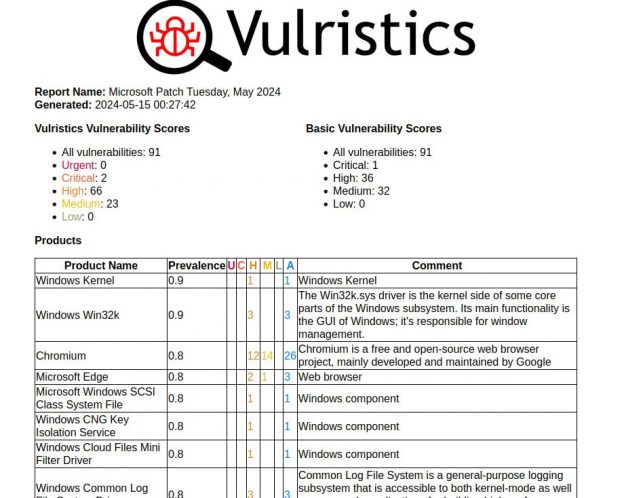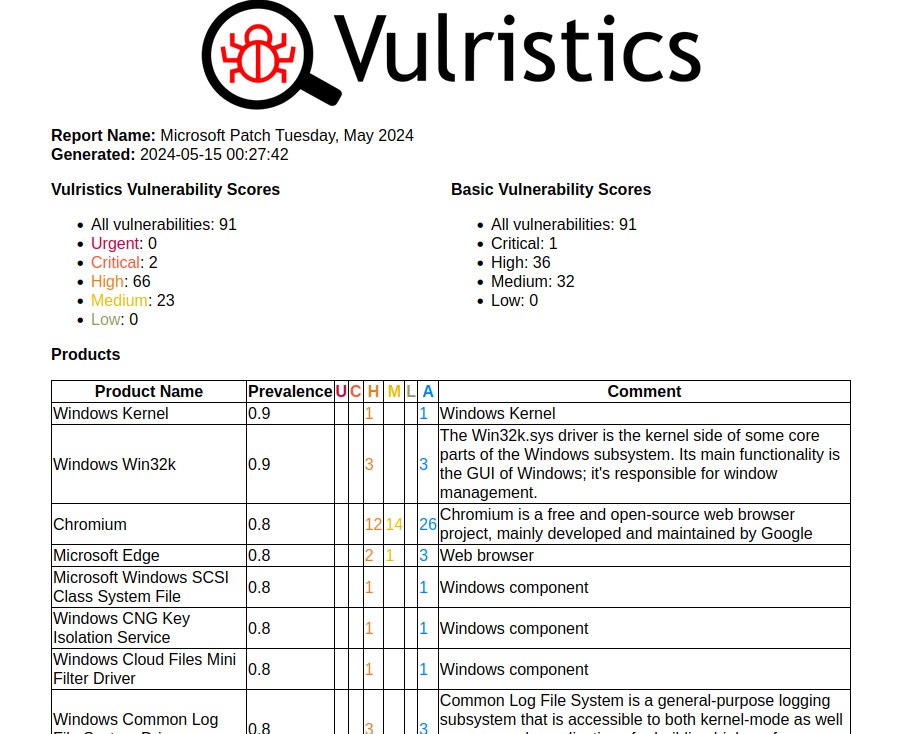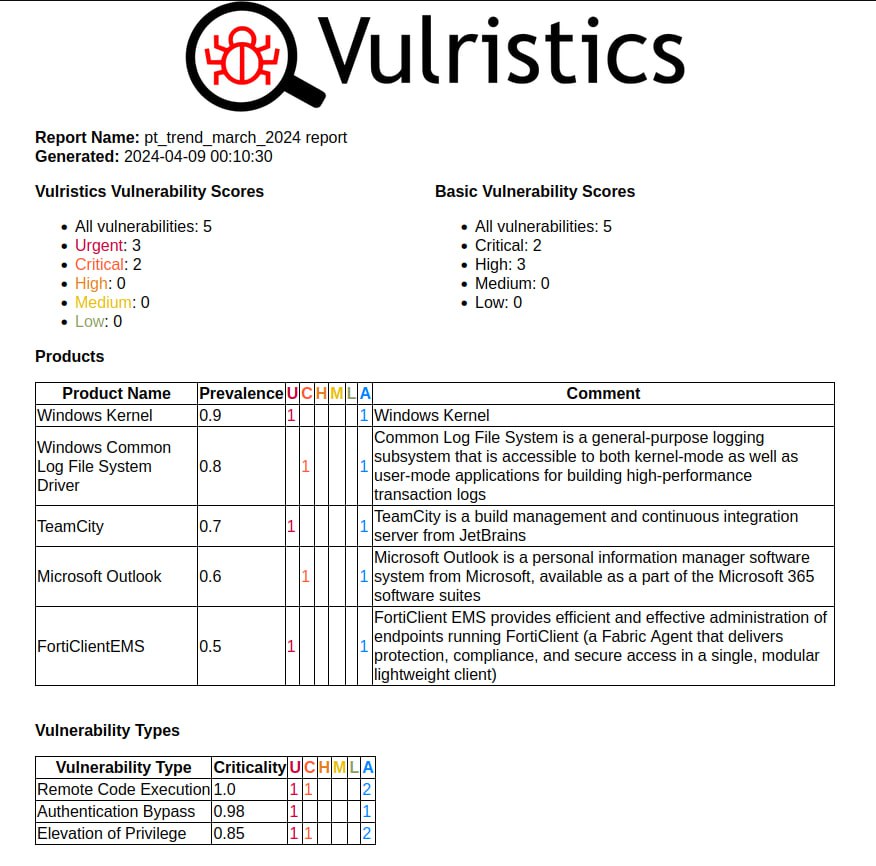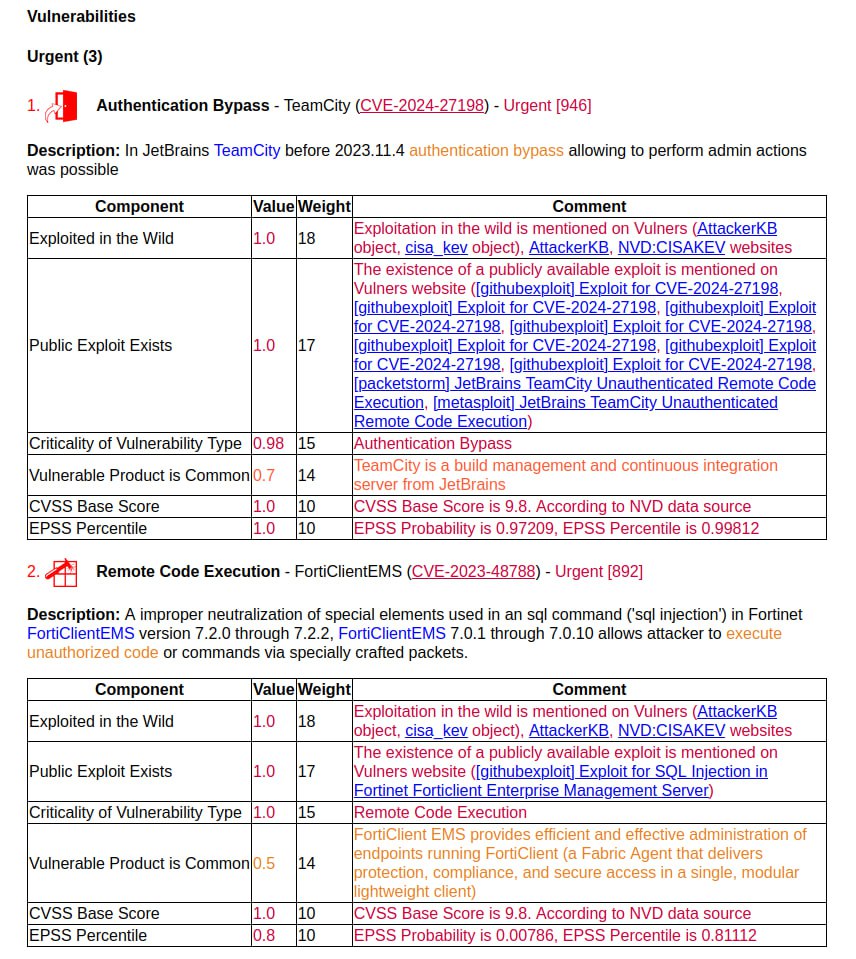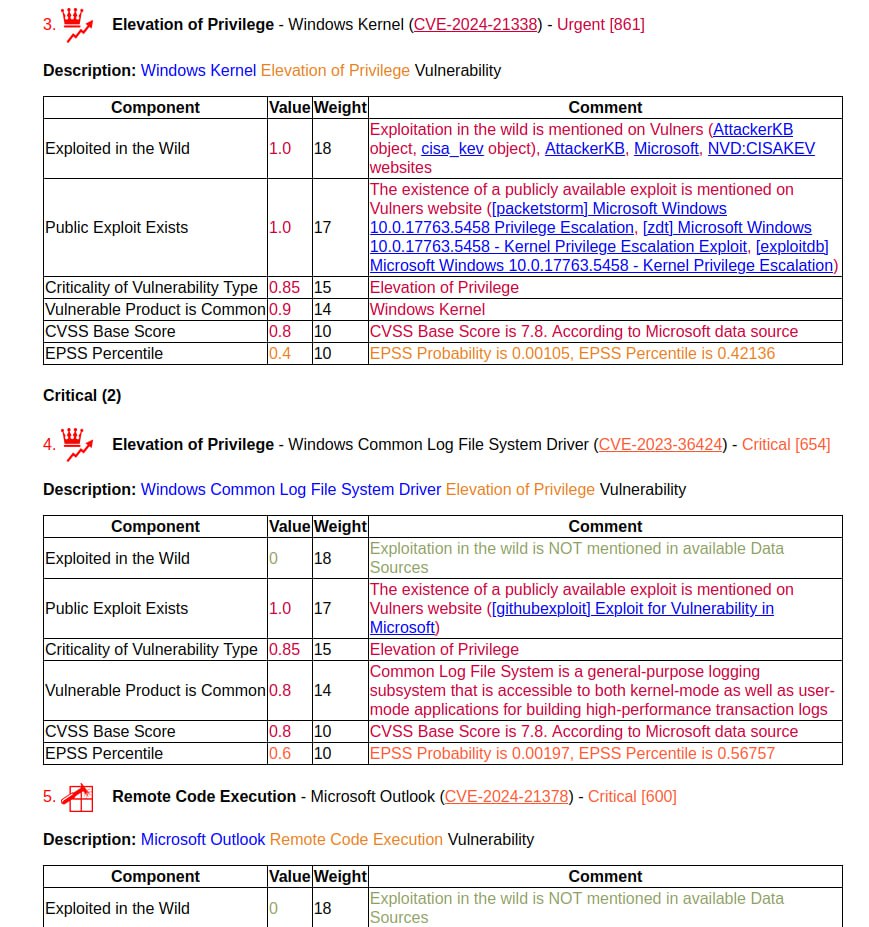