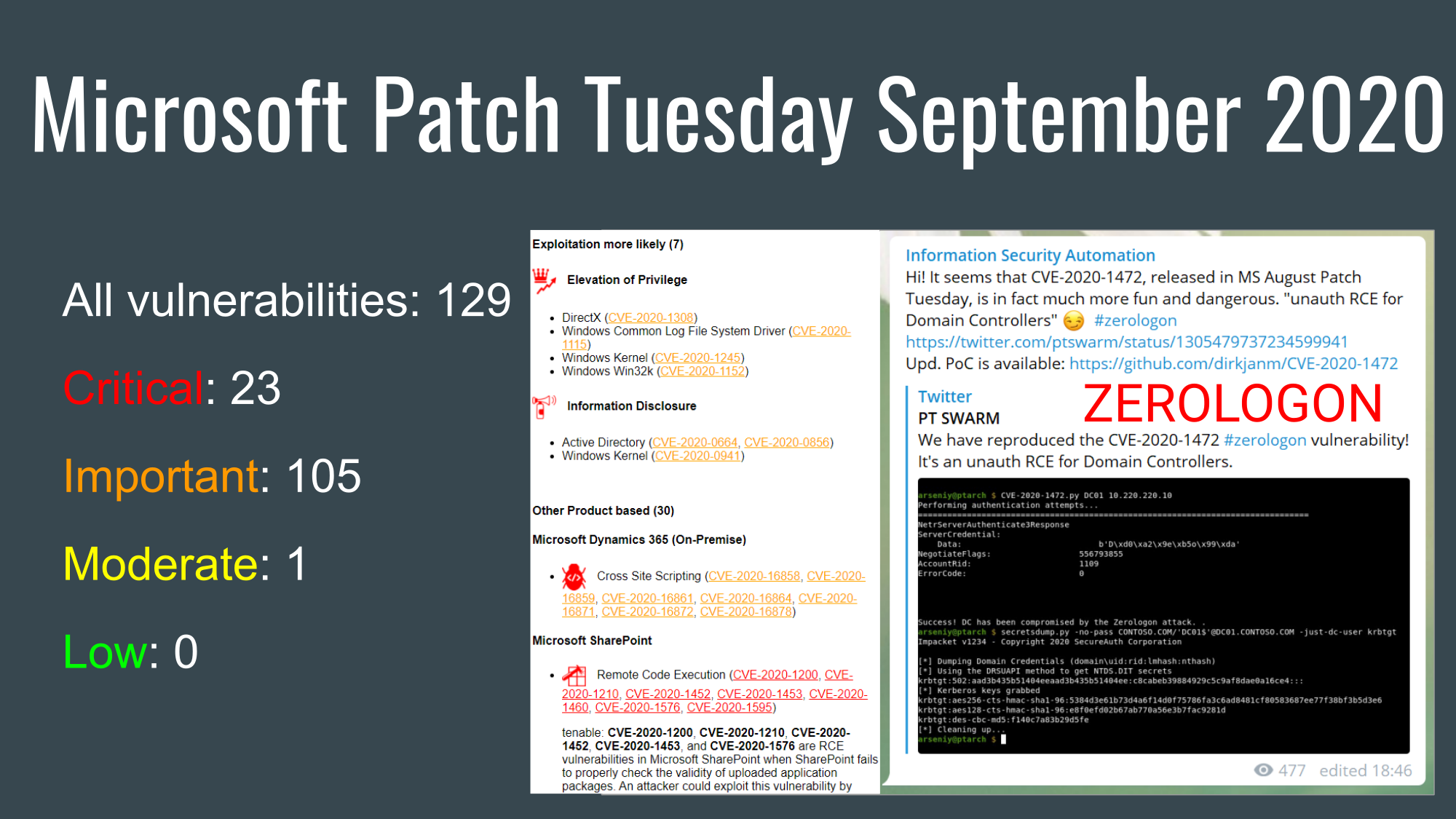
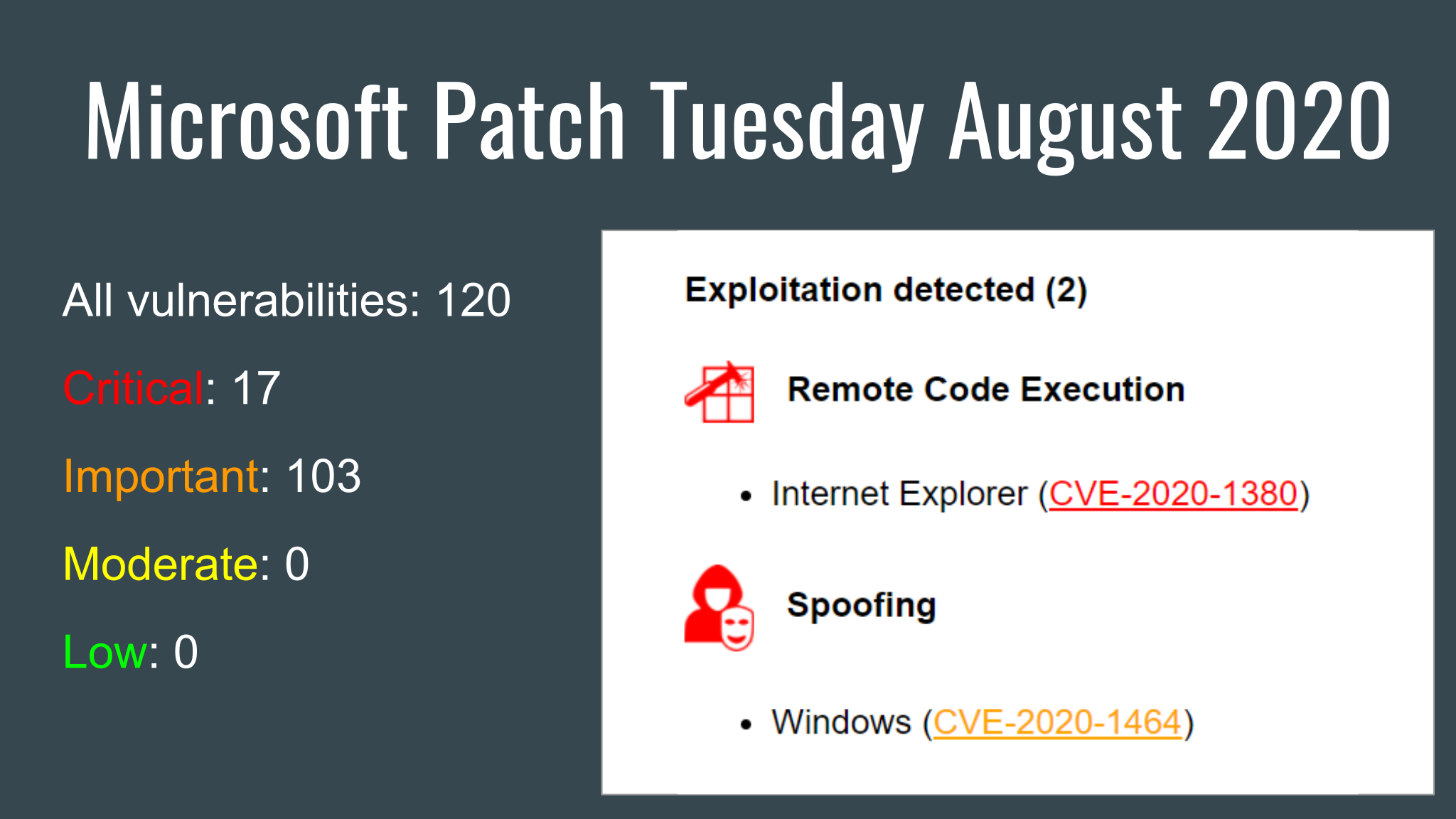
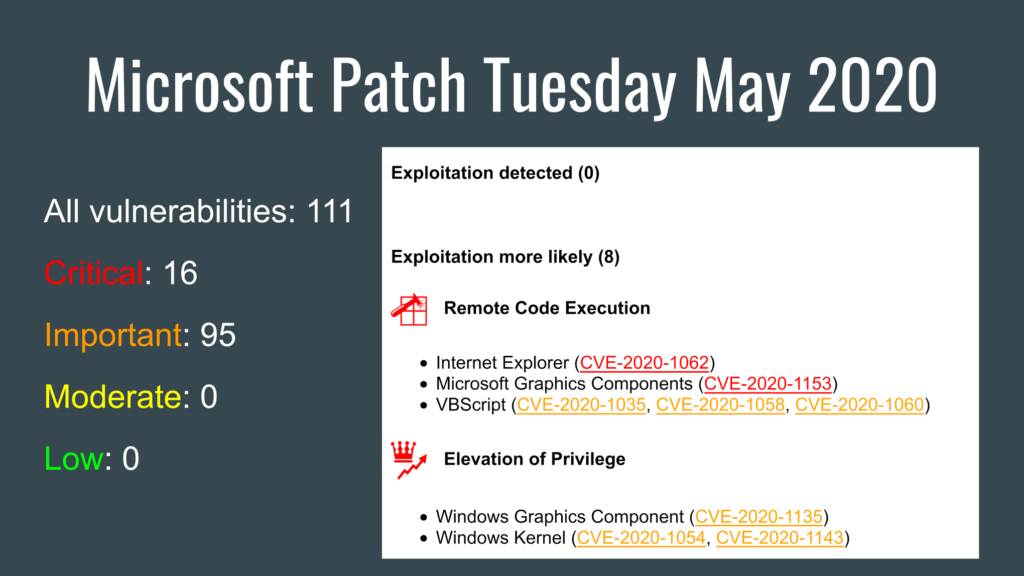
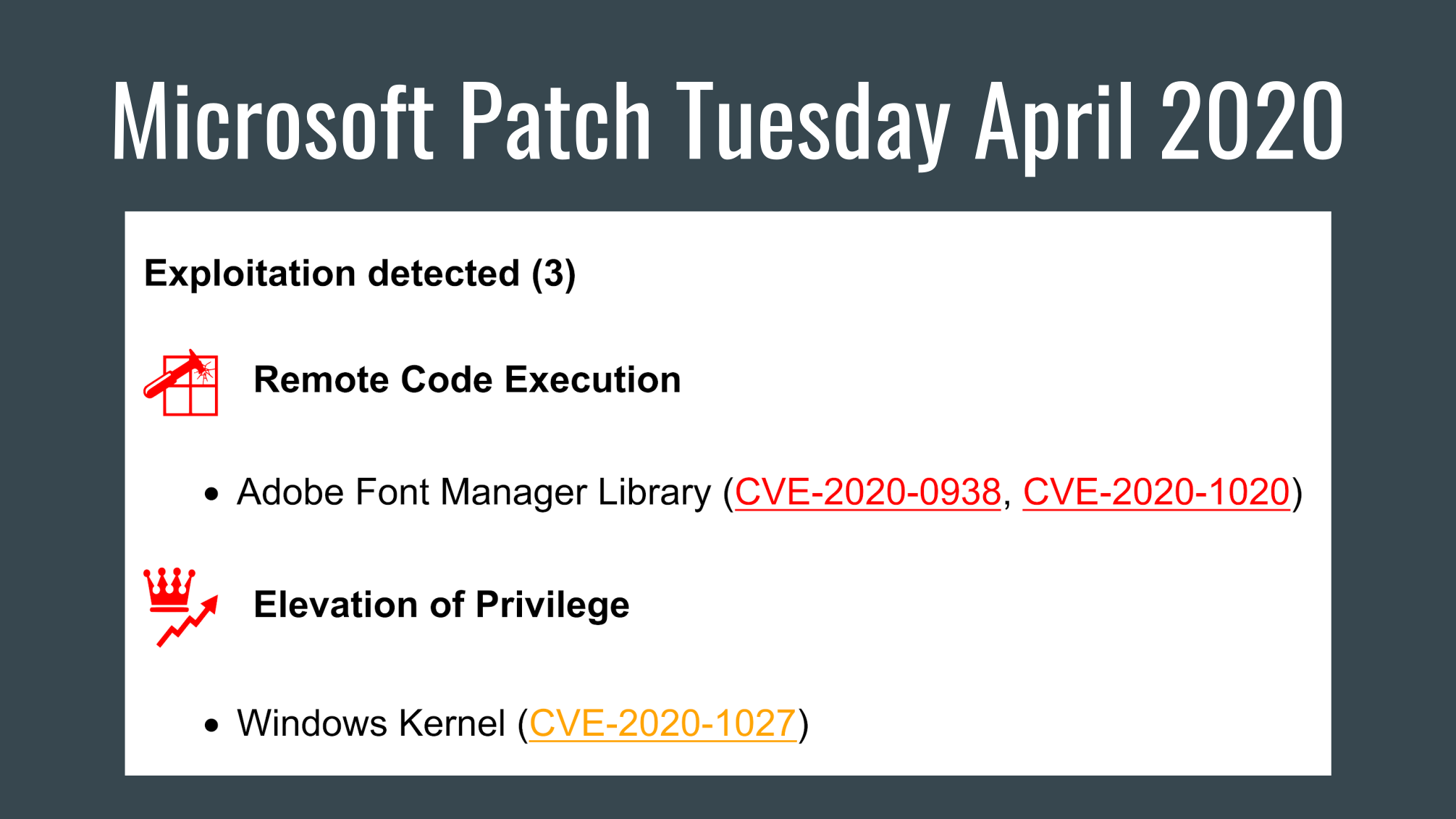
Hi guys! I was on vacation this week. So I had time to work on my Vulristics project. For those who don’t know, this is a framework for prioritizing known CVE vulnerabilities. I was mainly grooming the HTML report.
