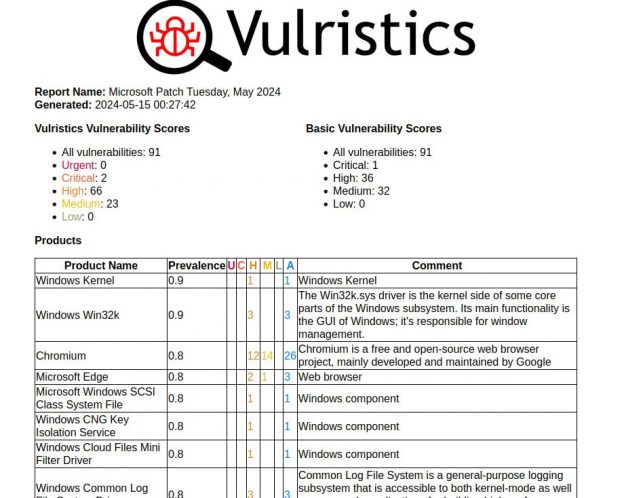
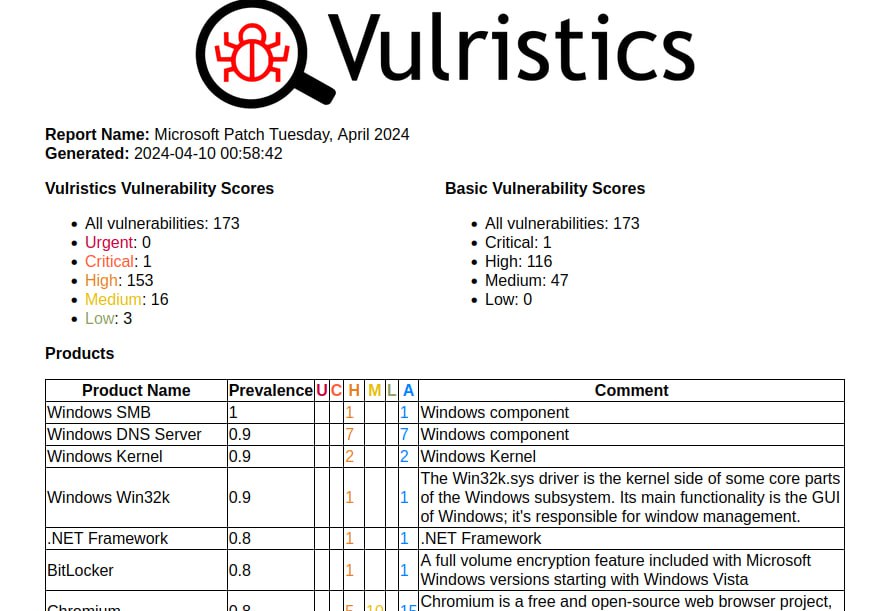
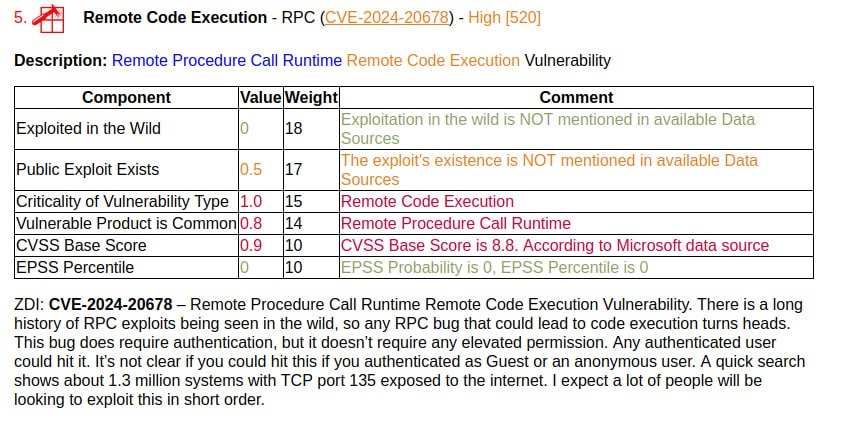
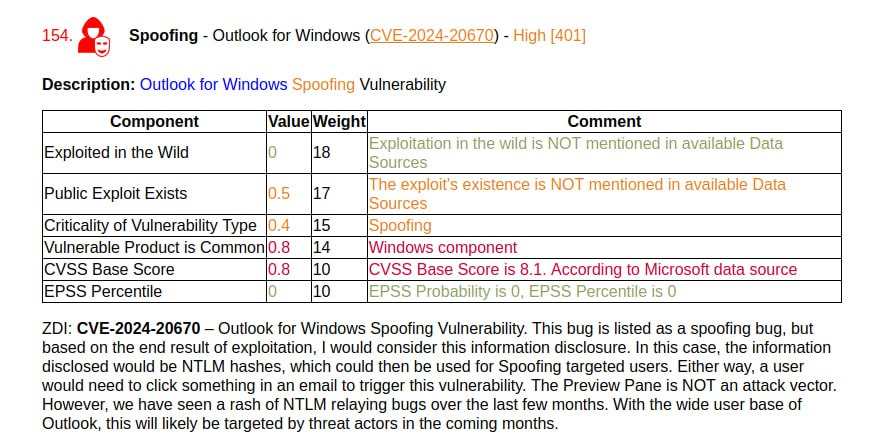
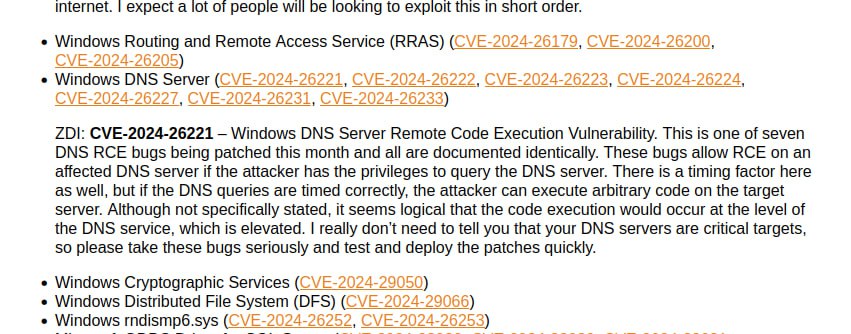