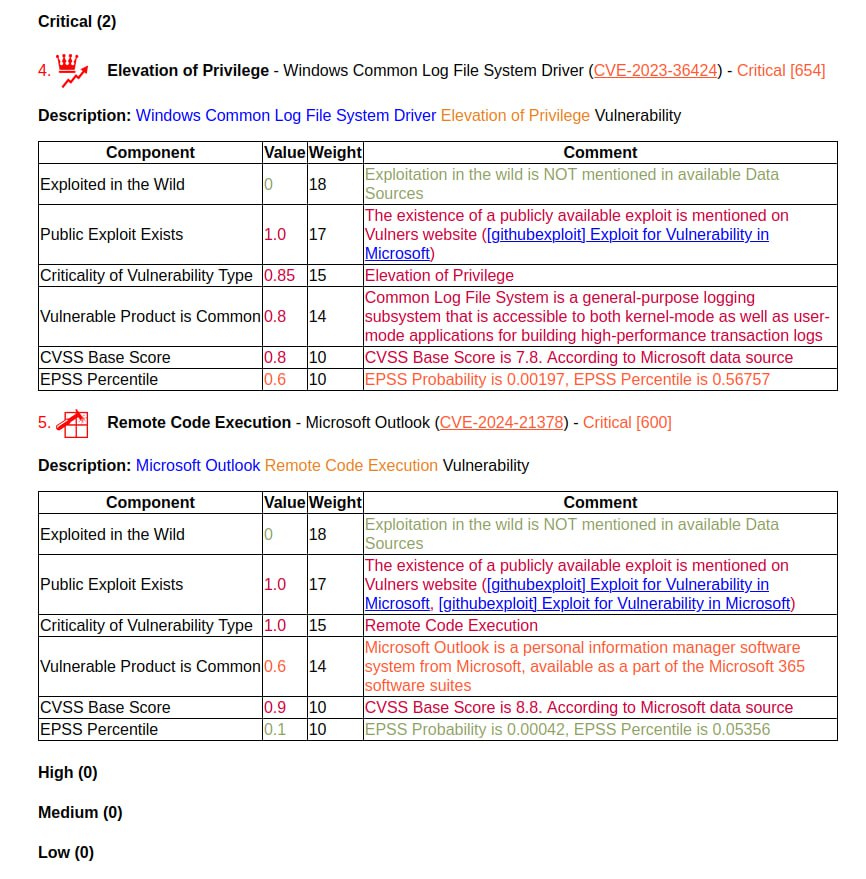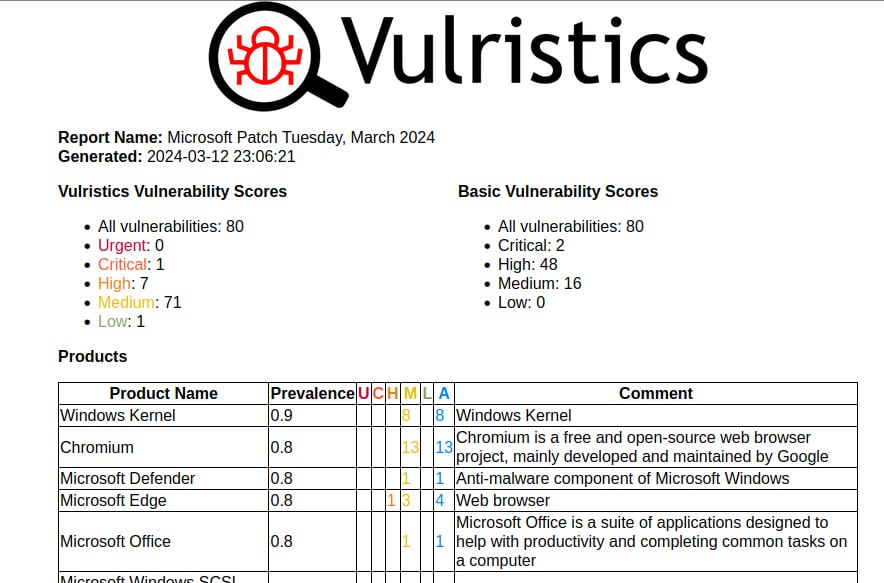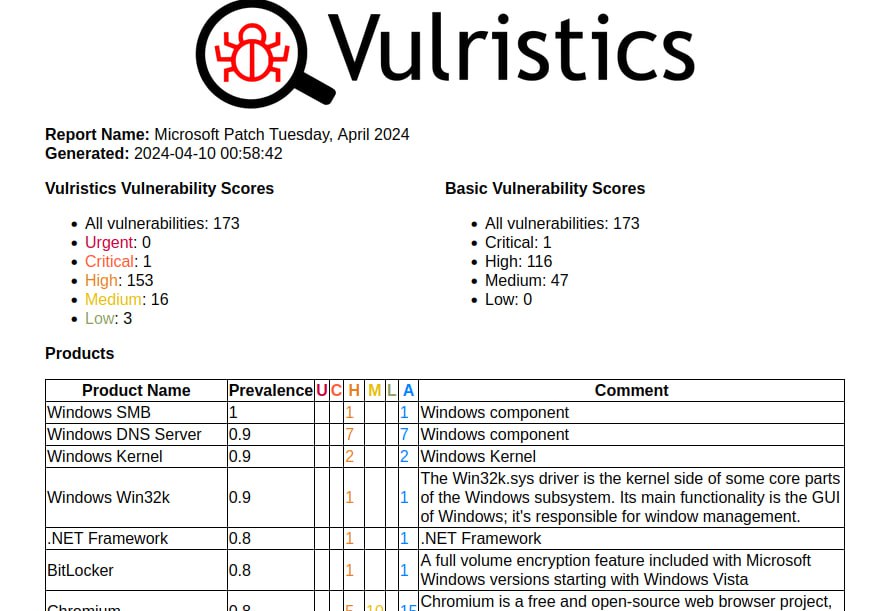

First impressions of the April Microsoft Patch Tuesday. I don’t even know what to write. 