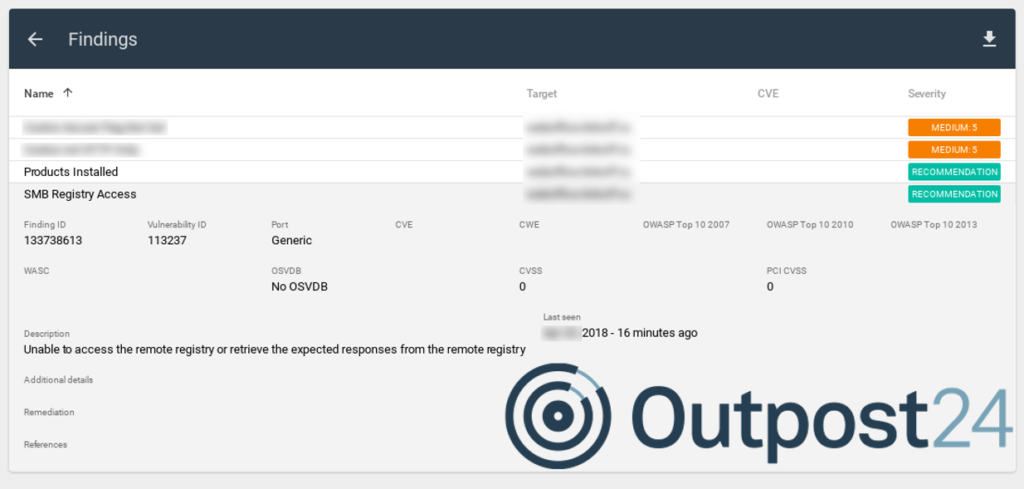
Free High-Tech Bridge ImmuniWeb Application Discovery service. Today I would like to talk about another service for application security analysis by High-Tech Bridge. It’s called ImmuniWeb Application Discovery.
This service can get information about your web and mobile applications available from the Internet. Believe me, this is not so obvious for a large organization. And, what is especially pleasant, it works automatically and free of charge. 😉
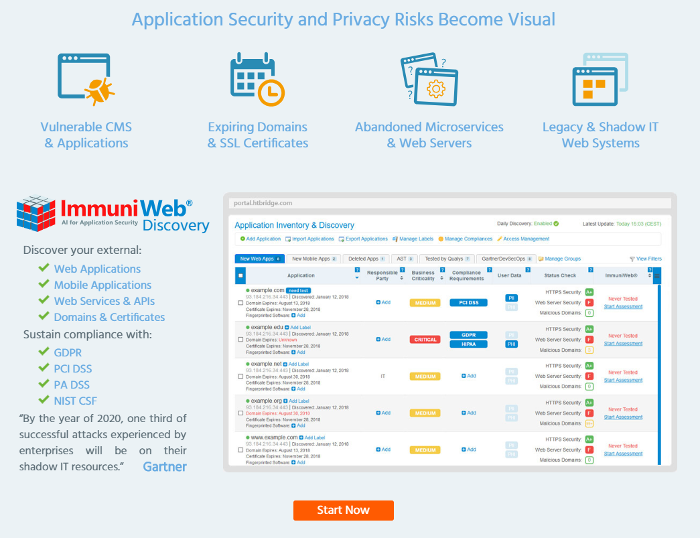
ImmuniWeb Application Discovery will also show the basic security problems with SSL connection, web-server headers, potential phishing issues for all founded web services. You can read more about this part in my posts about High-Tech Bridge services and APIs for SSL/TLS server testing and for searching cybersquatting, typosquatting and phishing domains.
From the same interface you can order an advanced audit of your web applications by High-Tech Bridge as well.