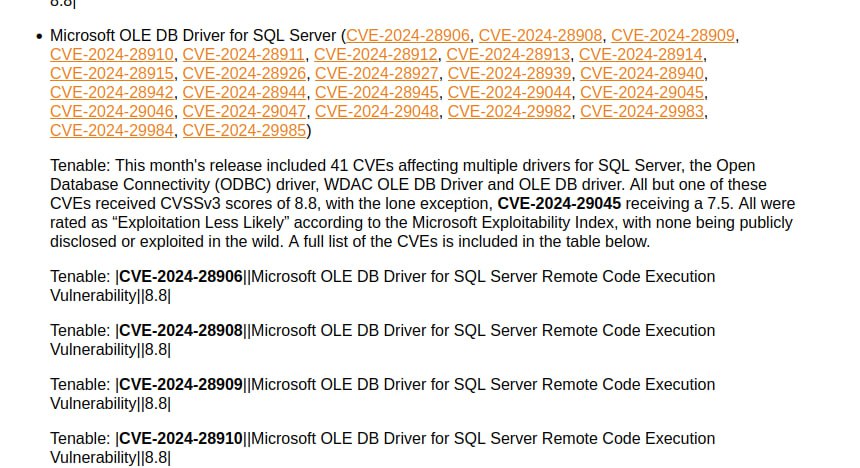
May Microsoft Patch Tuesday. There are 91 vulnerabilities in total. Of those, 29 were added between April and May Patch Tuesday.