🤪 Very strange! 173 vulnerabilities, of which 23 were added since the last Patch Tuesday.
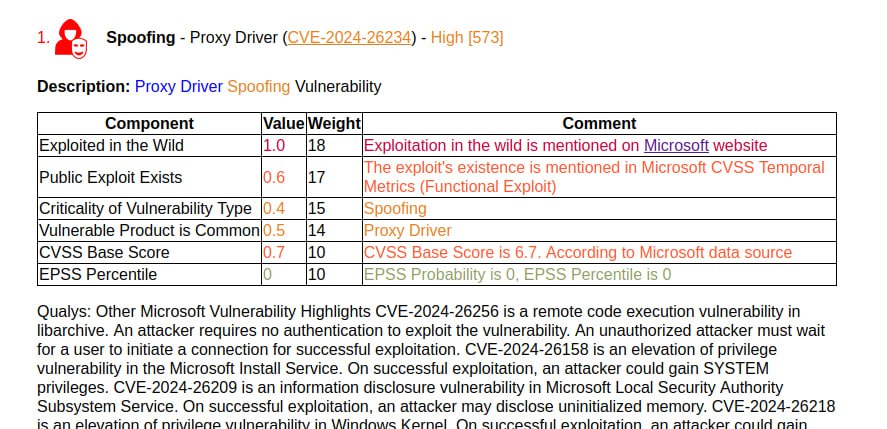
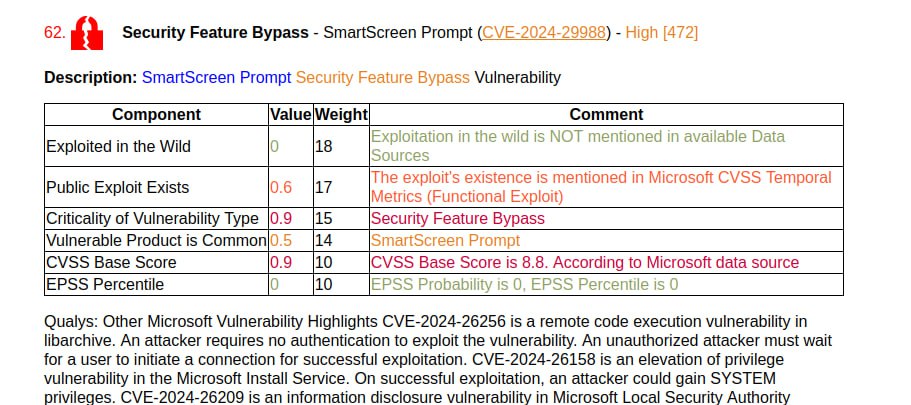
Microsoft flags one vulnerability as being exploited in the wild: Spoofing – Proxy Driver (CVE-2024-26234). And only Qualys briefly mentions it. Literally like this: “Microsoft has not disclosed any information about the vulnerability”. 😅 ZDI also claims that Security Feature Bypass – SmartScreen Prompt (CVE-2024-29988) is being exploited in the wild, which is a Mark of the Web (MotW) bypass.
