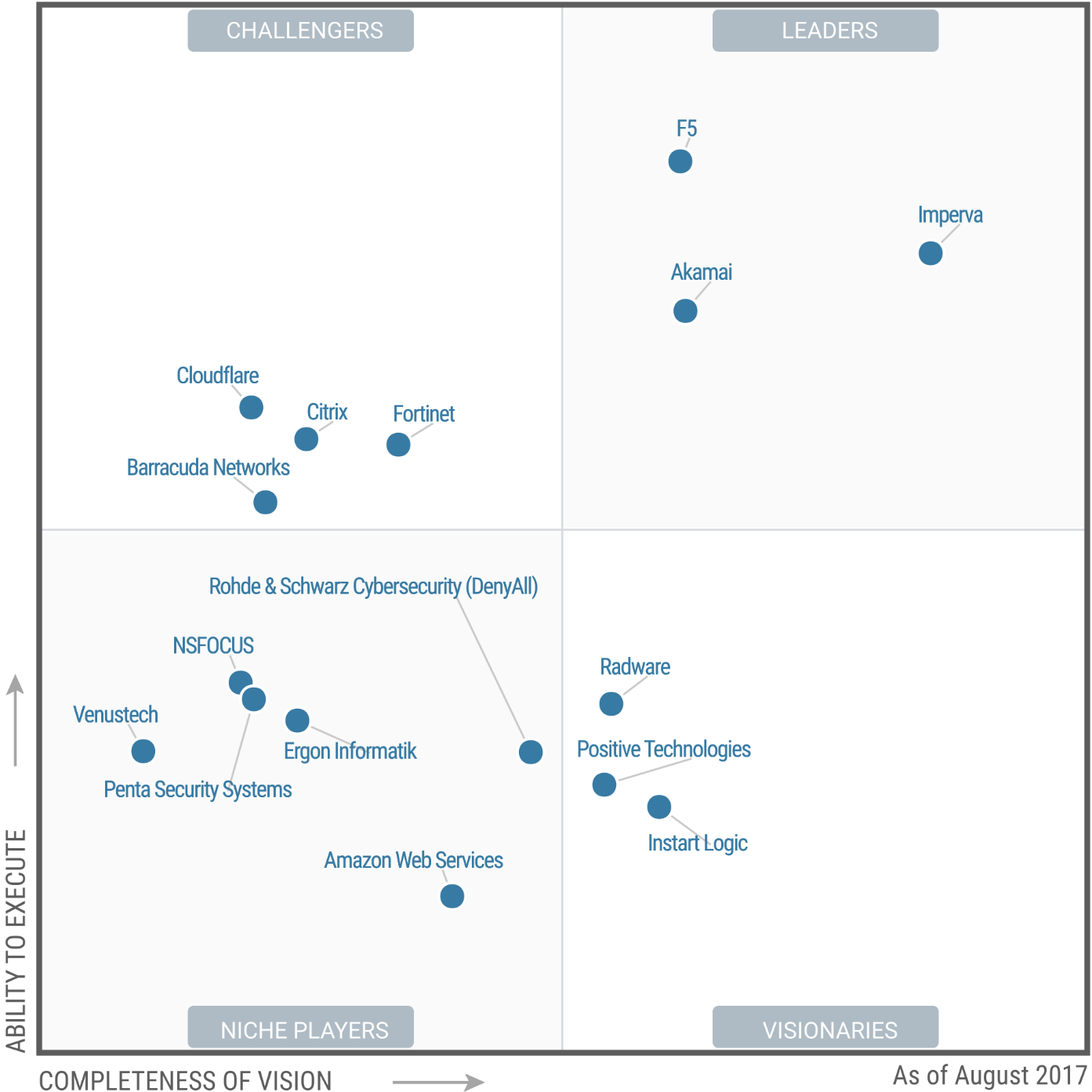
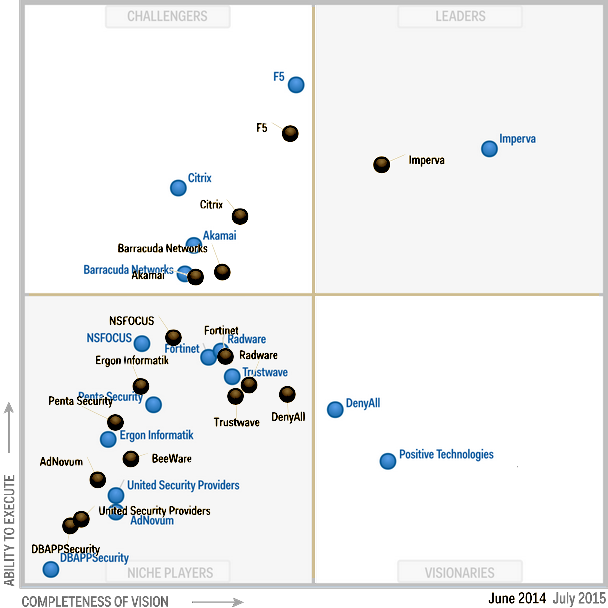
In this episode, I would like to share my thoughts about the new Vulnerability Management product by Positive Technologies – MaxPatrol VM. It was presented on November 16th, at the Standoff365 online conference (full video in Russian). The presentation and concept of the product were very good. I really liked them. However, as it always happens on vendor’s events, some critical topics were not covered. So I also want to highlight them. I will try to be as objective as possible. Although it is difficult for me, since I have worked in the company for 6 years, and many of my good friends work there.