Two vulnerabilities have signs of exploitation in the wild and the presence of a functional exploit (not yet public):
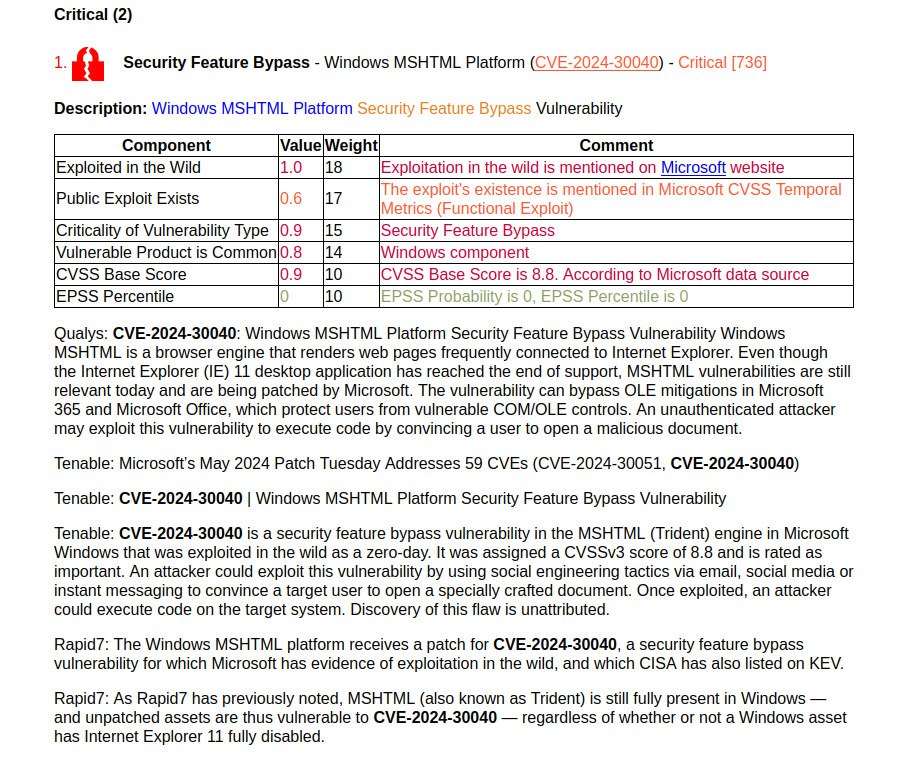
🔻 Security Feature Bypass – Windows MSHTML Platform (CVE-2024-30040). In fact, an attacker can execute arbitrary code when the victim opens a specially crafted document. It is exploited through phishing.
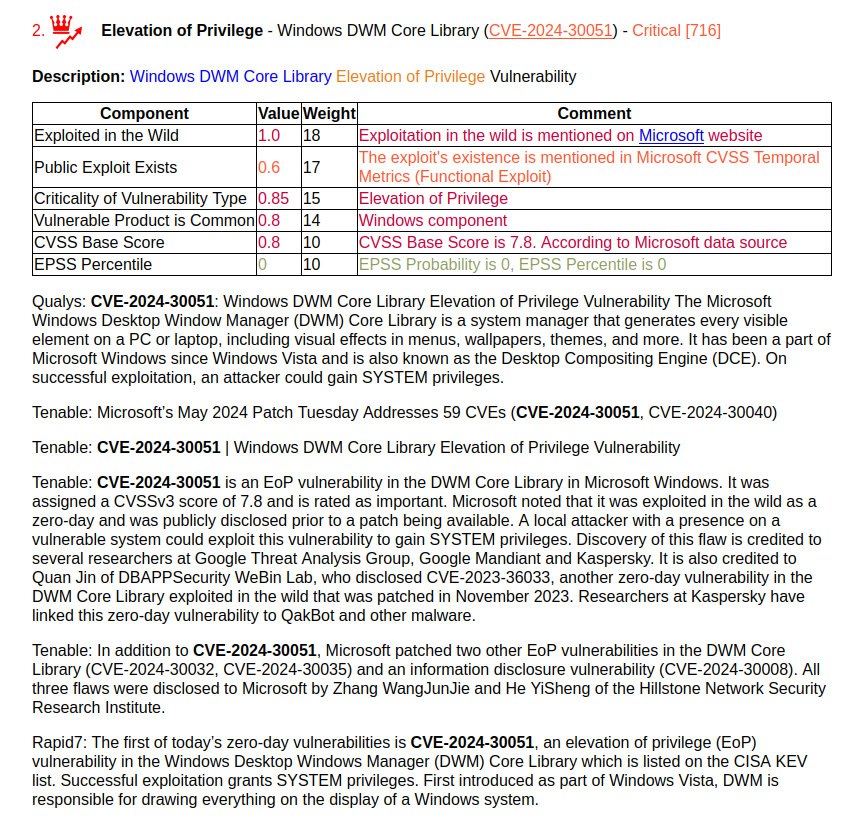
🔻 Elevation of Privilege – Windows DWM Core Library (CVE-2024-30051). A local attacker can gain SYSTEM privileges on the vulnerable host. Microsoft credits four different groups for reporting the bug, indicating that the vulnerability is being widely exploited. The vulnerability is associated with the QakBot malware.
