New Nessus 7 Professional and the end of cost-effective Vulnerability Management (as we knew it). It’s an epic and really sad news. 🙁

When people asked me about the cost-effective solution for Vulnerability Management I usually answered: “Nessus Professional with some additional automation through Nessus API”.
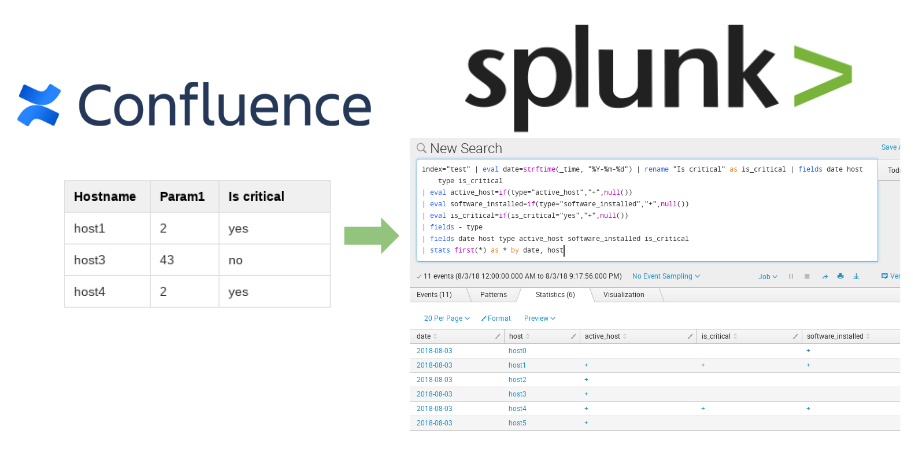
With just a couple of Nessus Professional scanning nodes it was possible to scan all the infrastructure and network perimeter (see “Vulnerability Management for Network Perimeter“). Price for each node was fixed and reasonable. And you could make your any reports from the raw scan data, as you like it.
Nessus Pro was still were best choice even when Tenable:
- Cut off master/slave functionality in Nessus and created “Nessus Manager”.
- Changed API completely during the update from 5 to 6 version.
- Gradually increased the price from $1,5k to $2,7k per scanning node per year.
But unfortunately it’s not anymore. End of an era.
And what is even more sad is that Tenable does not mention disabling the API and multi-user function in the main Nessus 7 marketing, as it never was, as if it’s not very important. Just look at “Announcing Nessus Professional v7” – not a word about “API” or users. Only in additional link:
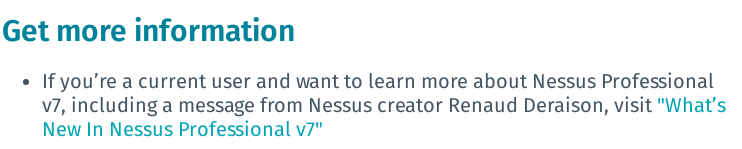
Only there, in the text (not a video) there is an information about removed features.
The nice little things like “Easily transferable license” and “Emailed scan reports and custom report name / logo” do not make it any better.
So, what next?
Continue reading →