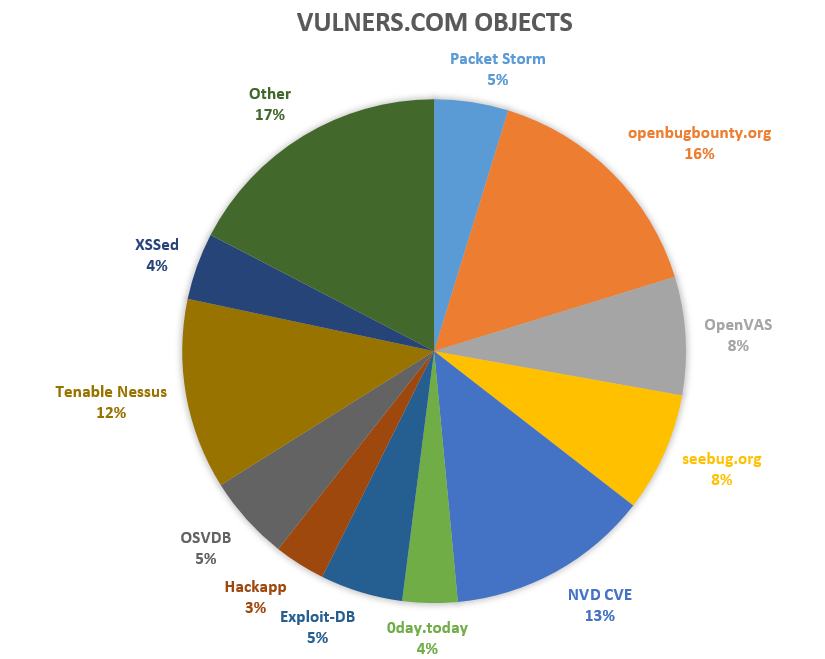
Positive Technologies is best known in the Russian Vulnerability Management market. The volume of the Russian VM market in 2019 is $40-46 million. The volume of the world market, according to IDC, is $1.2 billion. So the Russian market is ~3% of the world market. And 78% of it is occupied by Positive Technologies products: Maxpatrol 8 and XSpider. Disclaimer: all numbers are from the Maxpatrol VM presentation and I haven’t done fact checking. But in this case, the numbers are not so important.
Continue reading