There are no exploits for anything yet. The following vulnerabilities can be highlighted:
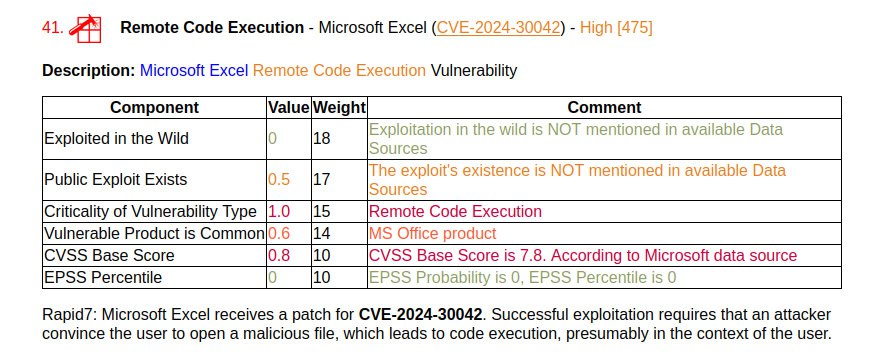
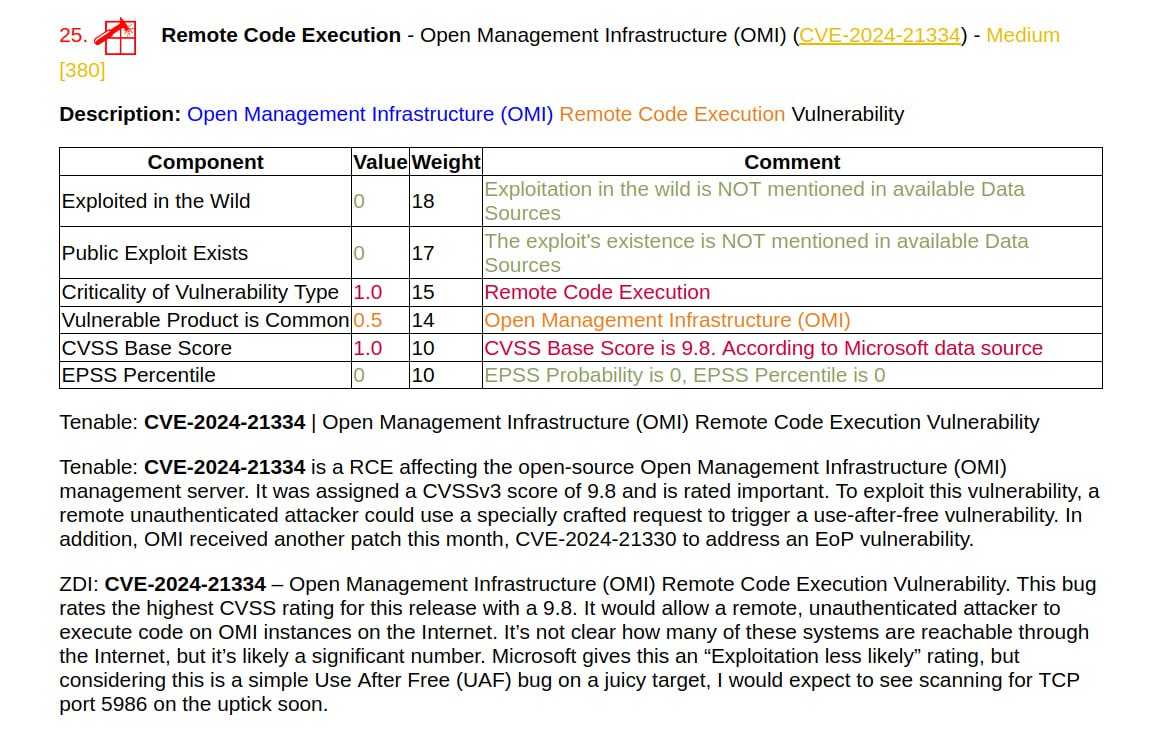
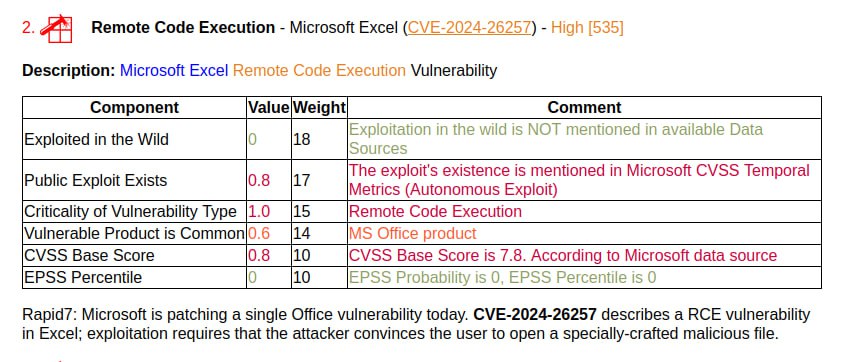
🔸 Remote Code Execution – Microsoft Excel (CVE-2024-26257). Can be exploited by an attacker when the victim opens a specially crafted file.