Among the rest we can note:
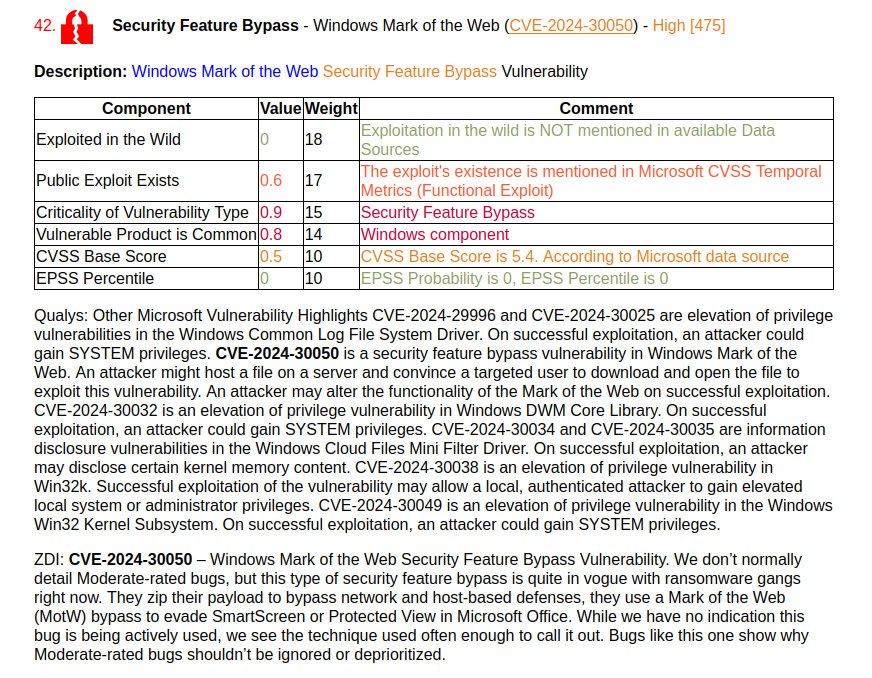
🔸 Security Feature Bypass – Windows Mark of the Web (CVE-2024-30050). Such vulnerabilities have been frequently exploited recently. Microsoft indicates that there is a functional exploit (private) for the vulnerability.
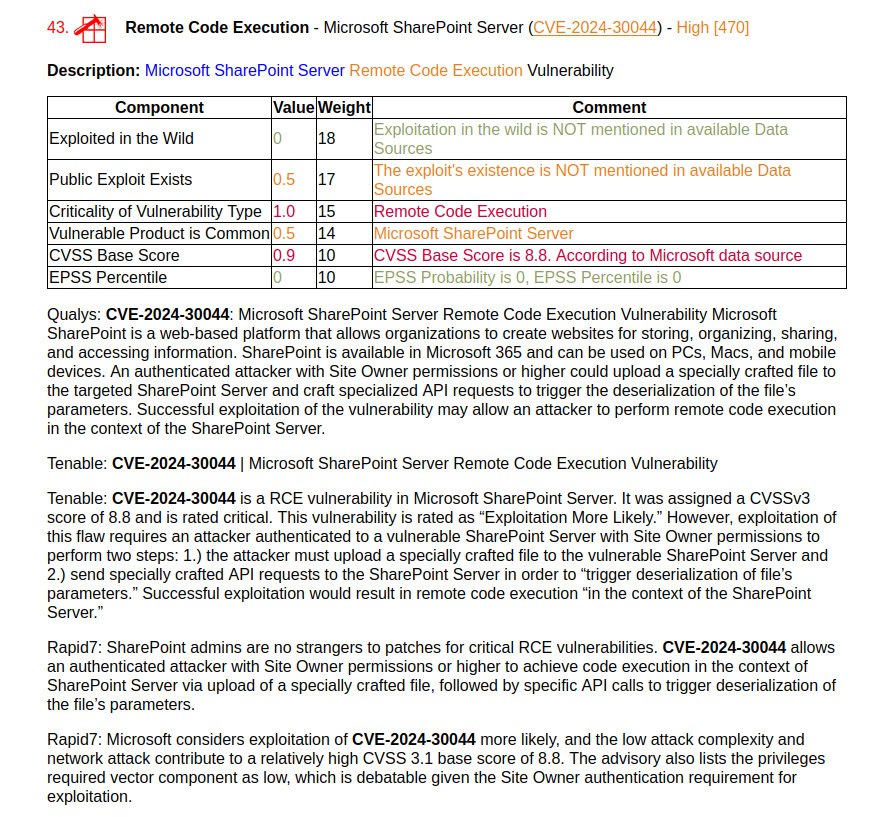
🔸 Remote Code Execution – Microsoft SharePoint Server (CVE-2024-30044). An authenticated attacker with Site Owner privileges or higher can execute