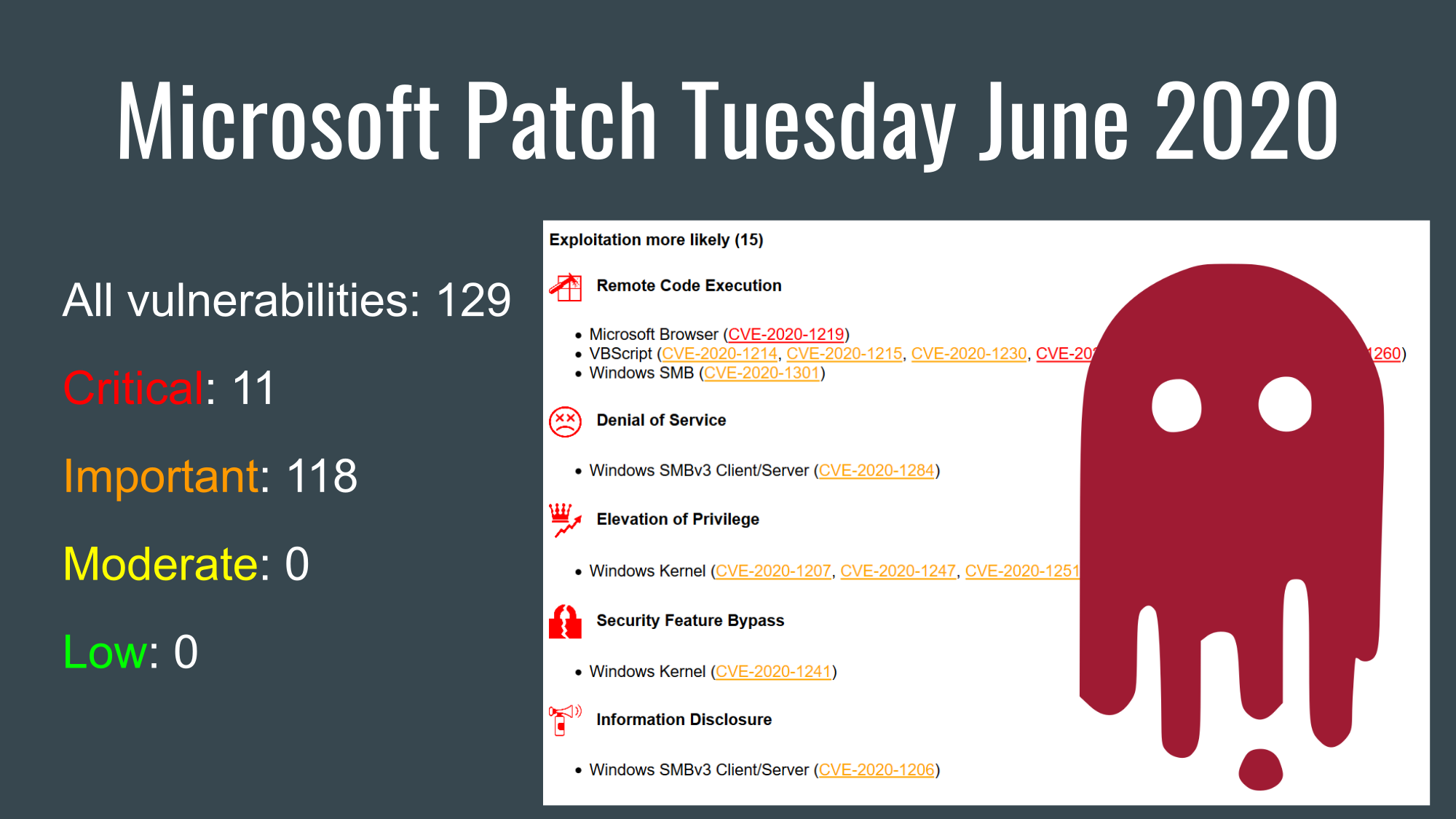
Microsoft Patch Tuesday December 2022: SPNEGO RCE, Mark of the Web Bypass, Edge Memory Corruptions. Hello everyone! This episode will be about Microsoft Patch Tuesday for December 2022, including vulnerabilities that were added between November and December Patch Tuesdays. As usual, I use my open source Vulristics project to analyse and prioritize vulnerabilities.
Alternative video link (for Russia): https://vk.com/video-149273431_456239112
But let’s start with an older vulnerability. This will be another example why vulnerability prioritization is a tricky thing and you should patch everything. In the September Microsoft Patch Tuesday there was a vulnerability Information Disclosure – SPNEGO Extended Negotiation (NEGOEX) Security Mechanism (CVE-2022-37958), which was completely unnoticed by everyone. Not a single VM vendor paid attention to it in their reviews. I didn’t pay attention either.