Detectify Asset Inventory and Monitoring. Continuing the topic about perimeter services. As I mentioned earlier, I don’t think that the external perimeter services should be considered as a fully functional replacement for custom Vulnerability Management processes. I would rather see their results as an additional feed showing the problems your current VM process has. Recently I tested the Detectify’s Asset Inventory (Monitoring) solution, which provides such feed by automatically detecting the issues with your second, third (and more) leveled domains and related web services.
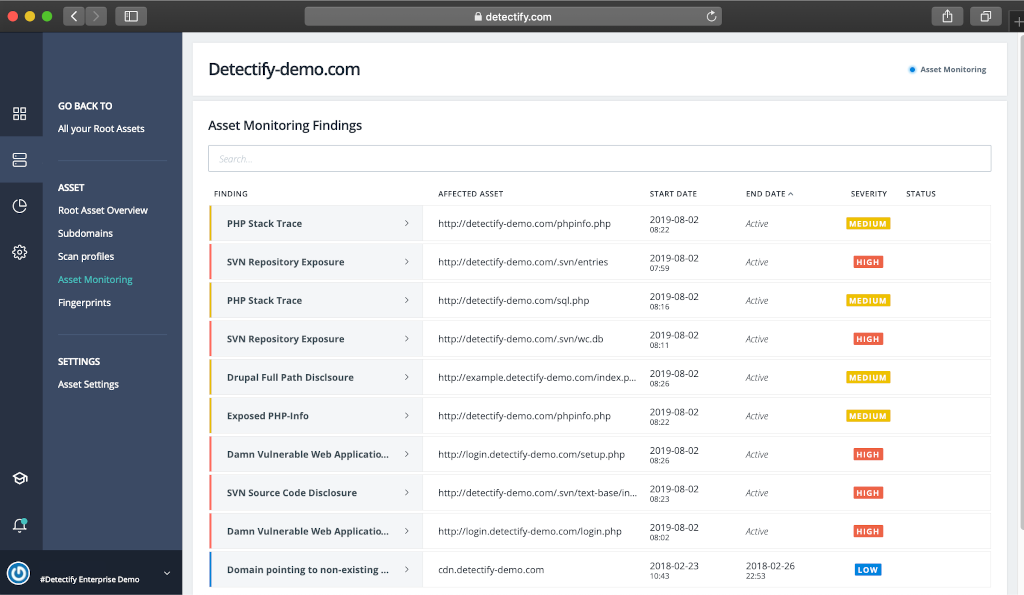
Let say your organization has several second level web domains, over9000 third (and more) level domains, and you even don’t know for what services they are used. This is a normal situation for a large organization. So, you simply add yourorganization.com to Detectify, activate Asset Monitoring, and Detectify automatically discovers third (and more) level domains and related technologies: web services, CMS, JavaScript frameworks and libraries. “It provides thousands of fingerprints and hundreds of tests for stateless vulnerabilities such as code repository exposure for SVN or Git.” This is called fingerprinting.