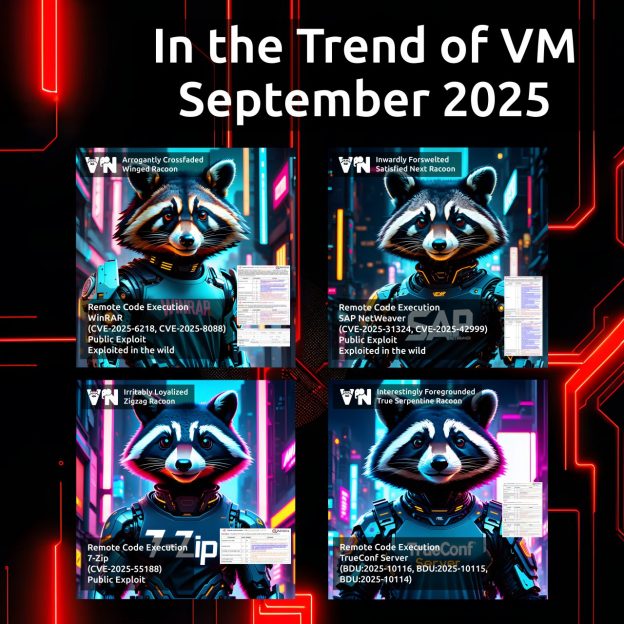
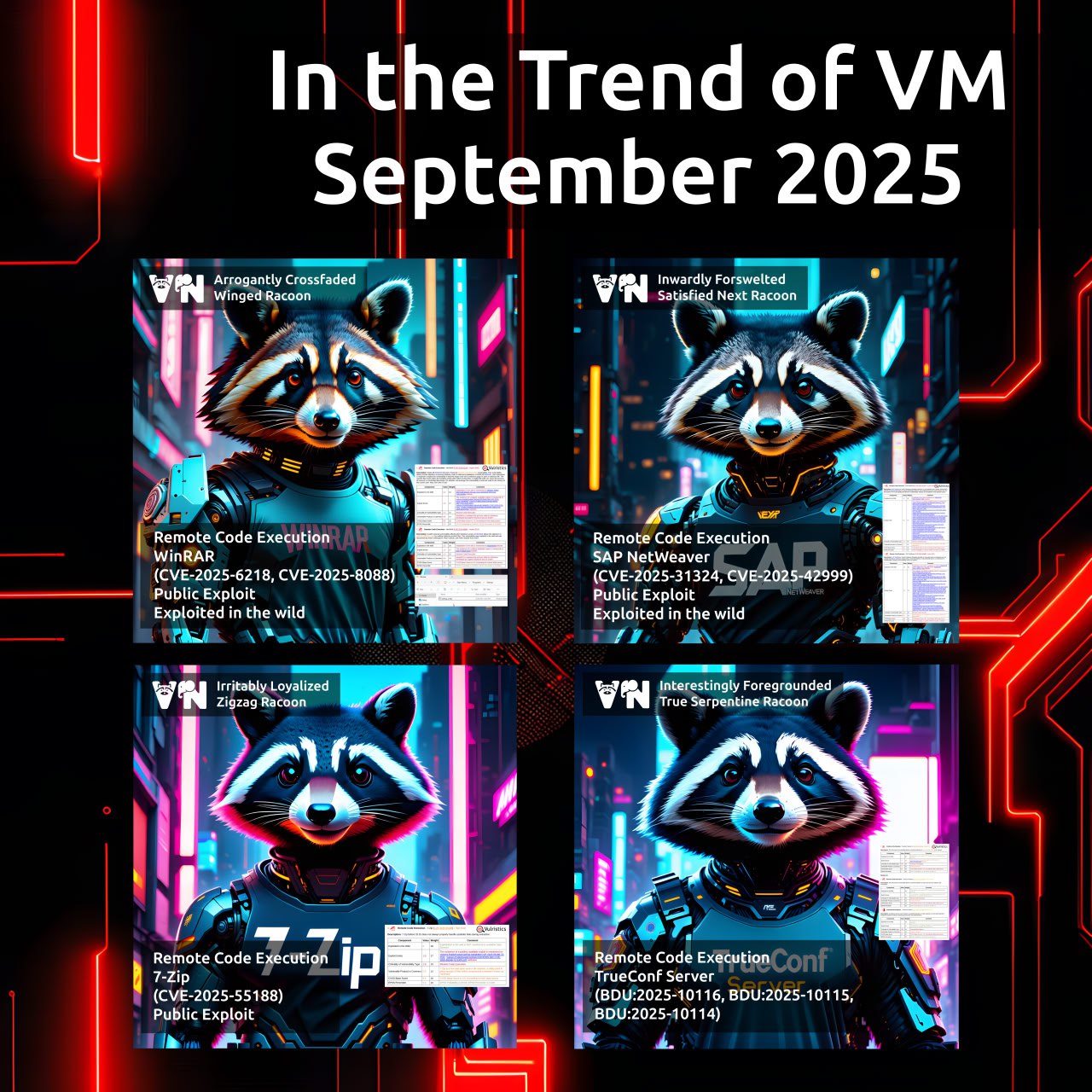
Statistics on 2024 trending vulnerabilities were featured in the OIC-CERT annual report. 🎉
🔹 The Organisation of Islamic Cooperation (OIC) is the largest and most influential official intergovernmental Muslim international organization. It currently unites 57 countries with a population of about 2 billion people. Russia is also a member of the OIC as an observer.
🔹 OIC-CERT is a computer incident response team and a subsidiary of the OIC. It brings together national CERTs from 27 countries, as well as 8 commercial organizations, including Positive Technologies.
➡️ The statistics on 2024 trending vulnerabilities that I prepared were published in the section highlighting Positive Technologies’ results (report size: 67.49 MB, p.229).
I’m glad my work contributed to promoting PT ESC and Positive Technologies among national CERTs and key decision-makers! 😉
На русском