arbitrary code in the context of SharePoint Server by uploading a specially crafted file.
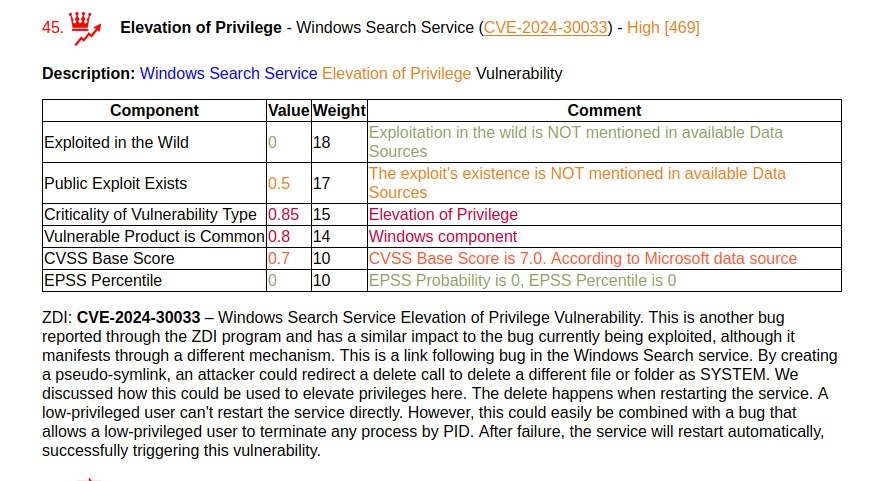
🔸 Elevation of Privilege – Windows Search Service (CVE-2024-30033). ZDI believes that the vulnerability has the potential to be exploited in the wild.
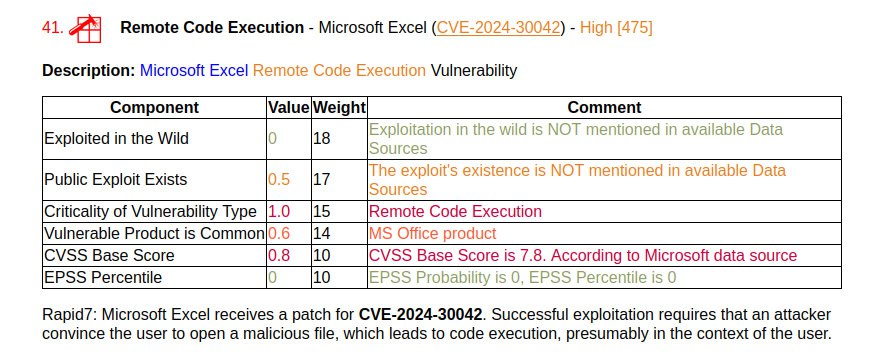
🔸 Remote Code Execution – Microsoft Excel (CVE-2024-30042). An attacker can execute code, presumably in the user’s context, when a malicious file is opened.