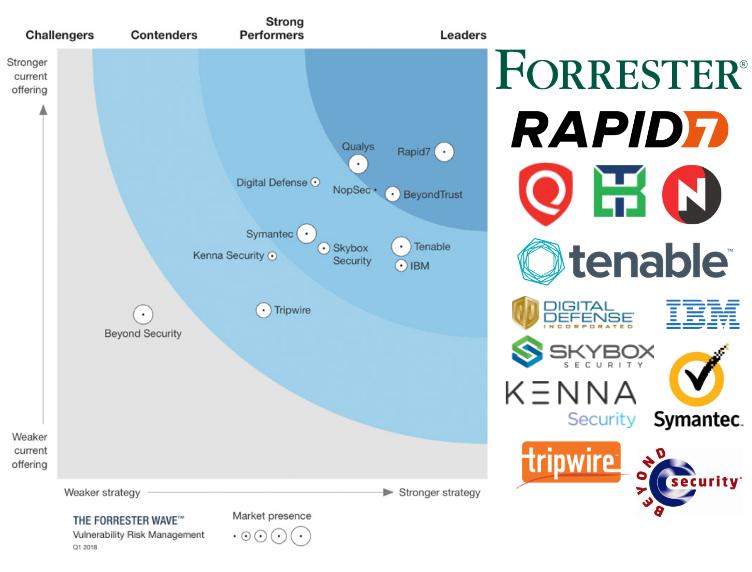
My thoughts on the “2021 Gartner Market Guide for Vulnerability Assessment”. What about the quality? The Gartner Vulnerability Management Reports are one of the few marketing reports that I try to read regularly. This started back in the days when I was working for a VM vendor doing competitive analysis. Gartner is one of the few organizations that think about Vulnerability Assessment and Vulnerability Management and clearly articulate where we are and where we are going.
I got a free reprint of “2021 Gartner Market Guide for Vulnerability Assessment” from the Tenable website. Thanks a lot to them for that.
Let’s start with what I liked:
- It’s great that Gartner has made vulnerability prioritization technology (VPT) a separate class of solutions, that do not detect vulnerabilities themselves, but work with them. For example, Kenna or my Vulristics. And it could be additional functionality like Tenable VPR.
- I liked the focus on EDR as a promising VM replacement. Especially, Microsoft solutions (Defender for Endpoint or as was mentioned in the report Microsoft’s Threat & Vulnerability Management, TVM).
- It’s nice that various areas related to Vulnerability Management have been mentioned: Pentest, Bug Bounty, Breach and Attack Simulation (BAS).
- An interesting diagram that shows that VA is primarily about “Assess” and “Asset Management”, VPT is primarily about “Prioritize” and “Workflow Management”, BAS is primarily about “Compensate” and “Security Controls”.
Now what I didn’t like. I have one pain point – the quality of the scanning. And here, on the one hand, something was said, but on the other, it was not enough and not as definite as I would like. Market Direction is the most interesting section of the document. And it was the most painful to read.