May “In the Trend of VM” (#15): vulnerabilities in Microsoft Windows and the Erlang/OTP framework. A traditional monthly vulnerability roundup. 🙂
🗞 Post on Habr (rus)
🗒 Digest on the PT website (rus)
A total of 4 trending vulnerabilities:
🔻 Elevation of Privilege – Windows Common Log File System Driver (CVE-2025-29824)
🔻 Elevation of Privilege – Windows Process Activation (CVE-2025-21204)
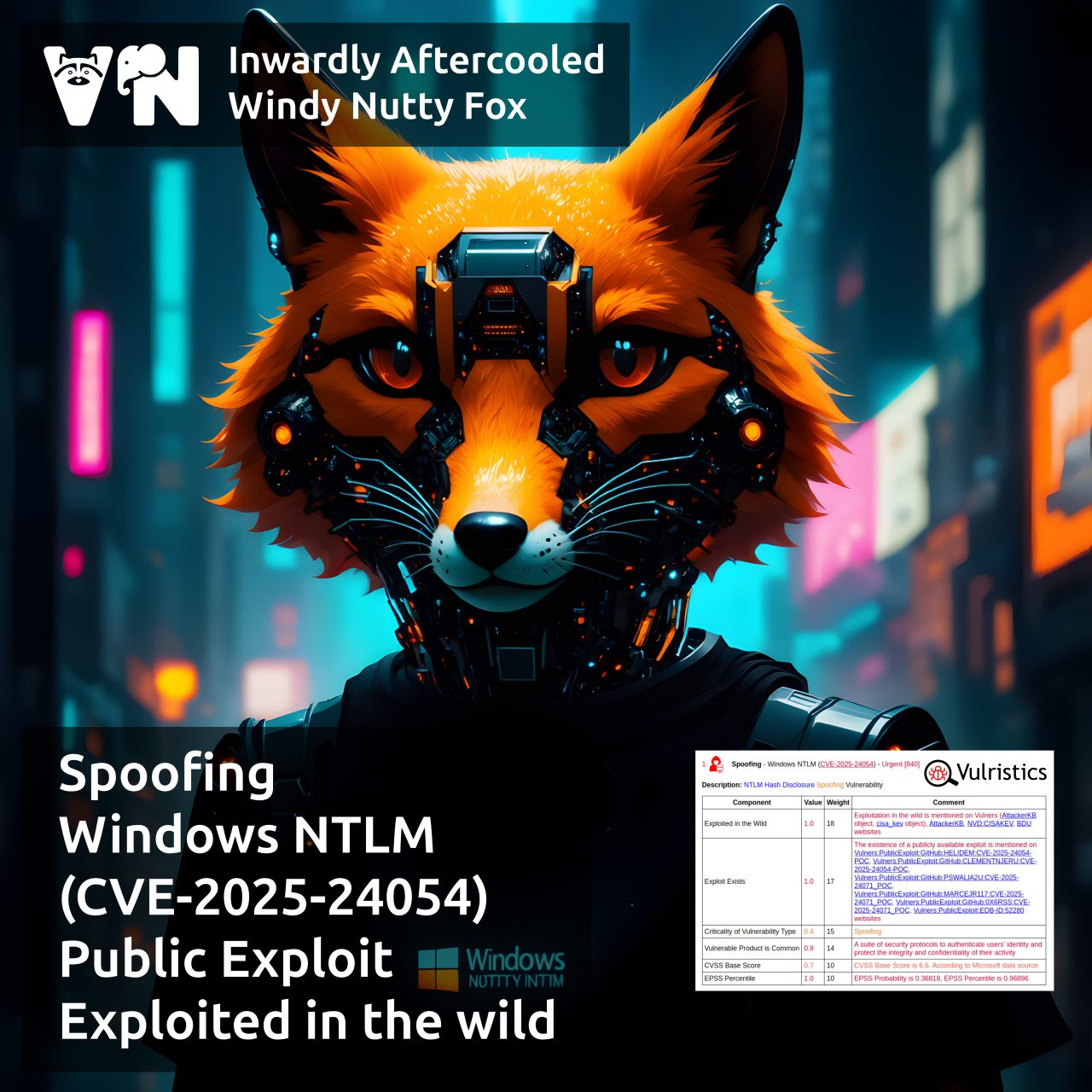
🔻 Spoofing – Windows NTLM (CVE-2025-24054)
🔻 Remote Code Execution – Erlang/OTP (CVE-2025-32433)