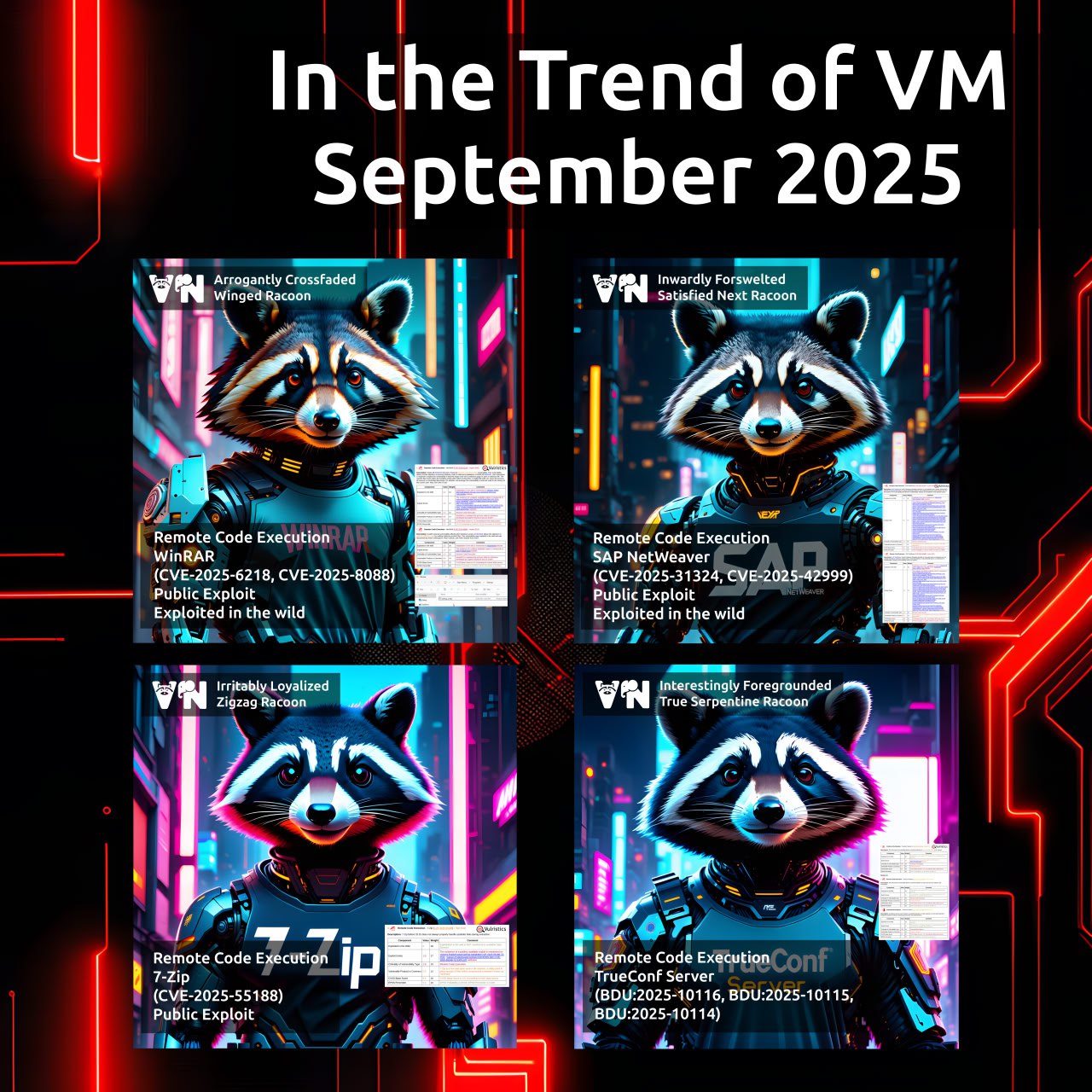
Petya, M.E.Doc and the problem of trust. I’ve already mentioned in “Petya the Great and why *they* don’t patch vulnerabilities“, that NotPetya ransomware seems trivial from Vulnerability Management point of view. It uses known Windows vulnerabilities, that were patched by Microsoft long time ago.
Despite of this, I was really interested in M.E.Doc (servers were confiscated by Ukrainian police and website is not operational) role in the initial phase of malware spreading. In my opinion, we have a pretty interesting example of an attack vector, that will be very hard to detect and mitigate. And moreover, it’s once again shows that protected perimeter won’t be a panacea anymore.
M.E.Doc – My Electronic Document Circulation System. “m.e.doc” sounds like the word, that mean “honey” in Russian and Ukrainian. That’s why all these bees in promo materials.
M.E.Doc is an Document Circulation System very popular in Ukraine. It makes possible to send reports to the government authorities in electronic form. It can be used in any organization. I can even imagine situation when usage of this kind of software may be even mandatory. Now the researchers [Eset, Dr.Web] say that M.E.Doc servers sent updates with backdoors to the customers.
This backdoor has abilities:
- Data collection for accessing mail servers
- Arbitrary commands execution in the infected system
- Running any executables
- Downloading arbitrary files to the infected computer
- Uploading arbitrary files to a remote server
- Identify the exact organization using EDRPOU number.
I don’t really care about technical details about this backdoor. For me it’s enough that malicious code was on official server of the vendor and was spread to legitimate customers. Boom!
Continue reading →