Microsoft Patch Tuesday April 2020: my classification script, confusing RCE in Adobe Type Manager and updates for older vulnerabilities. Making the reviews of Microsoft Patch Tuesday vulnerabilities should be an easy task. All vulnerability data is publicly available. Even better, dozens of reviews have already been written. Just read them, combine and post. Right?
Not really. In fact it is quite boring and annoying. It may be fun to write about vulnerabilities that were already used in some real attacks. But this is a very small part of all vulnerabilities. What about more than a hundred others? They are like “some vulnerability in some component may be used in some attack (or may be not)”. If you describe each of them, no one will read or listen this.
You must choose what to highlight. And when I am reading the reports from Tenable, Qualys and ZDI, I see that they choose very different groups of vulnerabilities, pretty much randomly.
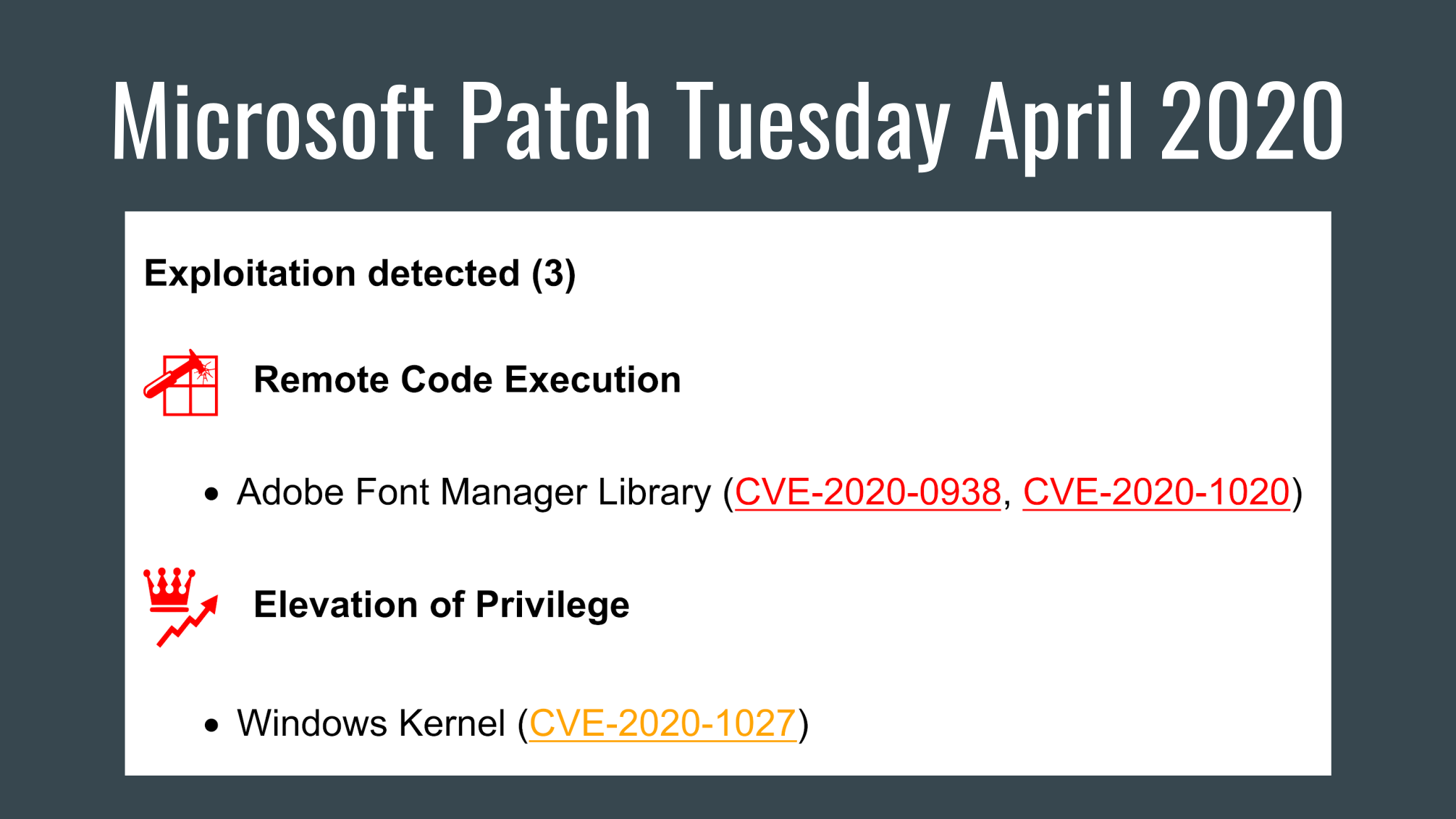
My classification script
That’s why I created a script that takes Patch Tuesday CVE data from microsoft.com and visualizes it giving me helicopter view on what can be interesting there. With nice grouping by vulnerability type and product, with custom icons for vulnerability types, coloring based on severity, etc.