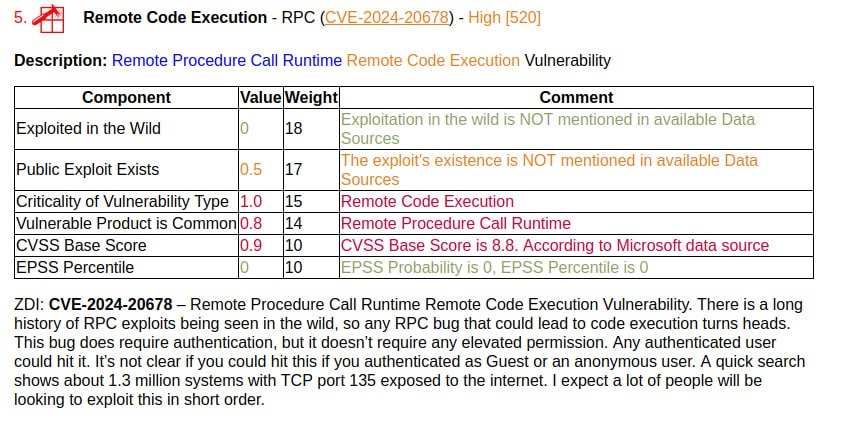
🔸 Remote Code Execution – RPC (CVE-2024-20678). It is highlighted by ZDI, which also claims 1.3 million exposed TCP 135 ports.
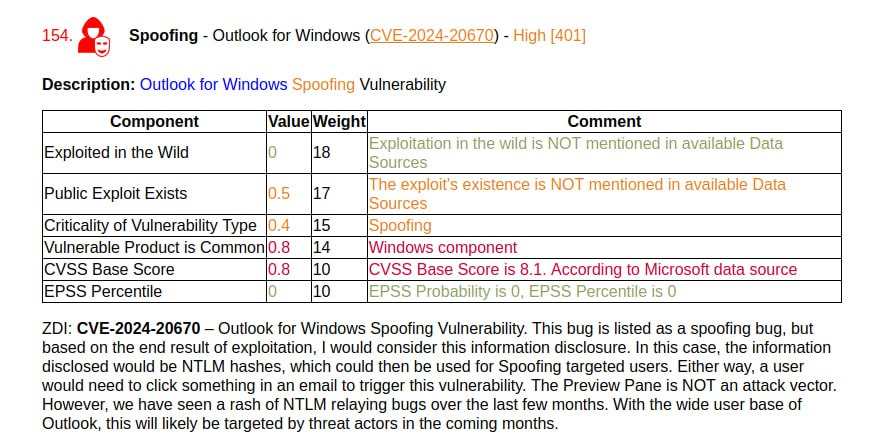
🔸 Spoofing – Outlook for Windows (CVE-2024-20670). ZDI writes that this is an Information Disclosure vulnerability that can be used in NTLM relay attacks.
