September episode of “In The Trend of VM”: 7 CVEs, fake reCAPTCHA, lebanese pagers, VM and IT annual bonuses. Starting this month, we decided to slightly expand the topics of the videos and increase their duration. I cover not only the trending vulnerabilities of September, but also social engineering cases, real-world vulnerability exploitation, and practices of vulnerability management process. At the end we announce a contest of questions about Vulnerability Management with gifts. 🎁
📹 Video “In The Trend of VM” on YouTube
🗞 A post on Habr (rus) a slightly expanded script of the video
🗒 A compact digest on the official PT website
Content:
🔻 00:51 Elevation of Privilege – Windows Installer (CVE-2024-38014) and details about this vulnerability
🔻 02:42 Security Feature Bypass – Windows Mark of the Web “LNK Stomping” (CVE-2024-38217)
🔻 03:50 Spoofing – Windows MSHTML Platform (CVE-2024-43461)
🔻 05:07 Remote Code Execution – VMware vCenter (CVE-2024-38812)
🔻 06:20 Remote Code Execution – Veeam Backup & Replication (CVE-2024-40711), while the video was being edited, data about exploitation in the wild appeared
🔻 08:33 Cross Site Scripting – Roundcube Webmail (CVE-2024-37383)
🔻 09:31 SQL Injection – The Events Calendar plugin for WordPress (CVE-2024-8275)
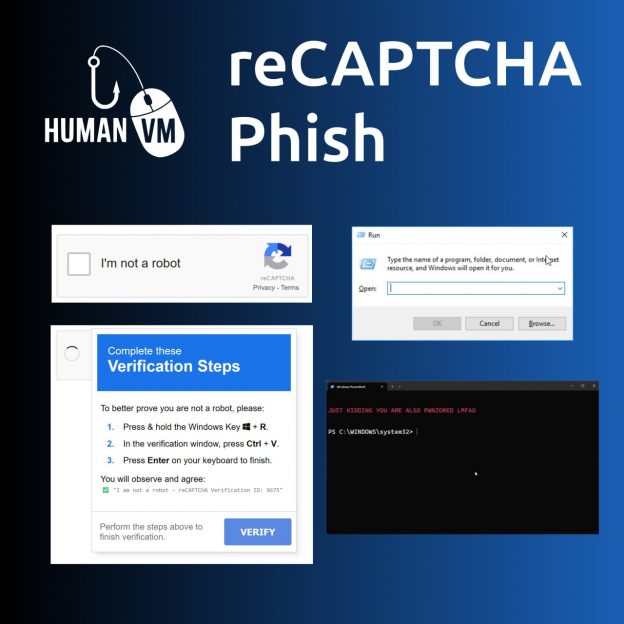
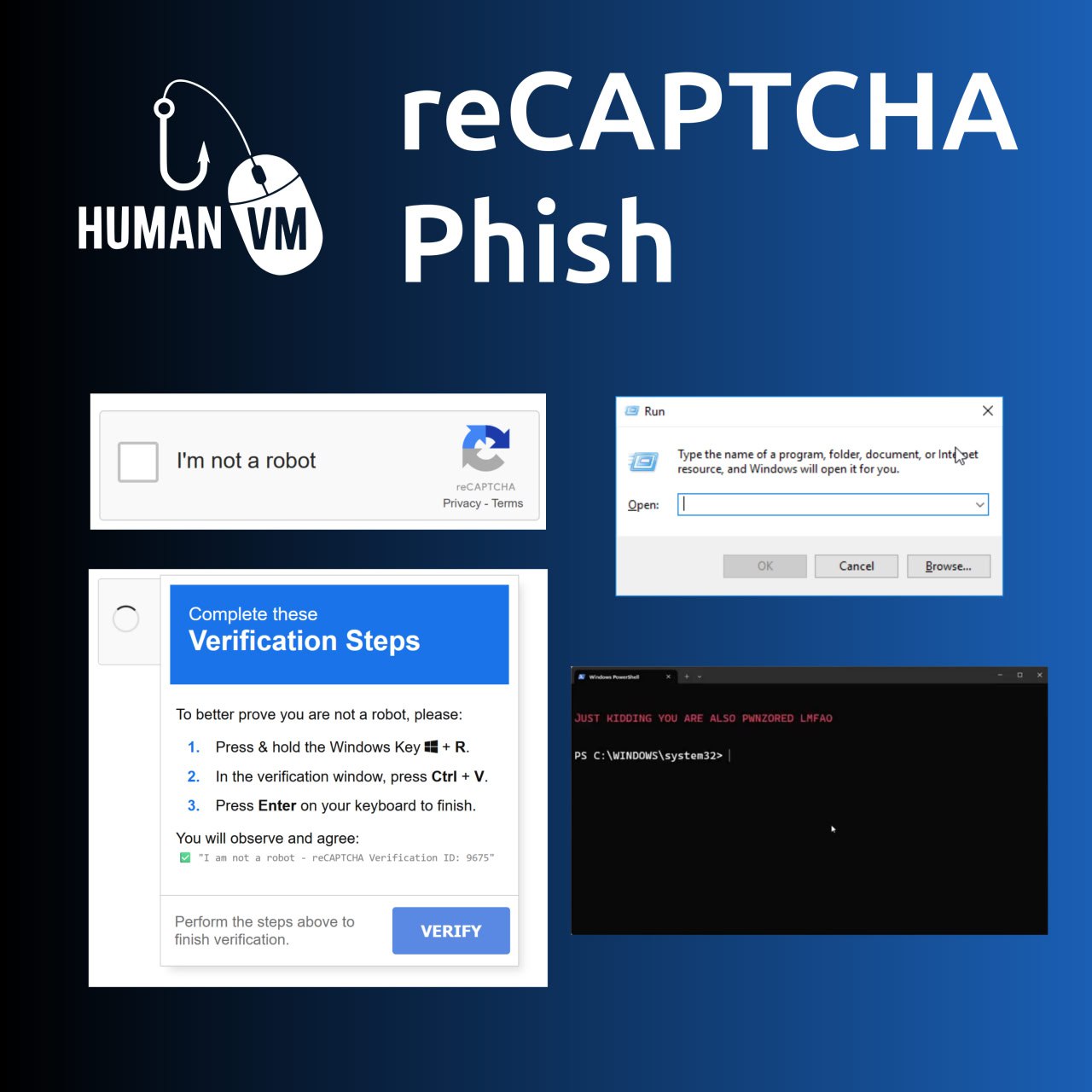
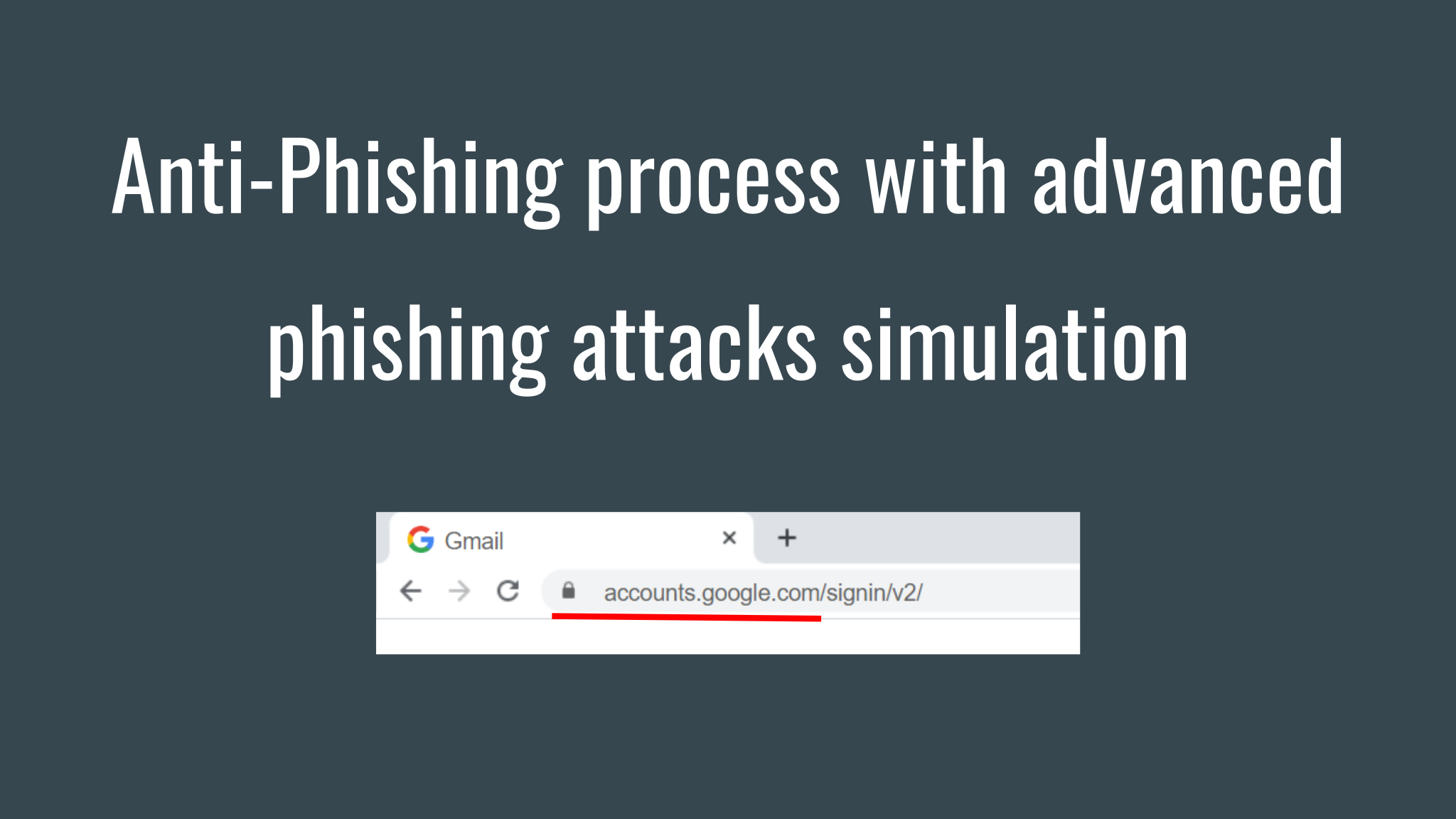
🔻 10:30 Human vulnerabilities: fake reCAPTCHA
🔻 11:45 Real world vulnerabilities: еxplosions of pagers and other electronic devices in Lebanon and the consequences for the whole world
🔻 14:42 Vulnerability management process practices: tie annual bonuses of IT specialists to meeting SLAs for eliminating vulnerabilities
🔻 16:03 Final and announcement of the contest
🔻 16:24 Backstage