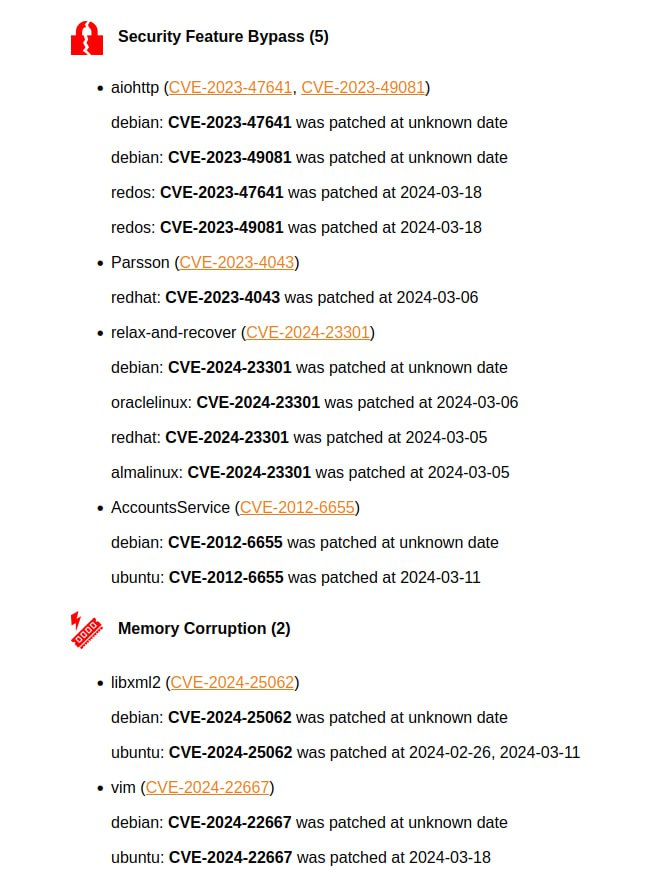
🔸 For aiohttp there is a pack of Command Injection (CVE-2023-37276, CVE-2023-47627, CVE-2023-49082) and Security Feature Bypass (CVE-2023-47641, CVE-2023-49081) with PoCs. It is an asynchronous client/server HTTP framework. The vulns were patched only in Russian RedOS and Debian.
🔸There are problems with vulnerability types/products detection due to the NVD crisis (no CPE & CWE). 🤷♂️
🔸 The Linux Kernel team is now a CNA and is creating a ton of CVEs with monstrously large descriptions. Because they can! 😏