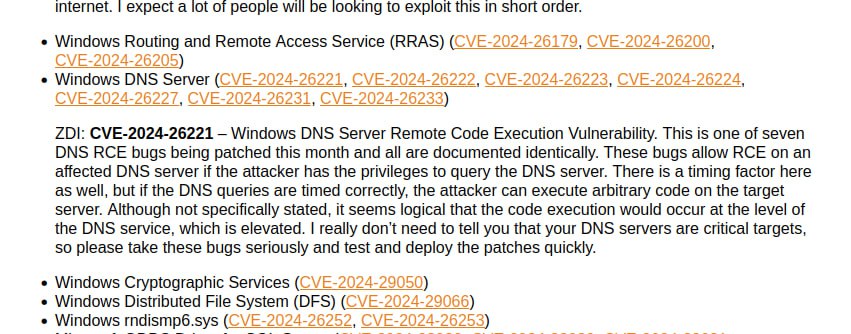
🔸 Remote Code Execution – Windows DNS Server (CVE-2024-26221, CVE-2024-26222, CVE-2024-26223, CVE-2024-26224, CVE-2024-26227, CVE-2024-26231, CVE-2024-26233). Maybe some of this will be exploited in the wild, ZDI particularly highlights CVE-2024-26221.
🔸 Remote Code Execution – Microsoft Defender for IoT (CVE-2024-21322, CVE-2024-21323, CVE-2024-29053). It is an IoT and ICS/OT security solution that can be deployed on-prem.
There are simply indecently massive fixes:
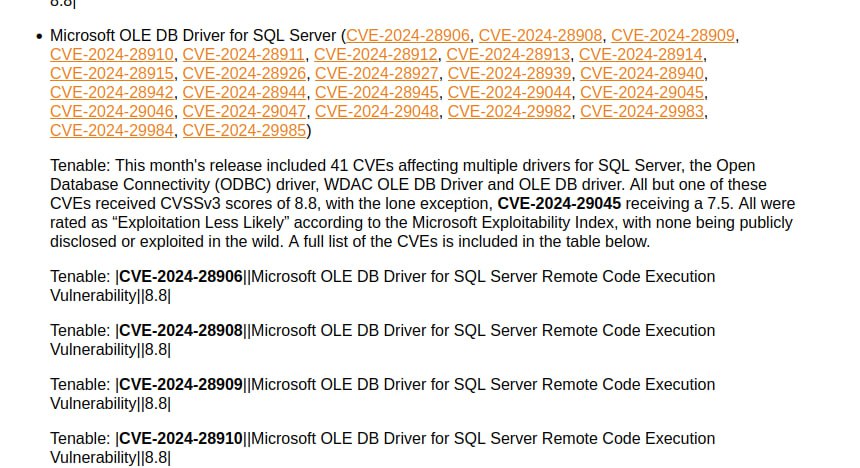
🔹 Remote Code Execution – Microsoft OLE DB Driver for SQL Server / Microsoft WDAC OLE DB Provider for SQL Server / Microsoft WDAC SQL Server ODBC Driver. 28 CVEs! I won’t even list everything here. 😨
🔹 Security Feature Bypass – Secure Boot. 23 CVEs!
🗒 Vulristics report
На русском
Upd. 10.04 I slightly tweaked the vulnerability type detection to increase the priority of the detection based on the Microsoft generated description compared to the detection based on CWE. In particular, the type of vulnerability for Spoofing – Proxy Driver (CVE-2024-26234) and Spoofing – Outlook for Windows (CVE-2024-20670) has changed.