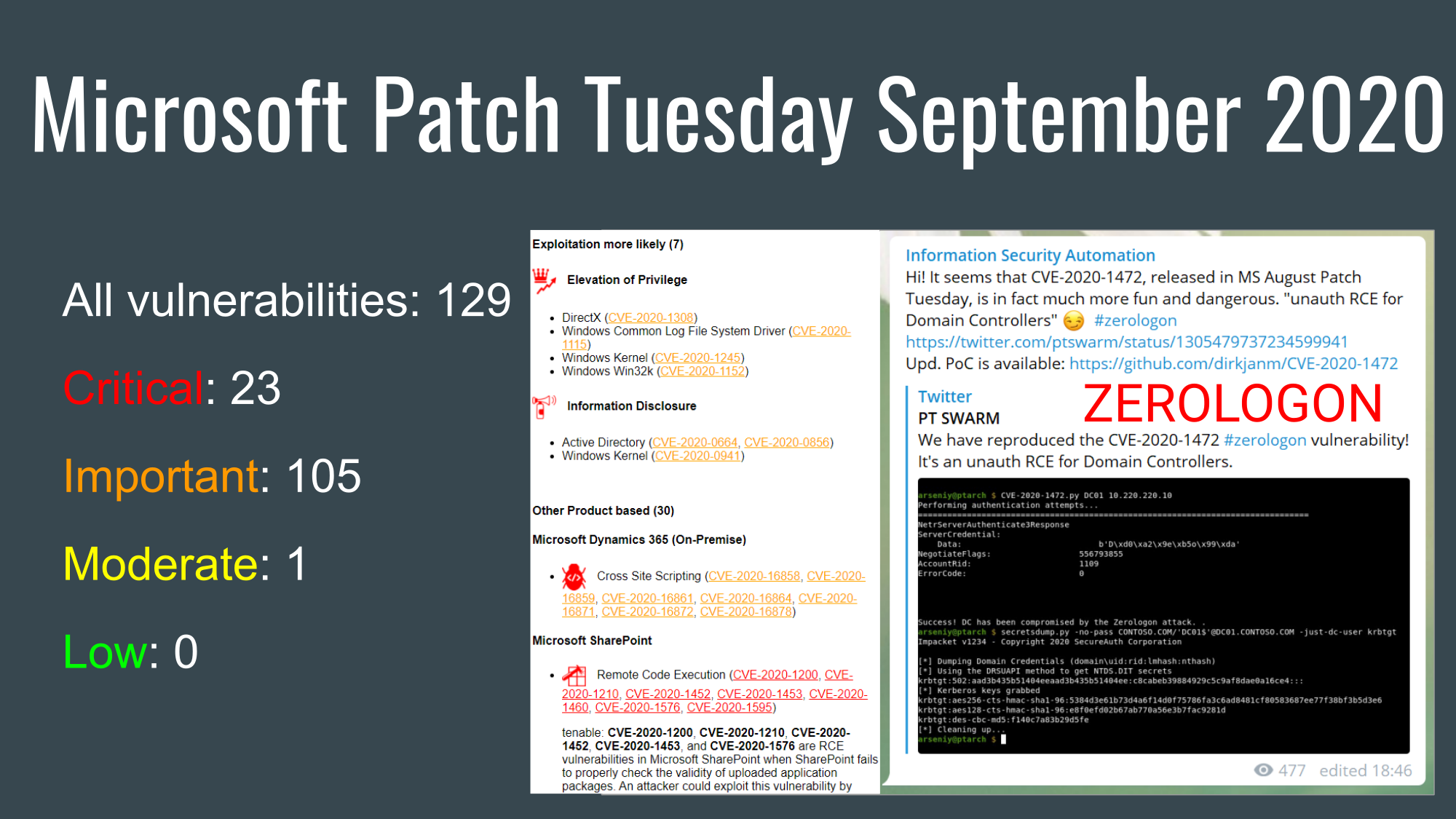
Vulristics Microsoft Patch Tuesday July 2021: Zero-days EoP in Kernel and RCE in Scripting Engine, RCEs in Kernel, DNS Server, Exchange and Hyper-V. Hello everyone! For the past 9 months, I’ve been doing Microsoft Patch Tuesday reviews quarterly. Now I think it would be better to review the July Patch Tuesday while the topic is still fresh. And that will save us some time in the next Last Week’s Security news episode. So, July Patch Tuesday, 116 vulnerabilities.
The 2 most critical are the Windows Kernel Elevation of Privilege Vulnerabilities (CVE-2021-31979, CVE-2021-33771). These vulnerabilities are critical because they are used in real attacks according to Microsoft’s Threat Intelligence Center and Security Response Center. Tenable: “A local, authenticated attacker could exploit these vulnerabilities to run processes with elevated permissions. Similar zero-day vulnerabilities were patched in April 2020, which were observed under active exploitation by Google Project Zero.”