I added a logo at the top, set a max width for the report, added a timestamp when the report was created so you can now see how fresh it is. I have combined CVSS and Vulristics score statistics in two parallel columns.
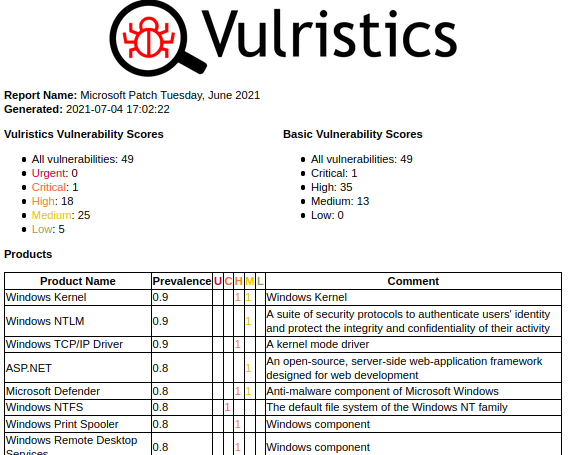
But the main new feature is the tables of vulnerable products and types of vulnerabilities. The products are sorted by “prevalence”. You can review this list and ask yourself if this order is correct in your opinion or change the “prevalence” values for some products in the config dictionary. For software products with unknown “prevalence”, you will see the comment “Unclassified Product”.
Continue reading