June “In the Trend of VM” (#16): vulnerabilities in Microsoft Windows, Apache HTTP Server, the web interfaces of MDaemon and Zimbra, and the 7-Zip archiver. A traditional monthly vulnerability roundup. 🙂
🗞 Post on Habr (rus)
🗒 Digest on the PT website (rus)
A total of 7 trending vulnerabilities:
🔻 Elevation of Privilege – Microsoft DWM Core Library (CVE-2025-30400)
🔻 Elevation of Privilege – Windows Common Log File System Driver (CVE-2025-32701, CVE-2025-32706)
🔻 Remote Code Execution & Arbitrary File Reading – Apache HTTP Server (CVE-2024-38475)
🔻 Cross Site Scripting – MDaemon Email Server (CVE-2024-11182)
🔻 Cross Site Scripting – Zimbra Collaboration (CVE-2024-27443)
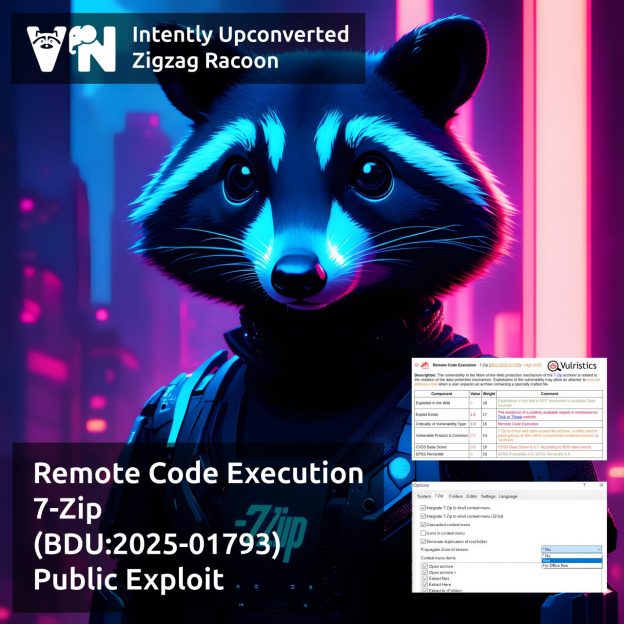
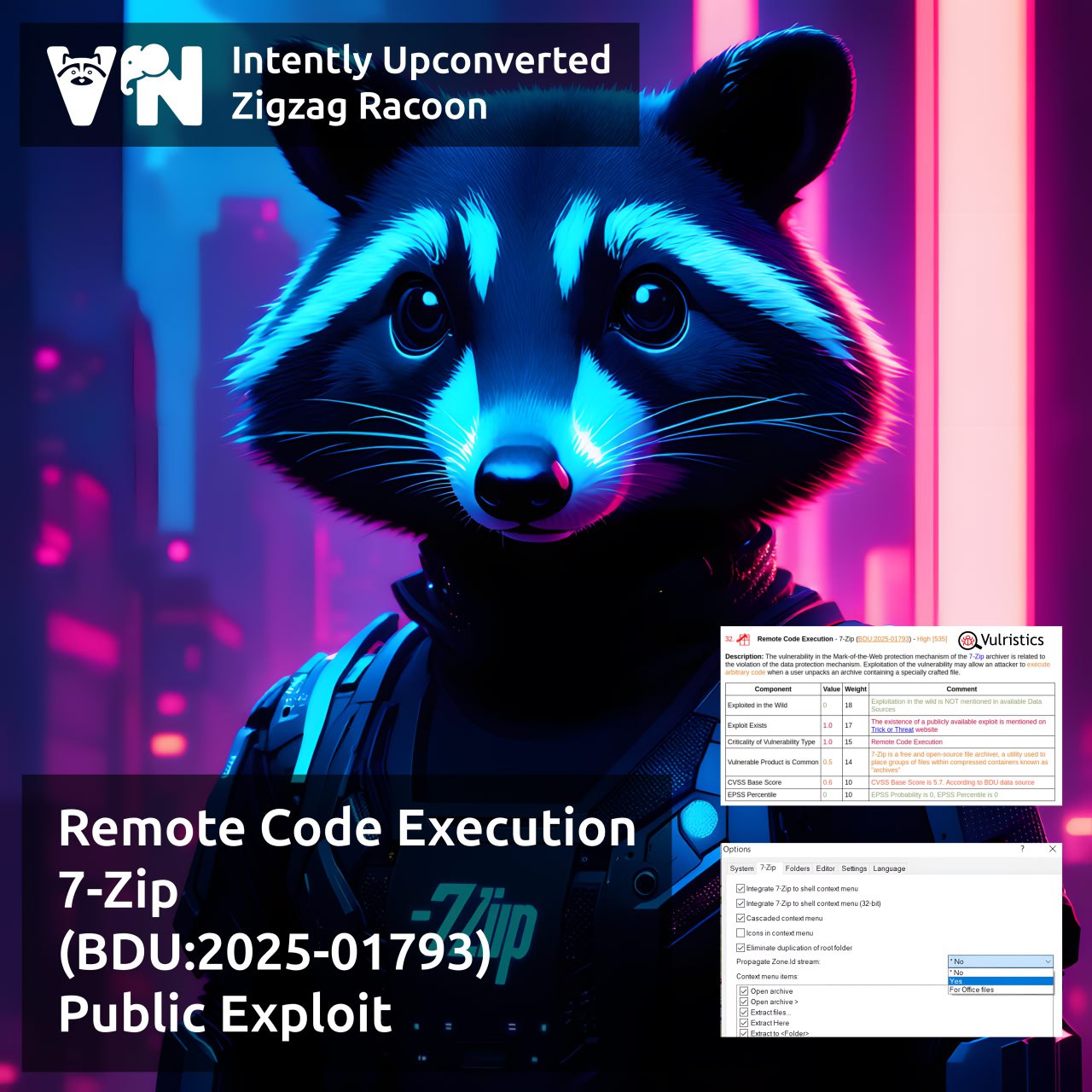
🔻 Remote Code Execution – 7-Zip (BDU:2025-01793)