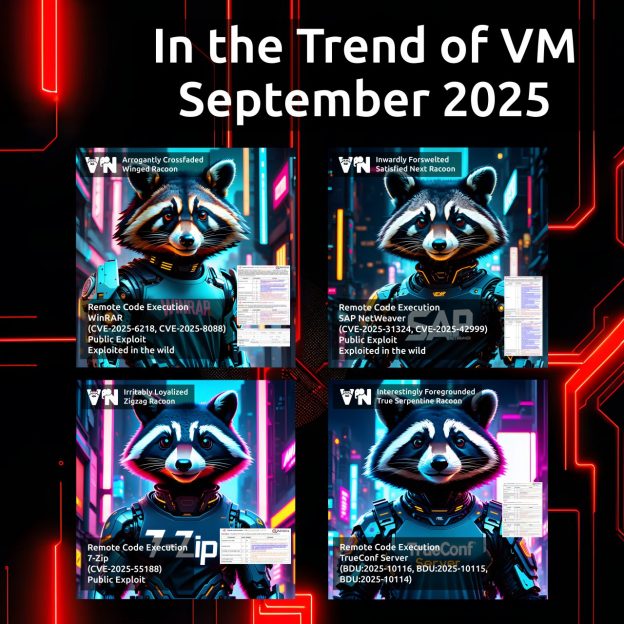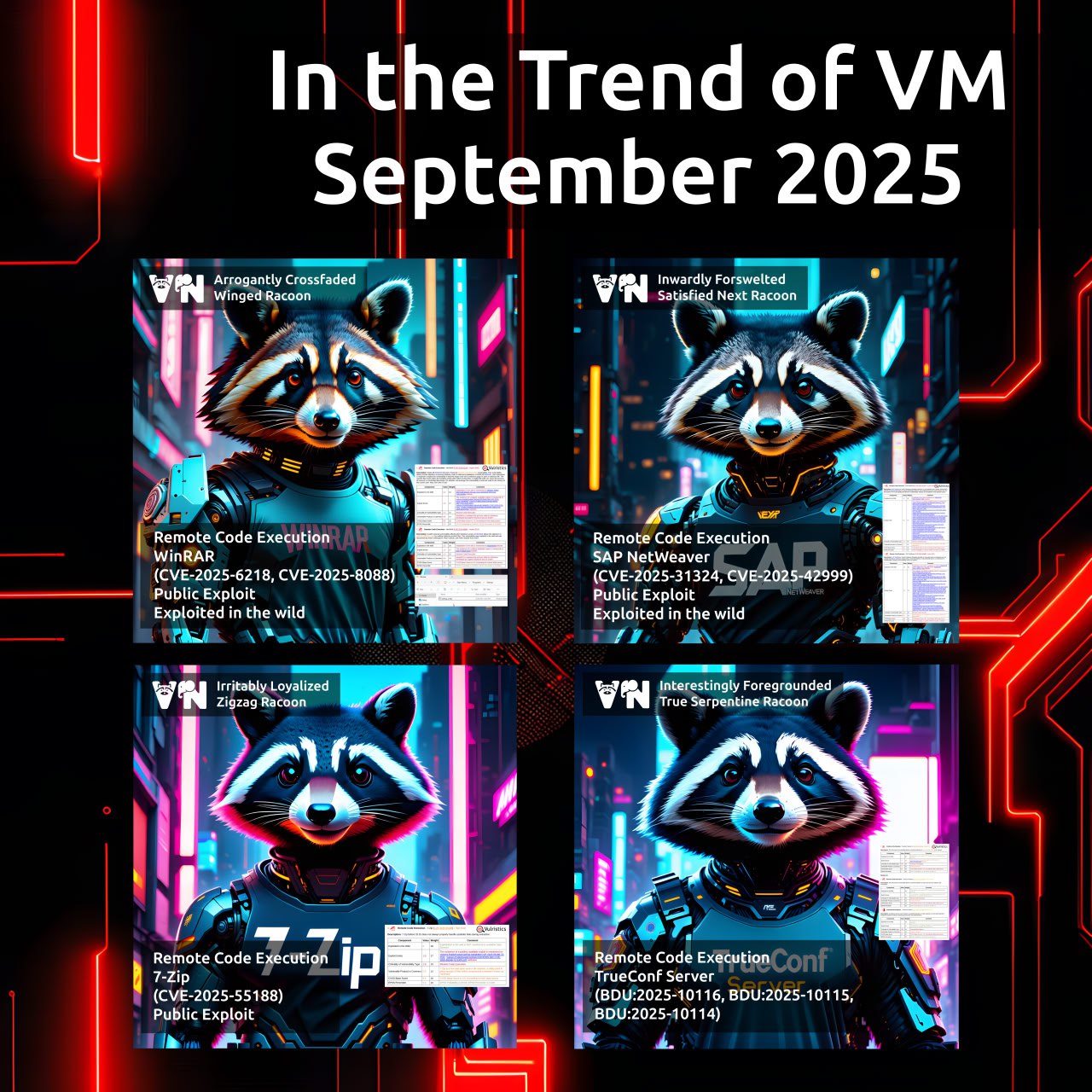
September “In the Trend of VM” (#19): vulnerabilities in the WinRAR and 7-Zip archivers, SAP NetWeaver, and TrueConf Server. A traditional monthly roundup – for the first time with NO Microsoft vulnerabilities! 😲🙂
🗞 Post on Habr (rus)
🗒 Digest on the PT website (rus)
A total of eight trending vulnerability IDs in four products:
🔻 Remote Code Execution – WinRAR (CVE-2025-6218, CVE-2025-8088). An exploitable RCE during archive extraction.
🔻 Remote Code Execution – SAP NetWeaver (CVE-2025-31324, CVE-2025-42999). An exploitable RCE in a component of a popular ERP system.
🔻 Remote Code Execution – 7-Zip (CVE-2025-55188). Mostly a Linux RCE during archive extraction – a public exploit is available.
🔻 Remote Code Execution – TrueConf Server (BDU:2025-10116, BDU:2025-10115, BDU:2025-10114). Critical flaws in Russian videoconferencing system.