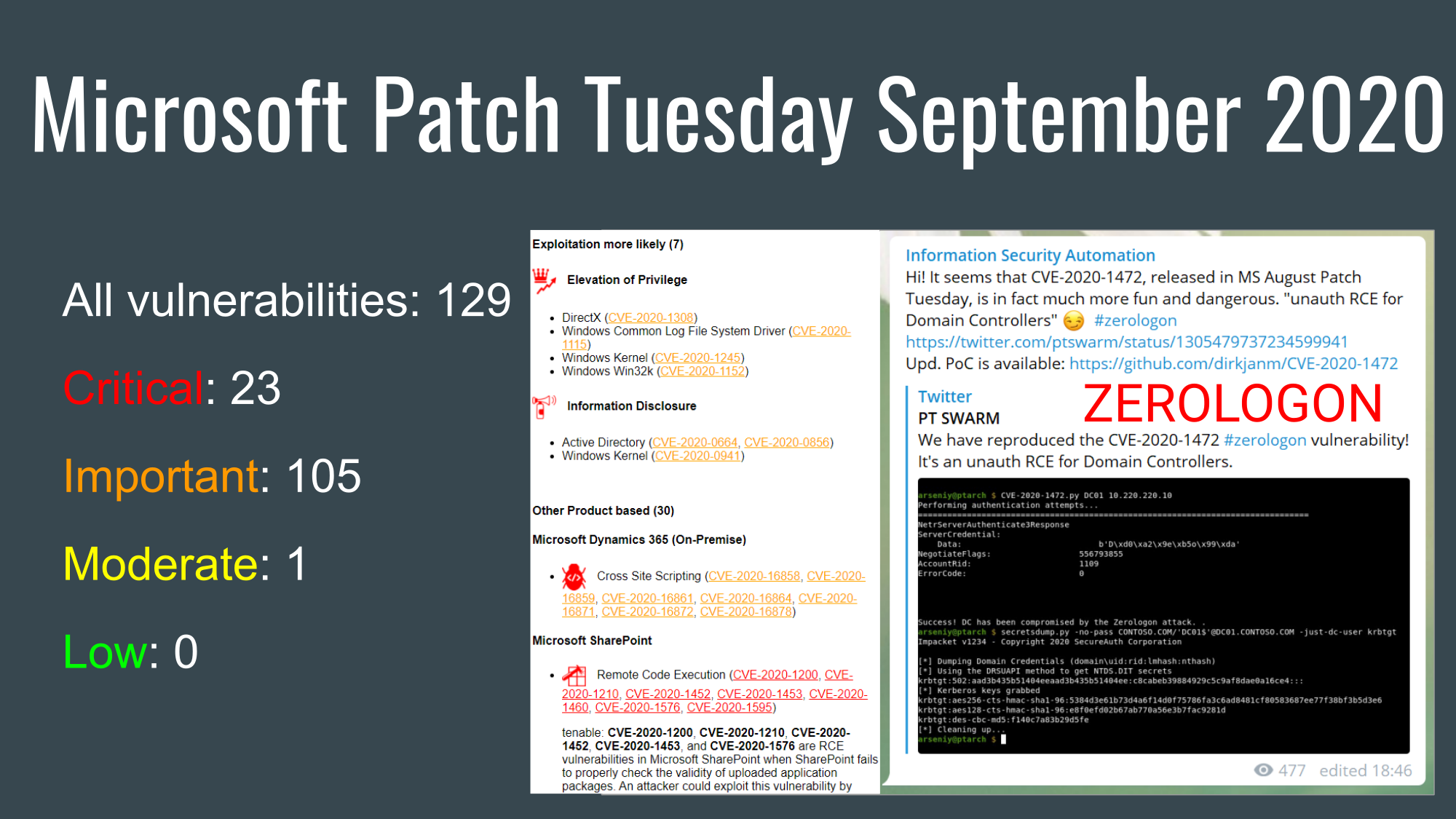
Asset Inventory for Network Perimeter: from Declarations to Active Scanning. In the previous post, I shared some of my thoughts about the good Asset Inventory system. Of course, for me as a Security Specialist, it would be great if IT will provide such magical system. 🙂 But such an ideal situation is rarely possible. So now let’s see how to build an Asset Inventory system using the resources of Information Security team.
There are no special secrets. It’s necessary to get information about the assets from all available IT systems and then get the rest of the data using our own Assessment tools. I would like to start with hosts on Network Perimeter. The Network Perimeter targets are available at any time for hacker attacks, that’s why this part of the network is the most critical.
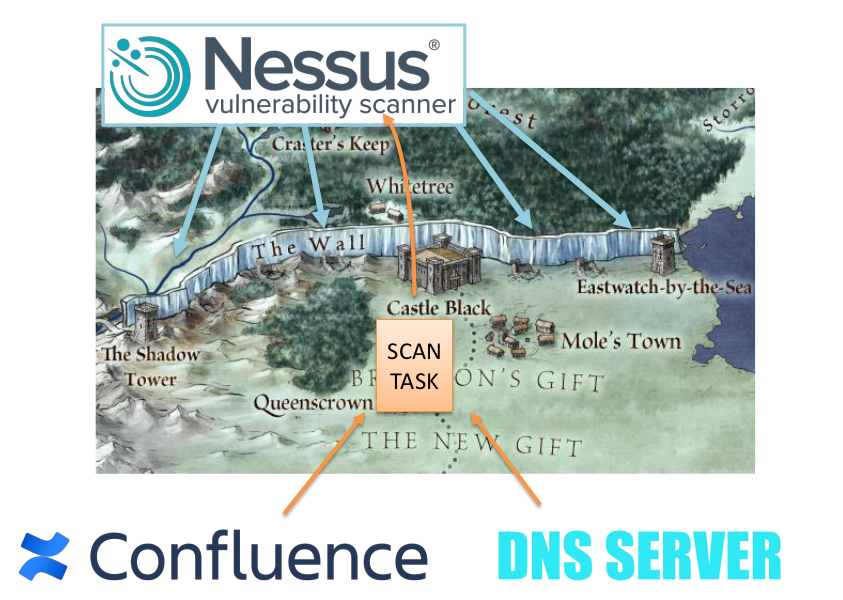
Network Perimeter is like the Wall in the Game of Thrones. The same white walkers are hiding behind the wall and our task is to find the breaches in the wall faster than potential intruders. “Night gathers, and now my watch begins”. (c)
Perimeter is changing constantly. And we should understand at any time what hosts are currently exposed in every office and every external hosting platform.
We can get information about external hosts using some Vulnerability Scanner located on external host in the Internet. I have already wrote about it briefly in Vulnerability Management for Network Perimeter. Here I would like focus on how we can understand which hosts should be scanned and what useful information we can get from the raw scan results.
Continue reading →